Dick Smiths Fair Go Supporters · @dsfgs
178 followers · 12401 posts · Server activism.openworlds.infoWe had a chance to delve a bit, and the 'nmcli' command seems like a way to examine #MACAddresses.
So that's half the trick, but it looks like this distro or driver or network adaptor, we are working with atm, doesn't reset the #MACAddress…
#MACaddresses #macaddress #nmcli
(RTP):tor:Privacy & Tech Tips · @RTP
2618 followers · 3880 posts · Server fosstodon.orgMost mac randomization routines use invalid OUI's (making a small perm leak more trackable) and/or predictable mac generation (ie: Android/Apple) by OUI precept (trackers cross these out hence wipri valid OUI only).
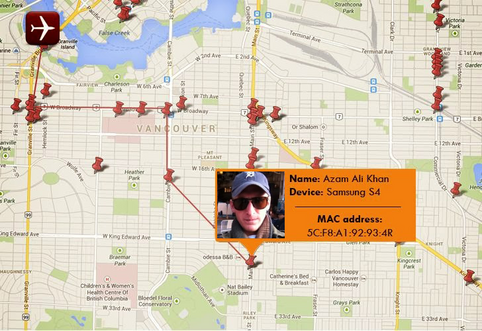
Websites like this for example, allow for the public to search cell phone wifi #MACaddresses for their logged location history: #privacy
And many tracking companies including Israeli specialize in tracking WiFi mac/bluetooth. Sharing in cloud fashion.