Thorsten Leemhuis (1/4) · @kernellogger
1998 followers · 1619 posts · Server fosstodon.orgTWIMC, the discussion about the #BPF extensible #scheduler class for the #Linux #kernel that Peterz rejected[1] slowly continues:
Mel Gorman recently shared his view and is "opposed to it conceptually": https://lore.kernel.org/all/20230817124457.b5dca734zcixqctu@suse.de/
Josh Don meanwhile "reiterated Google’s support for this proposal": https://lore.kernel.org/all/CABk29Nt_iCv=2nbDUqFHnszMmDYNC7xEm1nNQXibnPKUxhsN_g@mail.gmail.com/
[1] https://lore.kernel.org/all/20230726091752.GA3802077@hirez.programming.kicks-ass.net/ #LinuxKernel
#bpf #linux #kernel #linuxkernel #scheduler
Djalal Harouni · @djalaltix
14 followers · 7 posts · Server fosstodon.orgKernel Patching with Yaml!
Short post: preventing last overlayfs privilege escalations CVE-2023-2640 with Yaml (bpf) on Ubuntu kernels #tetragon #bpf
https://djalal.opendz.org/post/prevent-kernel-overlayfs-ubuntu-cves-with-yaml/
Peter Czanik · @PCzanik
294 followers · 518 posts · Server fosstodon.orgI just pushed syslog-ng 4.3.0 to @fedora Rawhide. Thanks to @bazsi, the dependency on the long time EoL pcre was finally replaced with pcre2. Along the way support for #bpf accelerated UDP source and @opentelemetry support were added:
https://github.com/syslog-ng/syslog-ng/releases/tag/syslog-ng-4.3.0
donaldh · @donaldh
9 followers · 222 posts · Server hachyderm.ioThorsten Leemhuis (1/4) · @kernellogger
1833 followers · 1408 posts · Server fosstodon.orgLOL:
```But the mptcpize (LD_PRELOAD technique) command has some limitations […]
- it is not in #BPF, we cannot talk about it at netdev conf. […]```
/me wonders what this kind of argument should be called; "appeal to cool technology" maybe?
Source: "[RFC bpf-next 0/8] BPF 'force to MPTCP'"
https://lore.kernel.org/mptcp/cover.1688616142.git.geliang.tang@suse.com/ #Linux #kernel #eBPF #LinuxKernel #MPTCP
#bpf #linux #kernel #ebpf #linuxkernel #mptcp
Thorsten Leemhuis (1/4) · @kernellogger
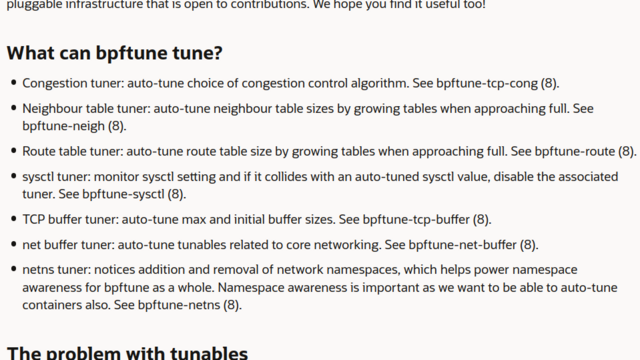
1833 followers · 1408 posts · Server fosstodon.orgIntroducing bpftune for lightweight, always-on auto-tuning of system behaviour – https://blogs.oracle.com/linux/post/introducing-bpftune
Alan Maguire writes:
```Introducing bpftune, an automatic configurator that monitors your workloads and sets the correct [#Linux] #kernel parameter values! […] using #BPF […] pluggable infrastructure that is open to contributions. […]``` #eBPF #LinuxKernel
#linux #kernel #bpf #ebpf #linuxkernel
Dave Marquardt · @davemq
61 followers · 421 posts · Server fosstodon.orgOh, as a long time TCP/IP guy who used and ported the original #BPF, it's a little annoying that the original BPF in BSD and other systems is ignored in most information about #eBPF. @brendangregg's books give BPF its due, though.
Galder Zamarreño · @galderz
8 followers · 26 posts · Server tooting.chComputing Performance 2022: What's on the Horizon https://www.youtube.com/watch?app=desktop&v=zGSQdN2X_k0 by @brendangregg #sre #performance #slo #latency #bpf #ebpf
#ebpf #bpf #latency #slo #performance #sre
Stéphane Bortzmeyer · @bortzmeyer
8168 followers · 78131 posts · Server mastodon.gougere.fr#BPF people now (running sandboxed programs in the kernel). Part of the effort to standardize BPF. Of course, at IETF, the focus is on BPF for networking.
