🖱🛠👉👕👈 SOSOrdinet 🎣🖥️🐛 🗞️ · @SOSOrdinet
15 followers · 845 posts · Server social.targaryen.house#PrintNightmare : l’impression insécuritaire perdure, malgré les récents patchs de #Microsoft !
#securite #ransomware #Magniber #patchtuesday #miseajour #PoC
#PrintNightmare #microsoft #securite #ransomware #Magniber #patchtuesday #miseajour #poc
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
627 followers · 27846 posts · Server mastodon.socialRT @gentilkiwi
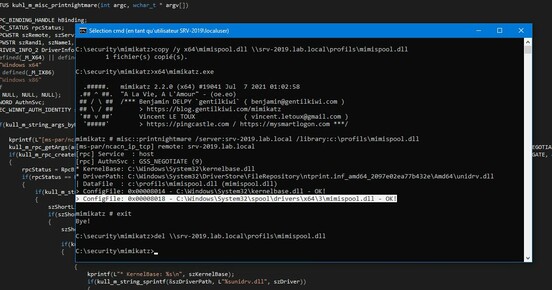
Little #printnightmare (ep 4.3) upgrade : user-to-system as a service🥝
> Open SYSTEM prompt
connect to \\printnightmare[.]gentilkiwi[.]com (remove [ ]) with
- user: .\gentilguest
- password: password
Open 'Kiwi Legit Printer - x64', enjoy SYSTEM
(just one printer this time🤪)
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
637 followers · 28210 posts · Server mastodon.socialRT @gentilkiwi
Little #printnightmare (ep 4.3) upgrade : user-to-system as a service🥝
> Open SYSTEM prompt
connect to \\printnightmare[.]gentilkiwi[.]com (remove [ ]) with
- user: .\gentilguest
- password: password
Open 'Kiwi Legit Printer - x64', enjoy SYSTEM
(just one printer this time🤪)
Pedro Fernandes · @DJPRMF
868 followers · 7898 posts · Server mastodon.socialBom, toca a desativar o Serviço de Spooler de Impressão do Windows mais uma vez....
#printnightmare v2.0
🖱🛠👉👕👈 SOSOrdinet 🎣🖥️🐛 🗞️ · @SOSOrdinet
15 followers · 845 posts · Server social.targaryen.house#PrintNightmare : un cauchemar sécuritaire qui serait partiellement colmaté par #Microsoft !
#PrintNightmare #microsoft #securite #spooler #windows #poc
🖱🛠👉👕👈 SOSOrdinet 🎣🖥️🐛 🗞️ · @SOSOrdinet
15 followers · 845 posts · Server social.targaryen.house#PrintNightmare : à nouveau le #spooler #Windows mis à mal… #Microsoft déploie un correctif d’urgence !
#PrintNightmare #spooler #windows #microsoft #securite #imprimante
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
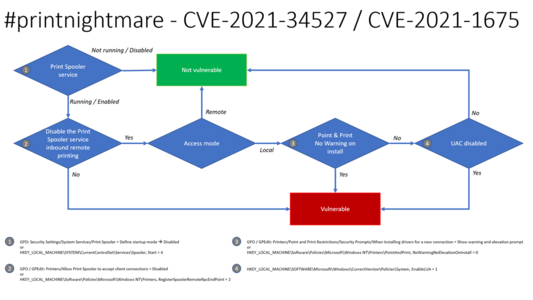
627 followers · 27846 posts · Server mastodon.socialDétail des différents cas de la faille #PrintNightmare
---
RT @gentilkiwi
Fix on a registry key for #printnightmare
https://twitter.com/gentilkiwi/status/1412483747321192451
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
637 followers · 28210 posts · Server mastodon.socialDétail des différents cas de la faille #PrintNightmare
---
RT @gentilkiwi
Fix on a registry key for #printnightmare
https://twitter.com/gentilkiwi/status/1412483747321192451
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
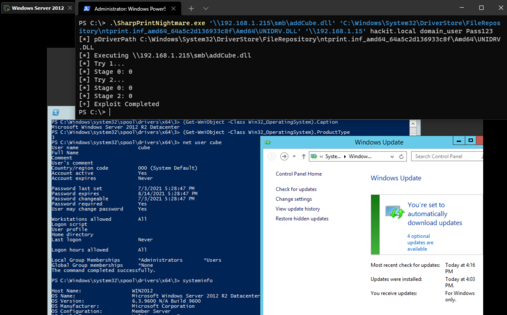
627 followers · 27846 posts · Server mastodon.socialRT @cube0x0
Disabling spooler on just your DC's is not enough #PrintNightmare
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
637 followers · 28210 posts · Server mastodon.socialRT @cube0x0
Disabling spooler on just your DC's is not enough #PrintNightmare
Geekland · @geekland
599 followers · 11921 posts · Server mastodon.social#PrintNightmare: la enésima pesadilla en Windows https://www.hackplayers.com/2021/07/printnightmare-la-enesima-pesadilla-en-windows.html
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
627 followers · 27846 posts · Server mastodon.socialRT @gentilkiwi
Thanks to @_f0rgetting_ we have an explanation about why we have an Elevated Token (allowing #PrintNightmare on patched domain controllers): legacy
If you remove "Authenticated users" from "Builtin\Pre-Windows 2000 Compatible Access", the original Microsoft Patch works again🤩 https://twitter.com/gentilkiwi/status/1410588058995548160
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
637 followers · 28210 posts · Server mastodon.socialRT @gentilkiwi
Thanks to @_f0rgetting_ we have an explanation about why we have an Elevated Token (allowing #PrintNightmare on patched domain controllers): legacy
If you remove "Authenticated users" from "Builtin\Pre-Windows 2000 Compatible Access", the original Microsoft Patch works again🤩 https://twitter.com/gentilkiwi/status/1410588058995548160