PrivacyDigest · @PrivacyDigest
570 followers · 2185 posts · Server mas.toThe Comedy of Errors That Let China-Backed Hackers Steal Microsoft’s #SigningKey
After leaving many questions unanswered, #Microsoft explains in a new postmortem the series of slipups that allowed attackers to steal and abuse a valuable #cryptographic key.
#privacy #security #encryption #china
https://www.wired.com/story/china-backed-hackers-steal-microsofts-signing-key-post-mortem/
#China #encryption #security #privacy #cryptographic #Microsoft #signingkey
BadGuysGetDead · @badguysgetdead
119 followers · 126 posts · Server synthwave.socialOnce a #cryptographic #cipher is successfully broken and meticulously documented, its veil of #security becomes irreparably compromised.
ROT13 - Out Now
/// Gur shegure n fbpvrgl qevsgf sebz gehgu gur zber vg jvyy ungr gubfr jub fcrnx vg. - Bejryy ///
https://badguysgetdead.bandcamp.com/track/rot13
---
#chipwave #chiptune #chip-hop #cyberpunk #dystopia #technology #encryption #privacy #music #cinematic #synthwave #newmusic
#cryptographic #cipher #security #chipwave #chiptune #chip #cyberpunk #dystopia #technology #encryption #privacy #music #cinematic #synthwave #newmusic
CryptoNewsBot · @cryptonewsbot
689 followers · 37723 posts · Server schleuss.onlineUK Researchers Claim New Tech Supercharges Bitcoin Mining With 260% Faster Hash Detection, Slashes Energy Use - Quantum Blockchain Technologies (QBT), a research firm hailing from the U.K., purp... - https://news.bitcoin.com/uk-researchers-claim-new-tech-supercharges-bitcoin-mining-with-260-faster-hash-detection-slashes-energy-use/ #quantumcomputing #machinelearning #bitcoinmining #cryptographic #energy-saving #breakthrough #deeplearning #logicalgates #blockchain #terahashes #btcmining
#btcmining #terahashes #blockchain #logicalgates #deeplearning #breakthrough #energy #cryptographic #bitcoinmining #machinelearning #quantumcomputing
sbo · @sbo_slv
76 followers · 424 posts · Server mas.to"Microsoft says hackers somehow stole a cryptographic key, perhaps from its own network, that let them forge user identities and slip past cloud defenses." #microsoft #cryptographic #masterkey #hackers #cloud
https://www.wired.com/story/microsoft-cloud-attack-china-hackers/
#cloud #hackers #masterkey #cryptographic #Microsoft
Alhaythum · @Alhaythum
42 followers · 108 posts · Server noc.social#Microsoft says hackers somehow stole a #cryptographic key, perhaps from its own network, that let them forge user identities and slip past #cloud #defenses.
https://www.wired.com/story/microsoft-cloud-attack-china-hackers/
#defenses #cloud #cryptographic #microsoft
Toni Aittoniemi · @gimulnautti
292 followers · 3365 posts · Server mastodon.green@Juro With #single-#use #cryptographic #hashes, we could still enable somewhat strong #anonymity together with strong human id #verification.
Learning from India’s Aadhar system, it is clear that a single #token isn’t good enough.
Perhaps something similar to blockchain, where you can mine some tokens that identify you. And you can throw away like wallets to escape tracking when you need to.
#single #use #cryptographic #hashes #anonymity #verification #token
· @ediepdx
86 followers · 114 posts · Server mstdn.partyAnd speaking of which:
Robert Hanssen died recently. He was seen as a #cryptographic and #computer expert- also seen as a #cybersecurity expert. But as it turns out- he was the ultimate threat.
I think also one of the lessons of #cybersecurity is understand that the experts themselves are the threat.
#cryptographic #computer #cybersecurity
DevWouter · @DevWouter
77 followers · 638 posts · Server s.poweredbydev.comI just want to send a encrypted decryption key that can’t be used to encrypt another message using the wrapKey of #subtlecrypto but I get unspecified errors all around. Guess tomorrow I will be spending time figuring out which combinations are allowed.
#subtlecrypto #browser #security #cryptographic #programming
5h15h · @shish
89 followers · 550 posts · Server techhub.socialZero Knowledge Proofs (#ZKP) can provide #retailers with a powerful tool for ensuring #customerprivacy, enhancing #security, and improving the overall #customerexperience.
A #ZKP is a #cryptographic protocol in which one party, th…https://lnkd.in/gtNc3Rxk https://bit.ly/3m8eTEH
#zkp #retailers #customerprivacy #security #customerexperience #cryptographic
Justin D Kruger · @jdavidnet
39 followers · 94 posts · Server me.dm@rasterweb
For a #Cryptographic #AI #ImageProtection solution in the browser,
Create an #OpenSource javascript library that can take an encrypted asset and then decrypt it. Then render the image in a #HTML5 <canvas> tag.
I see two possible implementations:
1. #openkey system - meant to add a decryption step; it won't stop anyone who uses the same library to decrypt it. which requires willful intent to steal the image.
2. use a private system, and use auth or payment to release a key
#cryptographic #ai #imageprotection #opensource #html5 #openkey
Justin D Kruger · @jdavidnet
39 followers · 94 posts · Server me.dm@rasterweb
#Cryptographic #AI #ImageProtection can work for a few reasons
1. declares an intent to protect
2. amplifies #copyright law around encrypted content
3. scrappers are usually simple, and this adds complexity at a different layer than the machine learning algorithm
4. #cryptography adds compute time to the process; how much depends on how dense the method is.