Patches to the Linux kernel implementation.
https://ebpf.io/
Thorsten Leemhuis (1/4) · @kernellogger
1600 followers · 876 posts · Server fosstodon.orgTejun posted v3 of the BPF extensible scheduler class for the #Linux #kernel, which allows scheduling policies to be implemented as #BPF/#eBPF programs.
https://lore.kernel.org/all/20230317213333.2174969-1-tj@kernel.org/ #LinuxKernel
#linux #kernel #bpf #linuxkernel
Thorsten Leemhuis (1/4) · @kernellogger
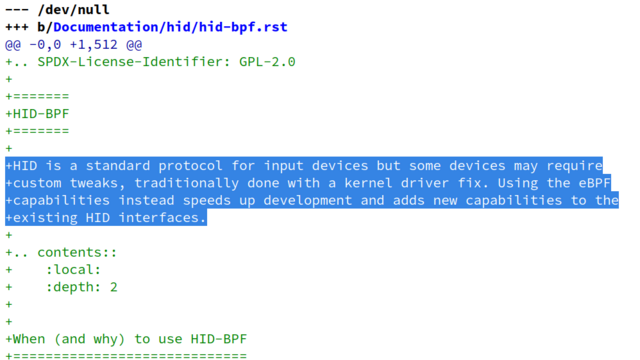
1543 followers · 732 posts · Server fosstodon.orgAfter a backslash ~ten weeks ago HID-#BPF now was finally merged for #Linux #kernel 6.3 with the main HID merge: https://git.kernel.org/torvalds/c/6c71297eaf713ece684a367ce9aff06069d715b9 :
- this allows to start using HID-BPF. Note that the mechanism to ship HID-BPF program through the kernel tree is still not implemented yet (but is planned).
- Logitech HID++ fixes for scroll wheel, protocol and debug
- Some new device support: Steam Deck, UClogic, Logitech G923 Xbox Edition steering wheel, EVision keyboards
stribika · @stribika
24 followers · 96 posts · Server infosec.exchangeHere is the problem, as far as I can tell. There are 2 different "BPF" variants: #BPF and #eBPF. What #LLVM calls BPF is in fact eBPF, while #seccomp only understands non-e BPF.
This was a horrible experience and a complete waste of time. If I need a compiler for security policies, you fucked up and should reconsider the design. (Remember selinux?) If I have to handcraft security policy bytecode, then my choice is between SECCOMP_MODE_STRICT or nothing.
Thank you for coming to my ted talk.
Thorsten Leemhuis (1/4) · @kernellogger
1501 followers · 603 posts · Server fosstodon.orgFlorian Westphal submitted an RFC patchset adding "minimal support to hook #bpf programs to #netfilter hooks, e.g. PREROUTING or FORWARD."
https://lore.kernel.org/all/20230208160307.27534-1-fw@strlen.de/ #Linux #kernel #LinuxKernel #eBPF
#bpf #netfilter #linux #kernel #linuxkernel #ebpf
Knomfr · @stuartdi
40 followers · 182 posts · Server ioc.exchangeWhile this article is selling a product, it is a good explainer on how eBPF could trigger on an event in a security context. https://www.sentinelone.com/blog/the-advantages-of-ebpf-for-cwpp-applications/ my understanding of map is a little better.
I’ve put Ida study on hold while I gain a deeper understanding of BPF. As I’ve mentioned, I’m just a part time hobbyist. Feel free to critique away anything I toot. #BPF
A thinking meat · @saint
419 followers · 1226 posts · Server river.group.ltSomehow BPF has hyped me and I want to see more usage of it, tools, teachings on how things work and people using it more for sysadmin tasks. (Reading https://vncz.js.org/ebpf/) #bpf #ebpf
Vincent Batts · @vbatts
664 followers · 1317 posts · Server fosstodon.orgHey #FOSDEM nerds! #Flatcar, #InspektorGadget, and #Headlamp volks will be there!
https://kinvolk.io/blog/2023/02/meet-us-at-fosdem-2023/
cc @headlamp
#ContainerLinux #CloudNative #BPF #eBPF #kubernetes
#fosdem #Flatcar #inspektorgadget #headlamp #containerlinux #cloudnative #bpf #ebpf #kubernetes
Thorsten Leemhuis (1/4) · @kernellogger
1455 followers · 535 posts · Server fosstodon.orgTejun posted v2 of the #Linux #kernel patchset[1] that allows influencing process scheduler decisions with #BPF/#eBPF programs:
https://lore.kernel.org/all/20230128001639.3510083-1-tj@kernel.org/
[1] it's called the "sched_ext (SCX) patchset", which "implements BPF extensible scheduler class" #LinuxKernel
#linux #kernel #bpf #linuxkernel
Knomfr · @stuartdi
41 followers · 176 posts · Server ioc.exchangeDetecting kernel exploits with #bpf #ebpf https://youtu.be/QTZvabExQ1I from #blackhat2022 speaker points out there are multiple points of failure with this approach. Author of open source tool KRIe https://github.com/Gui774ume/krie
Knomfr · @stuartdi
40 followers · 174 posts · Server ioc.exchangeHarnessing the eBPF Verifier https://blog.trailofbits.com/2023/01/19/ebpf-verifier-harness/ An interesting proof of concept for verifying interoperability with different kernel versions. Lays out challenges and solutions. #BPF Thanks for a great article.
Thorsten Leemhuis (1/4) · @kernellogger
1424 followers · 482 posts · Server fosstodon.orgThe content from Netdev 0x16 (held last Oct. 22) is now online.
For a session overview see:
https://netdevconf.info/0x16/accepted-sessions.html
Video breakdown:
Day 1: https://bit.ly/netdev-0x16-day-1
Day 2: https://bit.ly/netdev-0x16-day-2
Day 3: https://bit.ly/netdev-0x16-day-3
Day 4: https://bit.ly/netdev-0x16-day-4
Day 5: https://bit.ly/netdev-0x16-day-5
#netdev #networking #linux #kernel #linuxkernel #bpf #ebpf