Mr.Trunk · @mrtrunk
10 followers · 17826 posts · Server dromedary.seedoubleyou.meSecurityOnline: Sekiryu: Comprehensive toolkit for Ghidra headless https://securityonline.info/sekiryu-comprehensive-toolkit-for-ghidra-headless/ #VulnerabilityAnalysis #ReverseEngineering #Ghidraheadless #Sekiryu #Ghidra
#vulnerabilityanalysis #reverseengineering #ghidraheadless #sekiryu #ghidra
Giovanni Crisalfi · @gicrisf
87 followers · 323 posts · Server fosstodon.orgI never wrote Assembly in my life, but tonight (for some reason) I thought of disassembling simple C code snippets with Ghidra. So, I started with a hello world and was very surprised to find a much more extensive and complex result compared to my original assembly (obtained with GCC).
I mean, it's a Hello World!
#ghidra #gcc #clang #assembly #asm
Milos Constantin · @Tinolle
68 followers · 158 posts · Server hachyderm.ioComprehensive toolkit for #Ghidra headless https://github.com/20urc3/Sekiryu?s=09
The Last Psion | Alex · @thelastpsion
363 followers · 900 posts · Server bitbang.socialIs anyone using #Ghidra to #decompile DOS apps to C? Have you had much success?
Yes, my brain is trying to find distractions again, but this is my last gasp of dopamine-hunting before the day job gets busy again.
#retrocomputing #decompile #ghidra
mcneb10 · @mcneb10
4 followers · 45 posts · Server mstdn.socialHello #ghidra users! How do you keep track of your progress reverse-engineering something? I’m working on a game engine with ~1.6K functions and it’s hard to visualize how much work I still have to do. Any suggestions?
Lup Yuen Lee 李立源 · @lupyuen
1670 followers · 17600 posts · Server qoto.org#Ghidra decompiles the #RISCV #Linux Kernel for Star64 SBC
Source: https://github.com/lupyuen/nuttx-star64#decompile-armbian-kernel-image-with-ghidra
Adam ♿ · @voltagex
396 followers · 1088 posts · Server aus.socialLooks like libtiqiaadev.so is the way to go.
nm -D tells me there's functions exported like:
Java_com_icontrol_dev_TiqiaaCIRDevice_x
Java_com_icontrol_dev_TQUartDevice_x
(just strange function names, not actually using JNI or anything?)
Time to go pretend I know how to use #Ghidra
Slayerranger/Crackamphetamine · @crackamphetamine
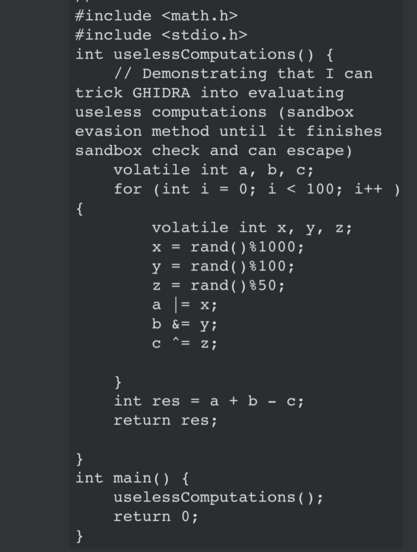
28 followers · 1292 posts · Server cyberplace.socialSo #ghidra between versions 10.1.5 and 10.2.3 has gotten better at removing dead/junk code when I write #malware #pentesting payloads.
Basically, without returning the values of junk calculations (gcc/g++ 11.3.0), your junk code that you may be using for say… sandbox evasion (faking a computation loop) would disappear in the decompilation section.
So what do you do? Set all integers to volatile, and RETURN them without even using them. As you can see, they reappear in the decompilation.
Gus · @projectgus
671 followers · 732 posts · Server aus.socialI have a silly newbie #Ghidra question: if you have some binary data in an executable and you want to export those data bytes to a binary file as-is, can you do this?
The best options I've found are:
- "Export and Import", which is a cool feature but means importing the file it just wrote out back into the Ghidra project, which isn't always useful.
- "Copy Python Byte String" then paste the byte string into a Python REPL, and use a one-liner to write that to a file. Works fine, seems roundabout...
