philpem · @philpem
519 followers · 2174 posts · Server digipres.clubAnd now, #BSBACM round two! This board has a GAL16V8 which decodes the dual RAM selects into a single select. Unfortunately I've cocked up, can you spot my mistake?
#hacktv #ReverseEngineering
#reverseengineering #HackTV #BSBACM
philpem · @philpem
519 followers · 2174 posts · Server digipres.clubThis is what a half assembled #BSBACM RAM dumper looks like. Needs a 4-pin header, another seven Roadrunner wires, the GAL socket flipping 180 degrees, and a bit of GAL programming. #reverseengineering #hacktv
#HackTV #reverseengineering #BSBACM
philpem · @philpem
519 followers · 2174 posts · Server digipres.clubI'm going to have a rethink about the #BSBACM RAM dump attempt. I've found a pair of Harwin transition headers, and I think I can use them and some IDC cable to connect to the ROM socket.
With a bit of luck, pad board with Roadrunner wire should have better SI than Veroboard, and I can make up a "sniffer" to read out the RAM - or at least the bits which are being accessed. #ReverseEngineering
philpem · @philpem
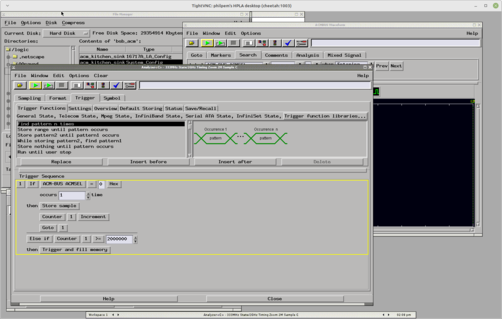
519 followers · 2174 posts · Server digipres.clubI'm surprised nobody has commented on how my HP16700 config for sniffing the #BSBACM RAM and host bus is called "kitchen sink".
philpem · @philpem
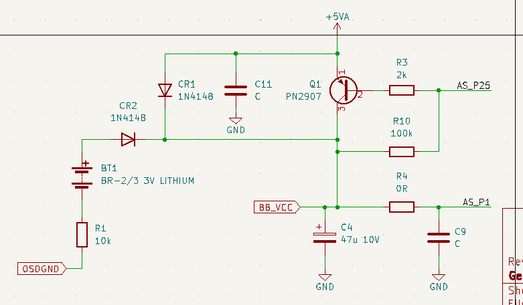
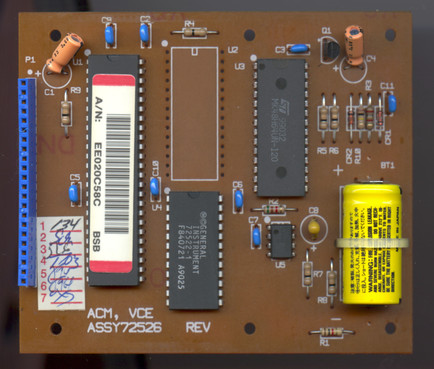
519 followers · 2174 posts · Server digipres.clubMore analysis on the #BSBACM battery-backup circuit!
BB_VCC powers a Mostek MK48H64UN SRAM - it's 3V less CR2's voltage drop with no VCC, or 5V less about 0.2V with VCC present.
Q1 is there because the MK48H64 can draw up to 100mA when active. A 1N4148 diode would drop over a volt in those conditions.
But Q1 is driven into saturation with 2.5mA base current, so according to fig.4 of the 2N2907 datasheet (https://global.oup.com/us/companion.websites/fdscontent/uscompanion/us/pdf/microcircuits/students/bjt/2N2907-motorola.pdf), BB_VCC would be around 4.85V with a 100mA load.
philpem · @philpem
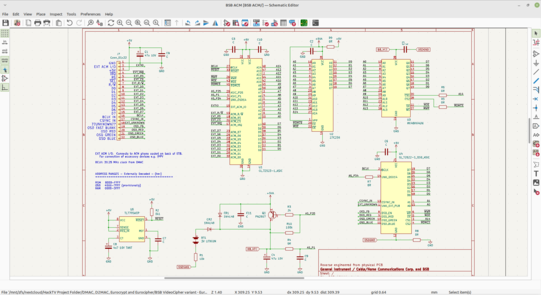
519 followers · 2174 posts · Server digipres.clubLook, what's this? A shiny new #BSBACM schematic, with corrected chip selects!
Shame the battery back-up circuit still doesn't make much sense. AS_P1 and AS_P25 go to the ASIC. But I'm still puzzled why Q1 is there, when CR1 bypasses it?
AS_P25 low would make Q1 bypass CR1, but the Vce(sat) of Q1 is higher than the Vf of CR1, so it's doing... nothing?
#ReverseEngineering #HackTV
#HackTV #reverseengineering #BSBACM
philpem · @philpem
519 followers · 2174 posts · Server digipres.clubContinuing with the #BSBACM #ReverseEngineering project tonight, for #HackTV. ICYMI, the previous thread is here: https://digipres.club/@philpem/109734418887706727
#HackTV #reverseengineering #BSBACM
philpem · @philpem
519 followers · 2174 posts · Server digipres.clubphilpem · @philpem
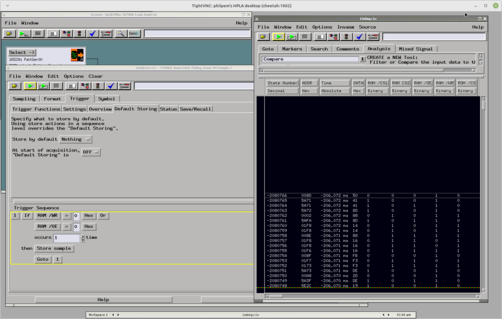
519 followers · 2174 posts · Server digipres.clubFirst logic analyser capture. #BSBACM.
What we've learned here is, the RAM Output Enable isn't qualified with the address decode. I'll have to take a closer look at that, it may be an inverted version of the 6502 R/!W, possibly gated with phi2.
philpem · @philpem
519 followers · 2174 posts · Server digipres.clubphilpem · @philpem
519 followers · 2174 posts · Server digipres.clubSeeing as @captainjack asked so nicely I'm going to show y'all how we do a live RAM dump on a 6502-based computer module: specifically the BSB Eurocypher Access Control Module (ACM). #BSBACM #BSB #HackTV
There are two known ROM versions: V1.20 and V1.50. Software upgrading/patching seems to be a thing too, as V1.20 units I've seem claim to be "V1.20 V1.50".
The first photo is the ACM, the second is the diagnostic screen.