Jeffrey Goldberg · @jpgoldberg
1699 followers · 1041 posts · Server ioc.exchange@jedisct1, spaces in passwords have had this problem with just humans listening. (I don’t know of actual experiments, but my guess is that it would take just a few occurrences for a human listening to someone type their #password to learn where the spaces are in it.)
But now this goes well beyond that. And, as the article says, this is a #sideChannel with lots of opportunities to exploit without specialized gear.
IT News · @itnewsbot
3298 followers · 263498 posts · Server schleuss.onlineHackers can steal cryptographic keys by video-recording power LEDs 60 feet away - Enlarge / Left: a smart card reader processing the encryption key of an... - https://arstechnica.com/?p=1947319 #sidechannel #encryption #smartcards #features #biz&it
#biz #features #smartcards #encryption #sidechannel
Tech news from Canada · @TechNews
636 followers · 19073 posts · Server mastodon.roitsystems.caArs Technica: Hackers can steal cryptographic keys by video-recording power LEDs 60 feet away https://arstechnica.com/?p=1947319 #Tech #arstechnica #IT #Technology #sidechannel #encryption #smartcards #Features #Biz&IT
#Tech #arstechnica #it #technology #sidechannel #encryption #smartcards #features #biz
Markus Wamser · @wamserma
24 followers · 98 posts · Server hachyderm.ioProgram for the 23rd #COSADE Workshop is up: https://www.cosade.org/cosade23/program.html
Renaud Lifchitz :verified: · @nono2357
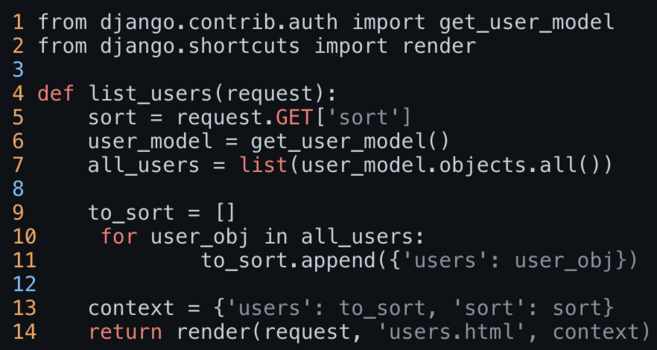
252 followers · 1128 posts · Server infosec.exchangeRT @0xor0ne
Interesting side channel attack against python Django framework by @DBrinkrolf (@SonarSource)
https://www.sonarsource.com/blog/disclosing-information-with-a-side-channel-in-django/
#sidechannel #infosec #cybersecurity
Patryk Krawaczyński · @agresor
42 followers · 142 posts · Server infosec.exchangeSpectre of the KAISER Meltdown ( https://nfsec.pl/security/6043 ) #linux #spectre #meltdown #security #sidechannel #kernel #attack #twittermigration
#linux #spectre #meltdown #security #sidechannel #kernel #attack #twittermigration
Tech News Worldwide · @TechNews
11292 followers · 97991 posts · Server aspiechattr.meBooks You Should Read: The Hardware Hacker’s Handbook
https://hackaday.com/2022/08/05/books-you-should-read-the-hardware-hackers-handbook/
#sidechannelanalysis #ReverseEngineering #hardwarehacking #powerglitching #Sidechannel #Featured #Interest #Reviews #Skills
#sidechannelanalysis #reverseengineering #hardwarehacking #powerglitching #sidechannel #Featured #Interest #Reviews #skills
(RTP):tor:Privacy & Tech Tips · @RTP
2616 followers · 3880 posts · Server fosstodon.orgMordechai Guri's SATAn Side Channel Attach Turns Harddrive SATA Cables Into A Transmitting Antenna
#Infosec #Cybersecurity #privacy #Israel #Tech #Radio #Sidechannel #SATA #antenna #Security #Data
https://hackaday.com/2022/07/22/satan-turns-hard-drive-cable-into-antenna-to-defeat-air-gapped-security/
#infosec #cybersecurity #privacy #israel #tech #radio #sidechannel #sata #antenna #security #data
vPierre · @vPierre
18 followers · 477 posts · Server mas.to(RTP):tor:Privacy & Tech Tips · @RTP
2618 followers · 3880 posts · Server fosstodon.orgBy monitoring power consumption on a device, researchers were able to compromise encryption process via side channel (attack).
#Infosec #Cybersecurity #Encryption #Crypto #Security #News #Research #Tech #SideChannel
https://thehackernews.com/2022/03/researchers-demonstrate-new-side.html
#infosec #cybersecurity #encryption #crypto #security #news #research #tech #sidechannel
(RTP):tor:Privacy & Tech Tips · @RTP
2619 followers · 3880 posts · Server fosstodon.orgTimeCache aims to use hardware + software to block side channel attacks. #Infosec #Cybersecurity #SideChannel #Security #Hardware #Software #Spectre #Meltdown
https://www.theregister.com/2021/06/15/timecache_aims_to_block_sidechannel/
#spectre #meltdown #infosec #cybersecurity #sidechannel #security #hardware #software
Julien M. · @julm
485 followers · 4935 posts · Server framapiaf.org#CyberSecurity
> Prime+Probe 1, #JavaScript 0: Overcoming #Browser-based #SideChannel Defenses
> first browser-based side-channel #attack which is constructed entirely from Cascading Style Sheets (#CSS) and #HTML, and works even when script execution is completely blocked.
https://arxiv.org/abs/2103.04952
#html #css #attack #sidechannel #browser #javascript #cybersecurity
Julien M. · @julm
485 followers · 4935 posts · Server framapiaf.org« The Sound of Silence: #Mining Security Vulnerabilities from Secret Integration Channels in #OpenSource Projects »
« #Linux #kernel #security fixes spotted before release with #SideChannel attack on...developer mailing lists »
« For these #vulnerabilities, our approach provides a temporal advantage of 2 to 179 days to design #exploits before public #disclosure takes place, and fixes are rolled out. »
https://www.theregister.com/2020/09/04/linux_kernel_flaws/
https://arxiv.org/pdf/2009.01694.pdf
#disclosure #exploits #vulnerabilities #sidechannel #security #kernel #linux #opensource #mining