Paul Weber · @000panther
148 followers · 79 posts · Server ooe.socialIch bin jetzt uebrigens auf ein groesseres Schiff gewechselt und hab bei #dynatrace angeheuert!
Nils Goroll · @slink
60 followers · 496 posts · Server fosstodon.orgDear #infosec community, is anyone aware of any independent audits/research on the security of #dynatrace or its inner workings?
My understanding is that it is basically a remote controlled system- and library-call interceptor implemented as an LD_PRELOAD library with super powers over any code run under its control.
For short, I call it a #rootkit. Do you agree or disagree that this simplification for not-so-tech-savy people is adequate? (edit: grammar)
Colin McNaughton · @cloin
18 followers · 31 posts · Server techhub.social🔧 Just finished an exciting demo on bridging observability and automation using Event-Driven @ansible and #Dynatrace. We automated responses to events in real-time to remediate an issue on the fly, and logged an incident for later review! 💻🚀
Check out the video https://www.youtube.com/watch?v=7i_EzHyrKQc
#ansible #dynatrace #eventdriven #observability #automation
Adam Gardner · @agardnerit
16 followers · 88 posts · Server techhub.socialtracepusher v0.6.0 has been released.
tracepusher v0.6.0:
- Adds support for span attributes
- Adds documentation website: https://agardnerit.github.io/tracepusher/
- Both #opensource and #dynatrace Killercoda tutorials have been upgraded
#opensource #dynatrace #tracepusher #jaeger #opentelemetry
wassx · @wassx
17 followers · 56 posts · Server mastodon.world#Dynatrace #AppEngine announced! 🤩 So #proud to be part of the #team 💪 #perform2023 https://www.dynatrace.com/platform/appengine/
#dynatrace #appengine #proud #team #perform2023
· @wurstsalat
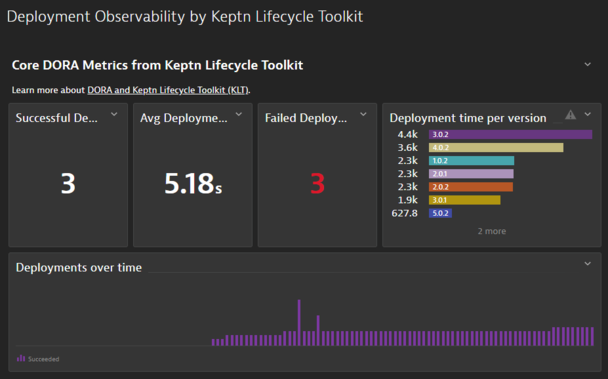
33 followers · 115 posts · Server crashloop.socialRT @grabnerandi
Update for our @Dynatrace users who use @keptnProject (Keptn Lifecycle Toolkit) to get k8s deployment #observability.
I uploaded my #dynatrace DORA dashboard that shows @opentelemetry @PrometheusIO data generated by Keptn in my demo repo ==> https://github.com/keptn-sandbox/klt-on-k3s-with-argocd#dynatrace-dora-dashboard