RulesBenitez · @rulesbenitez
0 followers · 91 posts · Server ioc.exchangeALERTA¡¡¡ La unidad de investigación de #SILIKN ha emitido una alerta por la presencia en México de #HiatusRAT, un troyano de acceso remoto (RAT), malware diseñado para permitir que un atacante controle de forma remota una computadora infectada. https://computerworldmexico.com.mx/emiten-alerta-por-presencia-de-hiatusrat-en-mexico/
Opalsec :verified: · @Opalsec
175 followers · 85 posts · Server infosec.exchangeHappy Monday folks, I hope you had a restful weekend and managed to take a breather from all things cyber! Time to get back into it though, so let me give you hand - catch up on the week’s infosec news with the latest issue of our newsletter:
https://opalsec.substack.com/p/soc-goulash-weekend-wrap-up-09e?sd=pf
#Emotet are back and are using…OneNote lures? ISO disk images? Malvertising? Nah – they’re sticking with tier tried and true TTPs – their Red Dawn maldoc template from last year; macro-enabled documents as lures, and null-byte padding to evade automated scanners.
We’ve highlighted a report on the Xenomorph #Android Banking Trojan, which added support for targeting accounts of over 400 banks; automated bypassing of MFA-protected app logins, and a Session Token stealer module. With capabilities like these becoming the norm, is it time to take a closer look at the threat Mobile Malware could pose to enterprise networks?
North Korean hackers have demonstrated yet again that they’re tracking and integrating the latest techniques, and investing in malware development. A recent campaign saw eight new pieces of malware distributed throughout the kill chain, leveraging #Microsoft #InTune to deliver payloads and an in-memory dropper to abuse the #BYOVD technique and evade EDR solutions.
A joint investigation by #Mandiant and #SonicWall has unearthed a two-year campaign by Chinese actors, enabled through exploitation of unpatched SMA100 appliances and delivery of tailored payloads. A critical vulnerability reported by #Fortinet this week helps reinforce the point that perimeter devices need to be patched with urgency, as it’s a well-documented target for Chinese-affiliated actors.
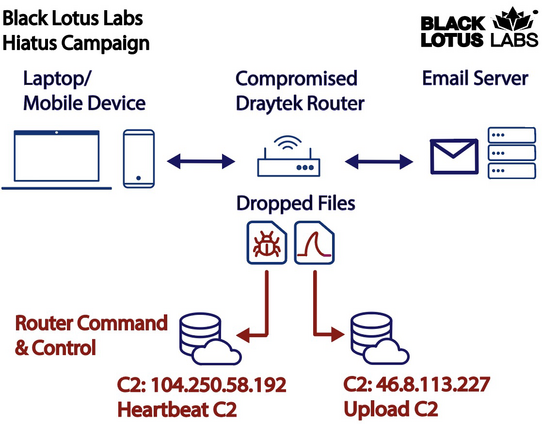
#HiatusRAT is a novel malware targeting #DrayTek routers, sniffing network traffic and proxying C2 traffic to forward-deployed implants. TTPs employed in recent #BatLoader and #Qakbot campaigns are also worth taking note of, as is #GoBruteforcer, a new malware family targeting specific web server applications to brute force logins and deploy an IRC bot for C2.
Those in Vulnerability Management should take particular note of the #Veeam vulnerability, which appears trivial to exploit and actually delivers plaintext credentials to the attacker. CISA have also taken note of nearly 40k exploit attempts of a 2 year old code-exec-as-root vulnerability in the #VMWare Cloud Foundation product in the last two months, so make sure you’re patched against it.
#Redteam members have some excellent reading to look forward to, looking at HTTP request smuggling to harvest AD credentials and persisting with a MitM Exchange server, as well as a detailed post that examines #CobaltStrike’s reflective loading capability;
The #blueteam has some great tradecraft tips from @inversecos on #Azure DFIR, as well as tools to help scan websites for malicious objects, and to combat the new #Stealc #infostealer and well-established Raccoon Stealer.
Catch all this and much more in this week's newsletter:
https://opalsec.substack.com/p/soc-goulash-weekend-wrap-up-09e?sd=pf
#infosec #cyber #news #cybernews #infosec #infosecnews #informationsecurity #cybersecurity #newsletter #hacking #security #technology #hacker #vulnerability #vulnerabilities #malware #ransomware #dfir #soc #threatintel #threatintelligence #DarkWeb #mdm #dprk #FortiOS #FortiProxy
#emotet #android #microsoft #intune #byovd #mandiant #sonicwall #fortinet #hiatusrat #draytek #batloader #qakbot #gobruteforcer #veeam #vmware #redteam #cobaltstrike #blueteam #azure #stealc #infostealer #infosec #cyber #news #cybernews #infosecnews #informationsecurity #cybersecurity #newsletter #hacking #security #technology #hacker #vulnerability #vulnerabilities #malware #ransomware #dfir #soc #threatintel #threatintelligence #darkweb #mdm #dprk #fortios #FortiProxy
Josh Lemon · @joshlemon
134 followers · 39 posts · Server infosec.exchangeToo often I think organizations focus on only protecting compute endpoints. This is a good reminder #APT #ThreatActors do still like to #compromise network devices.
Nice write up on #HiatusRAT #malware compromising routers.
#DFIR #NetworkForensics
https://blog.lumen.com/new-hiatusrat-router-malware-covertly-spies-on-victims/
#apt #threatactors #compromise #hiatusrat #malware #dfir #networkforensics
IT News · @itnewsbot
2975 followers · 251891 posts · Server schleuss.onlineThreat actors are using advanced malware to backdoor business-grade routers - Enlarge (credit: Getty Images)
Researchers have uncovered adva... - https://arstechnica.com/?p=1922180 #remoteaccesstrojan #hiatusrat #biz #email
#email #biz #hiatusrat #remoteaccesstrojan
Tech news from Canada · @TechNews
326 followers · 8819 posts · Server mastodon.roitsystems.caArs Technica: Threat actors are using advanced malware to backdoor business-grade routers https://arstechnica.com/?p=1922180 #Tech #arstechnica #IT #Technology #remoteaccesstrojan #hiatusrat #Biz&IT #email
#Tech #arstechnica #it #technology #remoteaccesstrojan #hiatusrat #biz #email
crudd · @crudd
83 followers · 145 posts · Server hackers.townNew research on a #router campaign we are calling #Hiatus that we suspect has been active for years, as we recently discovered variant 1.5 of the #malware.
This campaign consists of two modules. The first is a variant of #TCPDump designed to passively collect email traffic as it transits through the routers. The second module #HiatusRAT, turns the router into a covert relay to #proxy commands and exfil.
https://blog.lumen.com/new-hiatusrat-router-malware-covertly-spies-on-victims/
#proxy #hiatusrat #tcpdump #malware #hiatus #router
Danny Adam · @dadamitis
7 followers · 3 posts · Server infosec.exchangeToday we’re releasing research on brand new activity cluster we’re calling #HiatusRat. This actor has an affinity for target routers, to gather pcap and use as covert infrastructure.