corbeaucrypto · @corbeaucrypto
140 followers · 325 posts · Server infosec.exchangeI have a diagramming question for the Infosec.Exchange/Mastodon hive mind. What diagramming tools and stencils do you use to create your dope-ass malware process diagrams? #InfoSec #Reporting #Malware #MalwareRE
#infosec #reporting #malware #malwarere
ericWadeFord · @ericWadeFord
0 followers · 2 posts · Server infosec.exchangeOneNote Attachment Used to Deliver New Variant of #BATLoader
Source: https://blog.cyble.com/2023/02/02/new-batloader-disseminates-rats-and-stealers/
Targeted Industries: Manufacturing, Retail Trade; Potential to target all industries
Cyble recently observed a #cybercriminal using a OneNote attachment (.one) in spam emails to deliver a .bat file that exhibits the same behavior as a new variant of #BATLoader. Deepwatch has observed cybercriminals using OneNote attachments to deliver #Qakbot #malwarere ATI's Cyber Threat Intel team cannot find any reference to BatLoader being sold or offered through publicly available sources, which may suggest that a single cybercriminal or group operates BATLoader; this may indicate that the cybercriminal behind the phishing campaign is the same cybercriminal behind BATLoader. Cybercriminals using OneNote attachments could be an emerging trend. However, as of yet, it appears to be an isolated usage and not a widespread threat and may indicate that cybercriminals are testing out this distribution method.
#batloader #cybercriminal #qakbot #malwarere #cti #threatintelligence #threatintel
Sajid Nawaz Khan · @snkhan
19 followers · 11 posts · Server infosec.exchangeOne of my favourite references on process injection techniques. The animations make this so much easier to understand — highly recommended!
Sajid Nawaz Khan · @snkhan
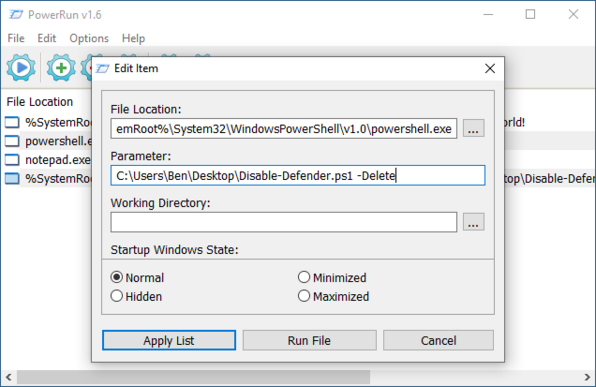
13 followers · 8 posts · Server infosec.exchangeStruggling to execute Red Canary's Atomic Red Team unit tests (or other malware) on a VM due to Windows Defender?
1. Download `disable-defender.ps1` from https://github.com/jeremybeaume/tools/blob/master/disable-defender.ps1
2. Download PowerRun from https://www.sordum.org/9416/powerrun-v1-6-run-with-highest-privileges/
3. Update the File Location within the PowerRun dialogue to powershell.exe.
4. Set the Parameter to the absolute path of `disable-defender.ps1`, optionally appending `-Delete`. Then Run File to execute the PowerShell script with TrustedInstaller privileges.
4. Restart the VM.
5. Continue with the installation instructions at https://github.com/redcanaryco/invoke-atomicredteam/wiki/Installing-Invoke-AtomicRedTeam#install-execution-framework-and-atomics-folder
#blueteam #purpleteam #malwarere