IT News · @itnewsbot
3603 followers · 269937 posts · Server schleuss.onlineUsing JTAG To Dump the Xbox’s Secret Boot ROM - When Microsoft released its first entry into the video game console market with th... - https://hackaday.com/2023/08/11/using-jtag-to-dump-the-xboxs-secret-boot-rom/ #hackingthexbox #interposer #xboxhacks #jtag #xbox
#xbox #jtag #xboxhacks #interposer #hackingthexbox
RevK :verified_r: · @revk
2073 followers · 7248 posts · Server toot.me.ukThis fun.
It looks like ESP32-S3 has USB JTAG, on by default, yay.
It even has OpenOCD pre-installed as a tool.
Just sparse on the actual instructions to use it.
What I am trying to do is flash via JTAG (via USB), which I am hoping I can do without having to bugger with GPIO0 first!
#ESP32 #esp32s3 #jtag #usb #openocd
Randy Widell ®️ · @randywidell
1 followers · 65 posts · Server twit.socialShould be getting a FTDI FT4232H module tomorrow for #jtag debugging hardware AFTER figuring out where my #rust #raspberrypi kernel was trapping. Onward and forward implementing a Buddy page allocator and Slab kernel object allocator. Have a pretty good idea what a basic driver interface is going to look like.
Randy Widell ®️ · @randywidell
1 followers · 64 posts · Server twit.socialAnyone have any good #jtag suggestions for #raspberrypi debug probe? The Black Magic probe doesn’t support #aarch64. A J-link is a bit much for just messing around.
Renaud Lifchitz :verified: · @nono2357
259 followers · 1695 posts · Server infosec.exchangeRT @nedos
Excited to be announcing our FIRST FREE WEBINAR of 2023. It'll be on JTAG vs. SWD. The differences as well as some of our favorite JTAG programmers. https://webinar.advancedsecurity.training/webinar-jtag-vs-swd/ #webinar #jtag #swd #hardwarehacking #embeddedsecurity
#webinar #jtag #swd #hardwarehacking #embeddedsecurity
GeekProjects News · @news
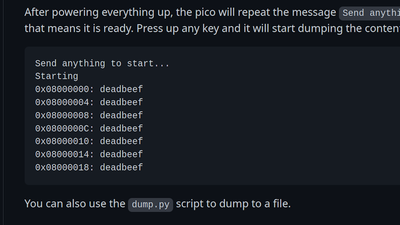
1 followers · 2084 posts · Server geekprojects.comNeed To Dump A Protected STM32F0x? Use Your Pico! https://hackaday.com/2023/02/05/need-to-dump-a-protected-stm32f0x-use-your-pico/ #ReverseEngineering #reverseengineering #hardwarehacking #SecurityHacks #fuzzing #rp2040 #stm32 #jtag
#ReverseEngineering #hardwarehacking #SecurityHacks #fuzzing #rp2040 #stm32 #jtag
IT News · @itnewsbot
2858 followers · 248642 posts · Server schleuss.onlineNeed To Dump A Protected STM32F0x? Use Your Pico! - Sometimes, security mechanisms can be bypassed if you just do things slightly out ... - https://hackaday.com/2023/02/05/need-to-dump-a-protected-stm32f0x-use-your-pico/ #reverseengineering #hardwarehacking #securityhacks #fuzzing #rp2040 #stm32 #jtag
#jtag #stm32 #rp2040 #fuzzing #securityhacks #hardwarehacking #reverseengineering
Garrett · @gtr
57 followers · 75 posts · Server infosec.exchangeIs Bus Pirate dead? The newest firmware fork I found is 2y old, and they're out of stock on seeedstudio. Do folks use J-Links these days instead to #JTAG things?
Relatedly, it seems like the J-Link EDU is out of stock, but the BASE is available. Convenient!
https://www.segger.com/products/debug-probes/j-link/models/j-link-edu/
Éric Freyssinet · @ericfreyss
1973 followers · 750 posts · Server mastodon.socialRT a video by @getorix@twitter.com (via @magnetic_tape) "Following #JTAG scraping video @HackingThings posted recently. What if there is RAM on top? Well, I just tried another approach and it also works 😉"
Impressive precision JTAG job.
