sbug · @sbug
65 followers · 347 posts · Server social.sinnesro.seITSEC News · @itsecbot
1292 followers · 35180 posts · Server schleuss.onlineTime Taken For Hackers to Crack Passwords Revealed - New Specops Software research has unearthed the length of time it takes modern attackers ... https://www.itsecurityguru.org/2023/05/18/time-taken-for-hackers-to-crack-passwords-revealed/?utm_source=rss&utm_medium=rss&utm_campaign=time-taken-for-hackers-to-crack-passwords-revealed #cybersecurity #editorsnews #features #password #hashing #specops #news
#news #specops #hashing #password #features #editorsnews #cybersecurity
The Hacker News · @hackernews_bot
2437 followers · 1672 posts · Server social.platypush.techReferenced link: https://specopssoft.com/blog/best-password-practices-to-defend-against-modern-cracking-attacks/
Discuss on https://discu.eu/q/https://specopssoft.com/blog/best-password-practices-to-defend-against-modern-cracking-attacks/
Originally posted by The Hacker News / @TheHackersNews: http://nitter.platypush.tech/specopssoftware/status/1658857543131701248#m
RT by @TheHackersNews: How long does it take modern attackers to brute-force guess user passwords with the help of newer hardware?
See how long it will take a criminal to brute force guess passwords hashed with MD5.: https://specopssoft.com/blog/best-password-practices-to-defend-against-modern-cracking-attacks/
#cyberattack #cybersecurity #passwords #hashing
Robert Mooney · @vermelho
3 followers · 356 posts · Server babka.social
Mohammad Hajiaghayi · @MTHajiaghayi
29 followers · 29 posts · Server mathstodon.xyzNow (7pm ET Wed) watch https://youtu.be/9x8rcQYs1so (FEEL FREE TO SUBSCRIBE TO YOUTUBE
@hajiaghayi
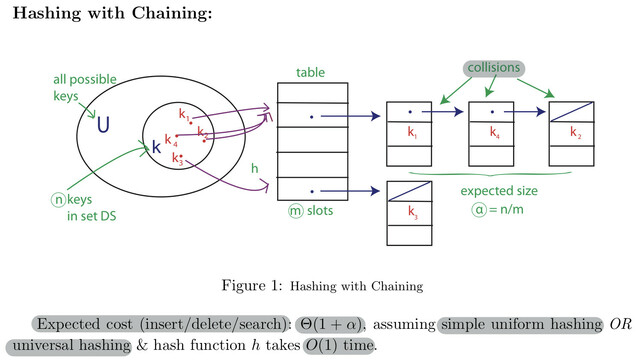
FOR FUTURE LESSONS) Lesson 16: Introduction to Algorithms by Mohammad Hajiaghayi: #orderselection #universal #hashing #collision #resolution
#resolution #collision #hashing #universal #orderselection
mkj · @mkj
45 followers · 632 posts · Server social.linux.pizza@kubikpixel @Stark9837 #Encrypting #passwords doesn't get better because you use a library someone else has written to implement the #encryption.
Salted slow #hashing for passwords, yes. (Again, with the exception of #PasswordManagers where passwords really need to be stored securely in a reversible fashion.) But then you still aren't doing #encryption, you're doing #hashing, which was the point of my previous post.
#encrypting #passwords #encryption #hashing #passwordmanagers
mkj · @mkj
45 followers · 632 posts · Server social.linux.pizza@Stark9837 Passwords should never be stored encrypted. (The one exception being #PasswordManagers.) There is no legitimate reason to store passwords encrypted. Any service which encrypts, rather than hashes, #passwords should be treated as highly suspect.
I know a lot of people don't know the difference, but there is a HUGE one.
#Encryption is by definition reversible.
#Hashing is irreversible (if done right).
That said, I absolutely agree that every #password should be random and unique.
#passwordmanagers #encryption #passwords #hashing #password
tkteo · @tkteo
39 followers · 1219 posts · Server infosec.exchangePaper 2023/331 A Vulnerability in Implementations of SHA-3, SHAKE, EdDSA, and Other NIST-Approved Algorithm
Abstract
This paper describes a vulnerability in several implementations of the Secure Hash Algorithm 3 (SHA-3) that have been released by its designers. The vulnerability has been present since the final-round update of Keccak was submitted to the National Institute of Standards and Technology (NIST) SHA-3 hash function competition in January 2011, and is present in the eXtended Keccak Code Package (XKCP) of the Keccak team. It affects all software projects that have integrated this code, such as the scripting languages Python and PHP Hypertext Preprocessor (PHP). The vulnerability is a buffer overflow that allows attacker-controlled values to be eXclusive-ORed (XORed) into memory (without any restrictions on values to be XORed and even far beyond the location of the original buffer), thereby making many standard protection measures against buffer overflows (e.g., canary values) completely ineffective. First, we provide Python and PHP scripts that cause segmentation faults when vulnerable versions of the interpreters are used. Then, we show how this vulnerability can be used to construct second preimages and preimages for the implementation, and we provide a specially constructed file that, when hashed, allows the attacker to execute arbitrary code on the victim's device. The vulnerability applies to all hash value sizes, and all 64-bit Windows, Linux, and macOS operating systems, and may also impact cryptographic algorithms that require SHA-3 or its variants, such as the Edwards-curve Digital Signature Algorithm (EdDSA) when the Edwards448 curve is used. We introduce the Init-Update-Final Test (IUFT) to detect this vulnerability in implementations. #cryptography #encryption #sha #sha3 #cybersecurity #hash #hashing #algorithm #algorithms #nist #nistcybersecurityframework
#cryptography #encryption #sha #sha3 #cybersecurity #hash #hashing #algorithm #algorithms #nist #nistcybersecurityframework
Jess For A Laugh · @meeple
24 followers · 13 posts · Server mstdn.gamesAnd of course I forgot #ChronicIllness #InvisibleIllness #MentalHealth #ProChoice #Hashing #H3 #Barfleet and a slew of other schtuff.
