SarlackLab · @SarlackLab
21 followers · 141 posts · Server ioc.exchangeCommand-and-control IPv4 map, 2023-05-31 to 2023-06-13 #CIDR
https://abjuri5t.github.io/SarlackLab/
94.142.138[.]0/24
45.155.249[.]0/24
5.42.64[.]0/22
91.215.85[.]0/24
103.212.81[.]0/24
141.98.6[.]0/24
194.50.153[.]0/24
45.81.39[.]0/24
5.62.20[.]0/24
45.11.180[.]0/24
SarlackLab · @SarlackLab
17 followers · 123 posts · Server ioc.exchangeCommand-and-control IPv4 map, 2023-05-11 to 2023-05-24 #CIDR
https://abjuri5t.github.io/SarlackLab/
91.202.246[.]0/23
94.142.138[.]0/24
173.239.236[.]0/24
141.98.6[.]0/24
37.220.87[.]0/24
77.73.134[.]0/24
156.234.180[.]0/24
45.12.253[.]0/24
95.214.27[.]0/24
45.15.156[.]0/24
SarlackLab · @SarlackLab
17 followers · 99 posts · Server ioc.exchangeCommand-and-control IPv4 map, 2023-04-21 to 2023-05-04 #CIDR
https://abjuri5t.github.io/SarlackLab/
94.142.138[.]0/24
45.15.156[.]0/24
62.204.41[.]0/24
23.227.196[.]192/28
185.215.113[.]0/24
83.217.11[.]0/24
95.214.27[.]0/24
37.220.87[.]0/24
77.73.134[.]0/24
31.41.244[.]0/24
↯ Klaatu - Some Brave Apollo ↯ · @Klaatu
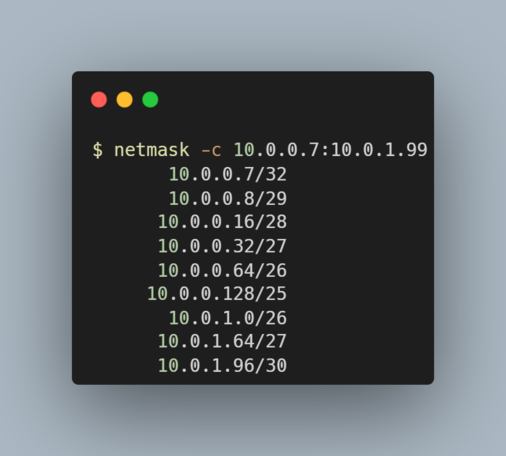
938 followers · 168150 posts · Server noagendasocial.com#CIDR Notation vs #Subnet Size
#networking #subnetting
#cidr #subnet #networking #subnetting
SarlackLab · @SarlackLab
12 followers · 63 posts · Server ioc.exchangeCommand-and-control IPv4 map, 2023-04-01 to 2023-04-14 #CIDR
https://abjuri5t.github.io/SarlackLab/
143.92.58[.]96/30
94.142.138[.]0/24
45.15.156[.]0/24
45.9.74[.]0/24
45.227.255[.]160/27
45.227.255[.]192/26
83.217.11[.]0/24
37.220.87[.]0/24
82.115.223[.]0/24
91.215.85[.]0/24
SarlackLab · @SarlackLab
5 followers · 9 posts · Server ioc.exchangeCommand-and-control IPv4 map, 2023-02-12 to 2023-02-25 #CIDR
https://abjuri5t.github.io/SarlackLab/
137.220.135[.]200/29
94.142.138[.]0/24
45.15.156[.]0/24
202.95.19[.]192/28
83.217.11[.]0/24
143.92.58[.]160/27
27.124.40[.]192/26
45.9.74[.]0/24
193.233.20[.]0/24
37.220.87[.]0/24
SarlackLab · @SarlackLab
2 followers · 2 posts · Server ioc.exchangeFAQ:
Are all these #CIDR blocks and #subdomains 100% malicious? - No, but they do host a SUBSTANTIAL amount of #C2 infrastructure
What’s the grid thingy? - A #HilbertCurve map of #IPv4 space
You spelled #sarlacc wrong! - The name is intentional🤓
DM @Abjuri5t for more info
#cidr #subdomains #c2 #hilbertcurve #ipv4 #sarlacc
CK's Technology News · @CKsTechNews
1736 followers · 1689 posts · Server cktn.todon.deHardCIDR – Network #CIDR and Range Discovery #Tool
Info
#HardCIDR is a #Linux Bash script to discover the #netblocks, or ranges, (in CIDR notation) owned by the target organization during the intelligence gathering phase of a penetration test.
#cidr #tool #hardcidr #linux #netblocks
pirate moo🐮 · @apiratemoo
3171 followers · 1253 posts · Server infosec.exchangeOld subnetting notes I had to dig up and refresh on while studying tonight. Enjoy!
Subnetting:
The representations of IP’s and prefixes (our masks) exist for each range. Whenever we see a /8, /16, or /24, the /number is a prefix, so 10.10.10.1 /24 is an address with a prefix. The classes listed for IPv4 aren't actually too scary when you space out exactly what is going on.
Let’s say we have a 255.255.255.0 mask
Try to look at it this way: Class A is X.Y.Y.Y Y being the hosts by number
If we have a /24 and need to understand how this translates:
255.255.255.0 is the value we end up with because the binary equivalent to 255 is 11111111
If we do this for every portion of our mask we get:
11111111.11111111.11111111.00000000
We end up with /24 because we are counting each set of 1's (11111111 + 11111111 + 11111111 = 24).
All we're essentially doing here when we subnet is counting the bits and looking at a mask.
If you look at it this way then the 2n-2 formula makes a lot more sense and becomes clearer.
What would be a /26 ? 11111111.11111111.11111111.11000000 or 24 +2
We added 2 bits to the sum we had when we converted and if we convert 11000000 again, we get 192 as a number. Then we subtract.
** Resources:**
https://subnetting.org
https://www.youtube.com/watch?v=ZxAwQB8TZsM
#subnetting #subnet #networking #network #infosec #cidr
Chris · @chr1stian
72 followers · 33 posts · Server mastodon.socialDeaDSouL :fedora: :fediverse: · @DeaDSouL
167 followers · 373 posts · Server fosstodon.orgDick Smiths Fair Go Supporters · @dsfgs
178 followers · 12401 posts · Server activism.openworlds.infoQuietly (but finally) adds to the #firewall blocklist, TurdSite #IPAddresses.
#firewall #IPAddresses #cidr #blocklist