But #metadata and #microformats are also useful
#cryptographic #ai #imageprotection #copyright #cryptography #metadata #microformats
IL Photonics · @ILphotonics
5 followers · 42 posts · Server qoto.orgUltimate #security for connected devices and #IoT systems: Combining quantum random number generator (#QRNG) technology and #cryptographic communication semiconductor technology into one security chipset. This next generation security chip provides the highest level of security for IoT and connected devices and unrivalled protection against hacking. Learn more: https://ilphotonics.com/new-quantum-enhanced-cryptographic-chip-released/
#security #iot #QRNG #cryptographic
doegox · @doegox
528 followers · 50 posts · Server infosec.exchangeWanna break #cryptographic whitebox implementations protected by external encodings? We're releasing Dark Phoenix, an open source implementation of the 2019 DFA #Attack paper by Amadori, Michiels and Roelse
https://blog.quarkslab.com/dark-phoenix-a-new-white-box-cryptanalysis-open-source-tool.html
CryptoNewsBot · @cryptonewsbot
353 followers · 12555 posts · Server schleuss.onlineMeme Coin Economy Swells by $5.8 Billion in Less Than a Month, Suggesting Demand for Meme Tokens Still High - The meme coin economy has grown significantly over the past 27 days, increasing 34... - https://news.bitcoin.com/meme-coin-economy-swells-by-5-8-billion-in-less-than-a-month-suggesting-demand-for-meme-tokens-still-high/ #marketcapitalization #marketsandprices #memetokeneconomy #statisticaldata #cryptographic #pomeranianeth #third-largest #babydogecoin #marketaction #memeeconomy
#memeeconomy #marketaction #babydogecoin #third #pomeranianeth #cryptographic #statisticaldata #memetokeneconomy #marketsandprices #marketcapitalization
Messageries Club de France · @Olvid_Club_de_France
53 followers · 342 posts · Server mastodon.socialA group of #Swiss researchers have published an impressive #securityanalysis of #Threema.
"We provide an extensive #cryptographic analysis of Threema , a Swiss-based #encrypted #messaging application with more than 10 million users and 7000 corporate customers. As one example, we present a cross-protocol attack which breaks authentication in Threema and which exploits the lack of proper key separation between different sub-protocols. [...]"
https://securityboulevard.com/2023/01/security-analysis-of-threema/
#swiss #securityanalysis #threema #cryptographic #encrypted #messaging #cybersecurite #ibexprotocol
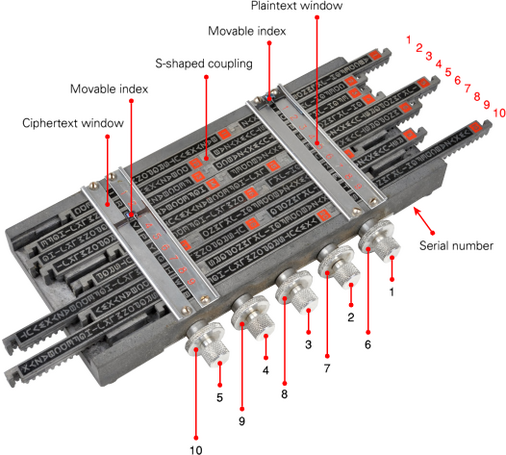
Messageries Club de France · @Olvid_Club_de_France
53 followers · 342 posts · Server mastodon.socialLE SPHINX was a pocket #cryptographic device, developed around 1930 by Société des Codes Télégraphiques Georges Lugagne in #Paris ( #France ). The device consists of 10 sliding bars with two scrambled #alphabets each, and should therefore be classed as an alphabet transposition #cipher . At the time, it was advertised as a method for #secret writing when sending ( #radio ) #telegrams .
#cryptographic #paris #france #alphabets #cipher #secret #radio #telegrams #telegraphe #chiffrement #cryptographie #belobjet
Tod Beardsley 🏴☠️ · @todb
1093 followers · 1020 posts · Server infosec.exchangeI’ve been doing some basic research on email #security the last couple days, and just came across this lovely blog post about #DKIM #cryptographic assurances lasting way long than intended. It’s a pretty great “intro to DKIM” read! From 2020!
https://blog.cryptographyengineering.com/2020/11/16/ok-google-please-publish-your-dkim-secret-keys/
#security #dkim #cryptographic
Sam A Lamb, A Ding-Dong · @Heterokromia
118 followers · 446 posts · Server aus.socialI would like to find a #cryptographic technique that would allow Alice and Bob to exchange messages.
Each message is written in a simple defined language.
I want; syntactic correctness of both messages to be essential to the decryption of each message, and that the timestamps of both be near-enough for them to be considered to have passed each other in flight.
Please help me to find code where this already exists? I am struggling.
Mirabeau Tech · @rss_tech
1 followers · 468 posts · Server social.technoetic.com#CryptoGuard is a high-precision tool used for detecting #cryptographic application programming interface misuse. In this article #researchers explore the needs and challenges of deployable #security #research: https://www.computer.org/csdl/magazine/sp/2022/06/09782873/1DIwV6jxOY8
#cybersecurity #privacy #stem #tech
Originally posted by IEEE ComputerSociety / @ComputerSociety@twitter.com: https://twitter.com/ComputerSociety/status/1610690274132463644#m (Wed, 04 Jan 2023 17:31:01 GMT)
Referenced link: https://www.computer.org/csdl/magazine/sp/2022/06/09782873/1DIwV6jxOY8
#cryptoguard #cryptographic #researchers #security #research #cybersecurity #privacy #stem #tech
Kristian Harstad · @KristianHarstad
357 followers · 537 posts · Server mastodon.cloudso i saw this here #kitty
and it got me thinking about #compression and #cryptographic #algorithms
and how much more fun they would be if they were #cat themed
purretty good purrivacy? #PGP #GPG
furball instead of #tarball?
ohhhh... remember #cryptocat?
#tarball #cryptocat #cryptographic #algorithms #pgp #gpg #kitty #compression #cat