#chronicillness #invisibleillness #mentalhealth #prochoice #hashing #h3 #barfleet #followfriday #followbackfriday
Gregory P. Smith (he/him) :python: 🚲🦝 :donor: · @gpshead
339 followers · 816 posts · Server infosec.exchange@campuscodi The need for these confuses me because in 2023 I have a hard time imagining that fitting AES and SHA2 into connection capable microcontrollers on a power budget is difficult. What is my imagination missing?
#NIST #Ascon #IoT #cryptography #hashing
#nist #ascon #iot #cryptography #hashing
Aisuko · @aisuko
1 followers · 38 posts · Server hostux.socialMarco Zocca · @ocramz
121 followers · 84 posts · Server sigmoid.socialwhen the world was young and people lovingly engineered their features..
("An industrial-strength audio search algorithm", Wang 2003)
https://www.ee.columbia.edu/~dpwe/papers/Wang03-shazam.pdf
#machinelearning #music #audio #search #hashing #informationretrieval
#machinelearning #music #audio #search #hashing #informationretrieval
aegilops :github::microsoft: · @aegilops
80 followers · 282 posts · Server fosstodon.org@gudenau for a static set:
https://en.wikipedia.org/wiki/Static_hashing#FKS_Hashing
For a dynamic set:
https://en.wikipedia.org/wiki/Dynamic_perfect_hashing
If you have space constraints and can accept some false positives:
https://en.wikipedia.org/wiki/Bloom_filter
#hashing #bloomfilter #algorithms
Harry · @harry
0 followers · 14 posts · Server techhub.socialBlog: How Blockchain Can Enhance Data Loss Prevention for Data Protection #blockchain #dlp #datalossprevention #dataleakage #dataprotection #datasecurity #filestorage #filesharing #googledrive #googledocs #medium #blockchain2023 #blockchaintechnology #zeroknowledge #hashing #encryption
https://medium.com/@jungsy11/how-blockchain-can-enhance-data-loss-prevention-for-data-protection-fd1603c2aea9
#blockchain #dlp #datalossprevention #dataleakage #dataprotection #datasecurity #filestorage #filesharing #googledrive #googledocs #medium #blockchain2023 #blockchaintechnology #zeroknowledge #hashing #encryption
Wepwawet ☑️ · @wepwawet
59 followers · 1219 posts · Server mastodon.socialHacking and Horror movies #horrormovies #90s #stephenking #it #hacking #hashing #crypto #tryhackme #HolidayOREOke #wepwawet #graywolf #zodmagus #hbomax #HorrorFamily
#horrormovies #90s #stephenking #it #hacking #hashing #crypto #tryhackme #holidayoreoke #wepwawet #graywolf #zodmagus #hbomax #horrorfamily
:hacker_z: :hacker_o: :hacker_d: :verified: · @zodmagus
87 followers · 426 posts · Server infosec.exchangeHashing - Crypto 101 - I have just completed this room! Check it out: https://tryhackme.com/room/hashingcrypto101 #tryhackme #security #crypto #hashing #101 #Crypto 101 #NinjaJc01 #hashingcrypto101 via @RealTryHackMe
#tryhackme #security #crypto #hashing #ninjajc01 #hashingcrypto101
:hacker_z: :hacker_o: :hacker_d: :verified: · @zodmagus
87 followers · 424 posts · Server infosec.exchangeHacking and Horror movies #horrormovies #90s #stephenking #it #hacking #hashing #crypto #tryhackme #HolidayOREOke #wepwawet #graywolf #zodmagus #hbomax
#horrormovies #90s #stephenking #it #hacking #hashing #crypto #tryhackme #holidayoreoke #wepwawet #graywolf #zodmagus #hbomax
Blain Smith · @blainsmith
301 followers · 703 posts · Server fosstodon.orgIntroduction to Locality-Sensitive Hashing https://tylerneylon.com/a/lsh1/ #Hashing
Marcus Botacin · @MarcusBotacin
31 followers · 31 posts · Server infosec.exchange[Paper of the day][#18] How do you triage #malware? How do you tell two files are similar? An interesting static analysis approach is to use #similarity #hashing tools, such as #ssdeep and #sdhash. However, to be effective, their application can't be straightforward, but should follow a protocol. In this paper, we discuss how to efficiently apply these functions for malware family classification. We show that hashing only the instruction disassembly has a greater impact than hashing the entire file. Check this result and much more.
Academic paper: https://www.sciencedirect.com/science/article/pii/S2666281721001281
Archived version: https://secret.inf.ufpr.br/papers/marcus_similarity_hashing.pdf
#malware #similarity #hashing #ssdeep #sdhash
ITSEC News · @itsecbot
943 followers · 32667 posts · Server schleuss.onlineSerious Security: MD5 considered harmful – to the tune of $600,000 - It's not just the hashing, by the way. It's the salting and the stretching, too! https://nakedsecurity.sophos.com/2022/11/30/serious-security-md5-considered-harmful-to-the-tune-of-600000/ #cryptography #law&order #hashing #pbkdf2 #cnil #edf #md5
#md5 #edf #cnil #pbkdf2 #hashing #law #cryptography