Joxean Koret (@matalaz) · @joxean
1057 followers · 11007 posts · Server mastodon.socialRT @_ringzer0@twitter.com
New to using #Diaphora, an #IDA #Python BinDiffing Plugin? Check out this tutorial by @matalaz@twitter.com on how to use Diaphora for program #diffing. https://bit.ly/diaphora
Wanna learn more? Advance your #reversing skills by enrolling in his class at #CATCH2022 🎉 https://ringzer0.training/binary-diffing-with-diaphora.html
🐦🔗: https://twitter.com/_ringzer0/status/1483795643458064387
#Diaphora #python #diffing #CATCH2022 #ida #reversing
Joxean Koret (@matalaz) · @joxean
1434 followers · 11891 posts · Server mastodon.socialRT @_ringzer0@twitter.com
New to using #Diaphora, an #IDA #Python BinDiffing Plugin? Check out this tutorial by @matalaz@twitter.com on how to use Diaphora for program #diffing. https://bit.ly/diaphora
Wanna learn more? Advance your #reversing skills by enrolling in his class at #CATCH2022 🎉 https://ringzer0.training/binary-diffing-with-diaphora.html
🐦🔗: https://twitter.com/_ringzer0/status/1483795643458064387
#Diaphora #python #diffing #CATCH2022 #ida #reversing
Joxean Koret (@matalaz) · @joxean
1057 followers · 11007 posts · Server mastodon.socialRT @_ringzer0@twitter.com
Watch @arnaugamez@twitter.com at #HITB give an overview of modern code deobfuscation techniques, their limitations, and how to handle them. https://www.youtube.com/watch?v=tYqXStZv1W4
Want to learn more about modern binary deobfuscation? Register for his class at #CATCH2022 Feb 19-25 ⚡ https://ringzer0.training/modern-binary-deobfuscation.html
🐦🔗: https://twitter.com/_ringzer0/status/1481258924674326538
Joxean Koret (@matalaz) · @joxean
1434 followers · 11891 posts · Server mastodon.socialRT @_ringzer0@twitter.com
Watch @arnaugamez@twitter.com at #HITB give an overview of modern code deobfuscation techniques, their limitations, and how to handle them. https://www.youtube.com/watch?v=tYqXStZv1W4
Want to learn more about modern binary deobfuscation? Register for his class at #CATCH2022 Feb 19-25 ⚡ https://ringzer0.training/modern-binary-deobfuscation.html
🐦🔗: https://twitter.com/_ringzer0/status/1481258924674326538
Joxean Koret (@matalaz) · @joxean
1057 followers · 11007 posts · Server mastodon.socialRT @_ringzer0@twitter.com
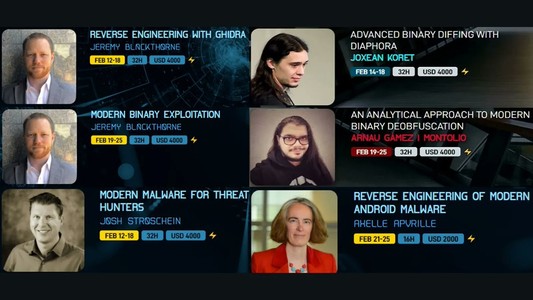
Elevate your binary analysis skills at #CATCH2022 ⚡ https://ringzer0.training/
✅ Reverse & exploit modern binaries: @0xJeremy@twitter.com
✅ Defeat obfuscated code: @arnaugamez@twitter.com
✅ Reverse #Android malware: @cryptax@twitter.com
✅ Master binary diffing: @matalaz@twitter.com
✅ Analyze #malware operations: @jstrosch@twitter.com
🐦🔗: https://twitter.com/_ringzer0/status/1465676246524829696
Joxean Koret (@matalaz) · @joxean
1434 followers · 11891 posts · Server mastodon.socialRT @_ringzer0@twitter.com
Elevate your binary analysis skills at #CATCH2022 ⚡ https://ringzer0.training/
✅ Reverse & exploit modern binaries: @0xJeremy@twitter.com
✅ Defeat obfuscated code: @arnaugamez@twitter.com
✅ Reverse #Android malware: @cryptax@twitter.com
✅ Master binary diffing: @matalaz@twitter.com
✅ Analyze #malware operations: @jstrosch@twitter.com
🐦🔗: https://twitter.com/_ringzer0/status/1465676246524829696
Joxean Koret (@matalaz) · @joxean
1057 followers · 11007 posts · Server mastodon.socialRT @_ringzer0@twitter.com
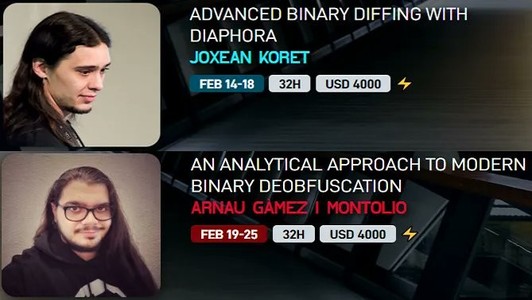
Curious about binary diffing or deobfuscation? At #CATCH2022, learn how to use #Diaphora to perform program #diffing with @matalaz@twitter.com and modern deobfuscation techniques to defeat obfuscated code with @arnaugamez@twitter.com. Enroll now ⚡ https://ringzer0.training/
🐦🔗: https://twitter.com/_ringzer0/status/1458428491167326214
Joxean Koret (@matalaz) · @joxean
1434 followers · 11891 posts · Server mastodon.socialRT @_ringzer0@twitter.com
Curious about binary diffing or deobfuscation? At #CATCH2022, learn how to use #Diaphora to perform program #diffing with @matalaz@twitter.com and modern deobfuscation techniques to defeat obfuscated code with @arnaugamez@twitter.com. Enroll now ⚡ https://ringzer0.training/
🐦🔗: https://twitter.com/_ringzer0/status/1458428491167326214