Beth Pariseau · @BPariseau
295 followers · 94 posts · Server hachyderm.io#3cxpocalypse, like the #LastPass breach, was facilitated in part by vulnerable software downloaded to an employee's home computer, which then had access to company systems. Securing remote access an increasingly hot topic: https://www.techtarget.com/searchitoperations/news/365534899/Securing-remote-access-grows-crucial-for-DevSecOps
Ultraviolet · @VioletSullivan
40 followers · 66 posts · Server risk.socialLooks like #3cxpocalypse MAY actually be #3cx rainstorm … with much less damage than expected.
“Kaspersky has now found that the #hackers combed through the victims infected with its corrupted software to ultimately target fewer than 10 machines—at least as far as @Kaspersky could observe so far—and that they seemed to be focusing on #cryptocurrency firms with “surgical precision.””
https://www.wired.com/story/3cx-supply-chain-attack-north-korea-cryptocurrency-targets/
#3cxpocalypse #3cx #hackers #cryptocurrency
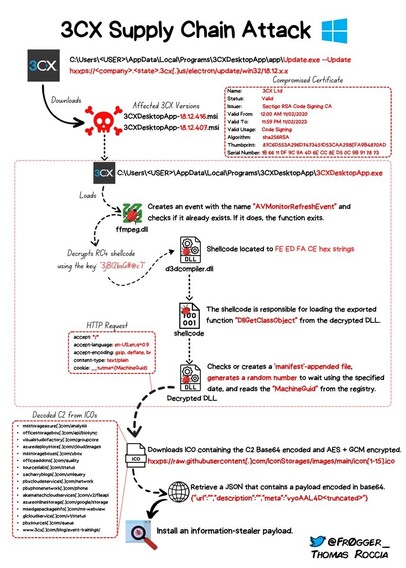
Edu Minguez 🐧 · @minWi
161 followers · 372 posts · Server tty0.socialRT @fr0gger_
🔍If you are looking for a comprehensive overview of the current #3CX supply chain attack, I created a diagram that shows the attack flow!💥I'll update as soon as the analysis progresses. Stay tuned for the MacOS edition! #cybersecurity #infosec #supplychainattack #3CXpocalypse
#3cx #cybersecurity #infosec #supplychainattack #3cxpocalypse
The Hacker News · @hackernews_bot
2274 followers · 1319 posts · Server social.platypush.techOriginally posted by The Hacker News / @TheHackersNews: http://nitter.platypush.tech/TheHackersNews/status/1641737567715438592#m
R to @TheHackersNews: The attack appears to have compromised 3CX's software build pipeline to distribute Windows and #macOS versions of the app package or poisoned an upstream dependency. The scale of the attack is currently unknown. 🔎
#macos #cybersecurity #3cx #3cxpocalypse #3cxdesktopapp