Blataak · @blataak
547 followers · 395 posts · Server mastodonczech.czTip na čtení!
Věděli jste, že Fred Astaire měl starší sestru, která byla zářivější a talentovanější? Že po ní toužili chlapci po celé Evropě? Jenže ona chtěla žít podle sebe.
Ženský byly a jsou silný v každý době. A málo se to ví. Životopisný romány jsou moje srdcovka.
#tipnacteni #tipnaknihu #čti
SarlackLab · @SarlackLab
32 followers · 201 posts · Server ioc.exchangeCommand-and-control IPv4 map, 2023-07-14 to 2023-07-27 #CTI
https://abjuri5t.github.io/SarlackLab/
103.234.72[.]0/24
45.9.74[.]0/24
91.103.252[.]0/24
77.91.68[.]0/24
193.233.133[.]0/24
45.12.253[.]0/24
87.121.47[.]0/24
2.59.255[.]0/24
79.110.49[.]0/24
141.98.6[.]0/24
v01ition · @v01ition
8 followers · 52 posts · Server ioc.exchangeAnyone have any good literature on Cyber Security being used by insurgencies and counter-insurgency agencies? #cybersecurity #informationsecurity #cyberthreatintelligence #CTI
#cybersecurity #informationsecurity #cyberthreatintelligence #CTI
SarlackLab · @SarlackLab
21 followers · 155 posts · Server ioc.exchangeCommand-and-control domain tree, 2023-06-09 to 2023-06-22 #CTI
https://abjuri5t.github.io/SarlackLab/
*.gz[.]apigw[.]tencentcs[.]com
*.sh[.]apigw[.]tencentcs[.]com
*.z01[.]azurefd[.]net
*.bj[.]apigw[.]tencentcs[.]com
*.com[.]s3[.]bucket-amazon[.]com
*.cloudapp[.]azure[.]com
Bongoknight · @bongoknight
81 followers · 37 posts · Server ioc.exchangeHere is my take on the intelligence lifecycle. I hope some of you could relate! #cti #ThreatIntel
Bongoknight · @bongoknight
75 followers · 32 posts · Server ioc.exchangeIf anyone in my network hears of a #ThreatIntel or #OSINT job in France (or remotely compatible), I will be happy to join the adventure and apply.
I have worked for a bank in phishing and brand impersonation detection. Then for a defence group, writing security specifications for radio equipment. Now I've been a threat analyst for 4 years, 3 at the French MoD and one at Vade. I've mainly worked on infrastructure/actor detection in a wild range of subjects from state actors to affiliate marketers and some influence campaigns.
I love learning new things, automating boring stuff, tinkering with some github repositories, OSINT-ing and digging through data to extract meaning and ultimately some #CTI.
#threatintel #osint #CTI #fedihired #infosecjobs
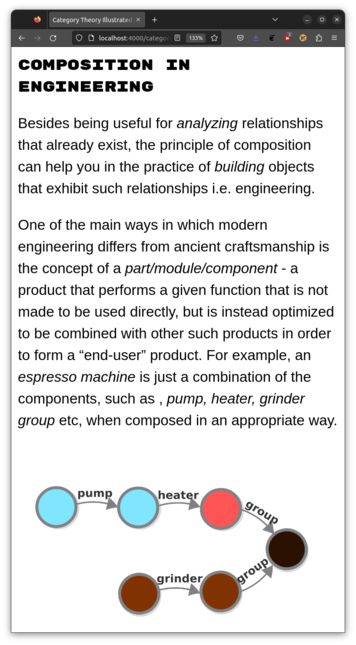
Jencel Panic · @abuseofnotation
316 followers · 499 posts · Server mathstodon.xyzToday I updated the first chapter of #CTI abuseofnotation.github.io/category-theory-illustrated/01_set/
Besides some minor corrections, I added a new section "Composition in engineering" and I wrote a little essay about programming at the end.
#mathematics #categorytheory #iamwriting #CTI
v01ition · @v01ition
8 followers · 48 posts · Server ioc.exchangeJust finished influence of sea power. Any #CTI or #intelligence analysts have recommendations for what to read next? Really on a strategy kick right now
Bongoknight · @bongoknight
73 followers · 28 posts · Server ioc.exchangehttps://twitter.com/packetwatch/status/1663644517986349056?s=20
A detection of QBot which seems interessting, I don't think that the ZIP → JS infection chain is common for this TA.