Surely there's something obvious I'm missing here?
Sidney Borne :donor: · @Sidneys1
47 followers · 257 posts · Server infosec.exchangeNew #blogpost! This time we dig into the disassembly of the game we looked at in part 1, and identify an undocumented settings file.
https://sidneys1.com/reverse-engineering/2023/03/16/reverse-engineering-a-win95-game-II.html
#reverseengineeing #ghidra #windows95 #retrogaming #retrocomputing
#blogpost #reverseengineeing #ghidra #windows95 #retrogaming #retrocomputing
Sébastie[N] Kirche :debian: · @sebkirche
56 followers · 879 posts · Server framapiaf.orgTIL about the existence of #Reko an #IDA / #Ghidra like decompiling and reversing tool. Unfortunately for me it is made with .Net 6.0 and won't run on my main Linux workstation. https://github.com/uxmal/reko
CyberKaida (サイバーかいだ) · @cyberkaida
115 followers · 278 posts · Server infosec.exchangeWe got libfrida-core building for Ghidra and loaded into the Debugger extension during the stream today! With a bit of work we’ll have the Frida 15 to 16 port done and a script to automatically build the Frida Ghidra extension! 🥳
#ghidra #frida #debugger #reverseengineering #vtuber
0xor0ne · @0xor0ne
593 followers · 120 posts · Server infosec.exchangeCool blog post for learning Ghidra a little bit more in depth by adding a new ISA (credits Tracy Mosley)
https://trenchant.io/expanding-the-dragon-adding-an-isa-to-ghidra/
#ghidra #reverseengineering #infosec #cybersecurity
Renaud Lifchitz :verified: · @nono2357
257 followers · 2020 posts · Server infosec.exchangeRT @0xor0ne
Nice blog post by @clearbluejar on Ghidra scripting with Python 3 (Pyhidra)
https://clearbluejar.github.io/posts/callgraphs-with-ghidra-pyhidra-and-jpype/
And a general overview of Ghidra scripting in python
https://clearbluejar.github.io/posts/building-vscode-ghidra-python-skeletons/
#ghidra #reverseengineering #infosec #cybersecurity
CyberKaida (サイバーかいだ) · @cyberkaida
115 followers · 267 posts · Server infosec.exchangeJust added a script to Ghidra to build the lldb bindings from a brew install. Hopefully this will make it a little easier to use lldb and Ghidra together! 🐉👩💻
Michael Oland · @uthanda
16 followers · 56 posts · Server musician.socialTrying my hand at reverse engineering using #ghidra. It's fun but mind bending for sure.
GeekProjects News · @news
2 followers · 2317 posts · Server geekprojects.comMaking Ghidra Play Nice With RP2040 https://hackaday.com/2023/03/01/making-ghidra-play-nice-with-rp2040/ #ReverseEngineering #RaspberryPi #SVDfile #Ghidra #rp2040
#ReverseEngineering #RaspberryPi #SVDfile #ghidra #rp2040
IT News · @itnewsbot
2956 followers · 251380 posts · Server schleuss.onlineMaking Ghidra Play Nice With RP2040 - Developing firmware for RP2040 is undeniably fun, what’s with all these PIOs. Howe... - https://hackaday.com/2023/03/01/making-ghidra-play-nice-with-rp2040/ #reverseengineering #raspberrypi #svdfile #ghidra #rp2040
#rp2040 #ghidra #svdfile #raspberrypi #reverseengineering
Sidney Borne :donor: · @Sidneys1
45 followers · 237 posts · Server infosec.exchangeAnyone have experience #reverseengineering Win32 applications and identifying variables within thread-local storage? #Ghidra doesn't seem to know anything about them.
#reverseengineering #ghidra #askfedi
Hexorg · @hexorg
47 followers · 242 posts · Server techhub.socialPretty excited - in preparation to my talk I have found and fixed a bug in #ghidra on my own… it’s a small regression bug but it took some digging to figure it out. https://github.com/NationalSecurityAgency/ghidra/issues/5027
Someone elsewhere pointed out that RSP = RSP +8 - RAX is the correct solution.
… I should submit a pull request