WACOCA · @wacoca
32 followers · 7676 posts · Server mastodon.cloudjohnchiment · @johnchiment
20 followers · 109 posts · Server ioc.exchange#CTI #ThreatIntelligence #newword
snafoolery: the seemingly active implementations and support for processes that are broadly recognized to be ineffective and broken beyond our ability to fix but are continually renewed.
Don't know if this is a word (and perhaps it should be spelled SNAFUlery?) but I intend to start using it.
#CTI #threatintelligence #newword
v01ition · @v01ition
8 followers · 45 posts · Server ioc.exchangeSarlackLab · @SarlackLab
10 followers · 45 posts · Server ioc.exchangeCommand-and-control IPv4 map, 2023-03-18 to 2023-03-31 #CTI
https://abjuri5t.github.io/SarlackLab/
94.142.138[.]0/24
45.15.156[.]0/24
46.161.27[.]160/28
45.9.74[.]0/24
37.220.87[.]0/24
83.217.11[.]0/24
45.227.255[.]192/26
185.106.92[.]0/24
77.73.134[.]0/24
195.133.40[.]0/24
Bongoknight · @bongoknight
70 followers · 31 posts · Server ioc.exchangeBongoknight · @bongoknight
70 followers · 30 posts · Server ioc.exchangeIt feels like there are some big #scam networks, which are so few documented. I'm always stunned by such things. #cti
Nice work! ;)
@rmceoin 🔗 https://infosec.exchange/users/rmceoin/statuses/110017723480010219
-
Here's a list of 8,213 domains using the Adsterra network. These were found by looking for atOptions at https://publicwww.com/websites/atOptions/.
https://gist.github.com/rmceoin/0e5ea6d21dbddd9bfe1318ce58a45ff3
All of them were at least live in the last few days I've been gathering the intel.
Most all of the ones I've sampled trigger to a malicious destination. In order for me to get them to do so I jump on mobile so as to get a fresh consumer IP. Otherwise they tend not to pop.
The video here is meant to demonstrate if a user had managed to get any of these four sites as a result in a search query.
Some of the sites have a common theme and I feel like maybe they've been spun up by a TA. Others look potentially legit and are either caught up in the malvertising or they're hacked and the malvertisement was placed on their page. Attribution is not an easy task.
Bongoknight · @bongoknight
65 followers · 27 posts · Server ioc.exchangehttps://blog.sevagas.com/?RedTeam-With-OneNote
A clear overview of how OneNote file format could be leveraged. Interresting in the actual phishing/malware landscape.
The site contains another cool article about Pub files.
Shoutout to : @EmericNasi
Bongoknight · @bongoknight
65 followers · 27 posts · Server ioc.exchangehttps://blog.sevagas.com/?RedTeam-With-OneNote
A clear overview of how OneNote file format could be leveraged.
The site contains another cool article about Pub files.
Håkon O. · @eselet
221 followers · 426 posts · Server snabelen.nonull - Open Security Community · @null0x00
146 followers · 246 posts · Server ioc.exchangeRT @avkashk
Our first talk of the day is live at Null Mumbai.
Career in CTI by @sandmaxprime
@NullMumbai @Snypter @chiragsavla94 @null0x00
#null #nullmumbai #cti #mumbai #meetup #infosec #cybersecurity
#null #nullmumbai #CTI #mumbai #meetup #infosec #cybersecurity
Bongoknight · @bongoknight
56 followers · 64 posts · Server ioc.exchangeThis week I made a project I want for a long time. It's a parser for recognizable data (IP, domain, phone, emails...). Custom actions are then linked to these datatype, one action can handle several types.
Here is a TUI made for this parser, it parses clipboard and allow to run customs actions :
- Extract URL and open them,
- Stats on duplicate lines,
- Informations on IP addresses,
- Format CSV or TSV data to a Markdown Table to include it inside a report,
Terminal is always up, as a front windows, so it make boring redundant searching actions painless.
I can instantly extract IoC from a security report, make some stats and check if I already know something about the observables I have.
I plan to add support for OpenCTI and MISP API soon.
Datatypes and actions are fully customizable.