HellPie · @hellpie
19 followers · 421 posts · Server raru.reIf I see one more #JTAG connector I will have a mental breakdown and I stg I will rip every old MacBook on sight and crush it until I can rip that disgraceful port off of its board.
Rebecca Cran · @bexcran
206 followers · 91 posts · Server octodon.socialDoing #firmware development with a purpose-built #arm #DeveloperKit like this #nvidia Orin is so much less stressful compared to using consumer devices and swapping micro-SD cards etc.!
With this I can run ‘./flash.sh’ from my development machine and the new firmware gets signed, bundled and flashed, the system reboots and I can see the firmware messages across two UARTS. If I need to #debug it further, I can plug into the #jtag port on the bottom and step through the code.
#firmware #arm #DeveloperKit #nvidia #debug #jtag
CK's Technology News · @CKsTechNews
1667 followers · 1103 posts · Server cktn.todon.de#Scraping the #SoC to expose #JTAG pads on the package
https://twitter.com/hackingthings/status/1605684402373156864
RT @HackingThings@twitter.com
Yeah, let me just scrape the SOC to expose JTAG pads on the package…
🐦🔗: https://twitter.com/HackingThings/status/1605684402373156864
IT News · @itnewsbot
1945 followers · 239691 posts · Server schleuss.onlineReverse Engineering Reveals EV Charger Has a Sense of Security - As more and more electric vehicles penetrate the market, there’s going to have to ... - https://hackaday.com/2022/11/16/reverse-engineering-reveals-ev-charger-has-a-sense-of-security/ #reverseengineering #electricvehicle #armcortex-a7 #nandflash #teardown #charger #jtag #uart #ev
#ev #uart #jtag #charger #teardown #nandflash #armcortex #electricvehicle #reverseengineering
GeekProjects News · @news
1 followers · 281 posts · Server geekprojects.comReverse Engineering Reveals EV Charger Has a Sense of Security https://hackaday.com/2022/11/16/reverse-engineering-reveals-ev-charger-has-a-sense-of-security/ #ReverseEngineering #reverseengineering #electricvehicle #ARMCortex-A7 #NANDflash #teardown #charger #jtag #uart #ev
#ReverseEngineering #electricvehicle #ARMCortex #NANDflash #teardown #charger #jtag #uart #ev
Tech News Worldwide · @TechNews
11787 followers · 98463 posts · Server aspiechattr.meReverse Engineering Reveals EV Charger Has a Sense of Security
https://hackaday.com/2022/11/16/reverse-engineering-reveals-ev-charger-has-a-sense-of-security/
#ReverseEngineering #reverseengineering #electricvehicle #ARMCortex-A7 #NANDflash #teardown #charger #jtag #uart #ev
#reverseengineering #electricvehicle #ARMCortex #NANDflash #teardown #charger #jtag #uart #EV
Psolyca · @psolyca
6 followers · 14 posts · Server fosstodon.org#jtag probing on #tf101, not standard.
Can we get Secure Boot Key v2 and be able to boot #postmarketos from eMMC? We will see.
CNX Software · @cnxsoft
267 followers · 528 posts · Server noc.socialInexpensive tiny @WCH_TECH CH347 board acting as a USB 2.0 to UART, I2C, SPI, #JTAG, and/or GPIO bridge. #electronics #debugging
https://www.cnx-software.com/2022/09/01/5-ch347-board-is-a-usb-2-0-bridge-to-i2c-spi-uart-jtag-and-gpio/
Original tweet : https://twitter.com/cnxsoft/status/1565280141541982208
RISC-V · @risc_v
311 followers · 1662 posts · Server noc.socialRT from CNX Software (@cnxsoft)
.@SipeedIO's new variant of their @AllwinnerTech D1 RISC-V #SBC with MIPI LCD connector, two microphones, and a built-in #JTAG and UART debugger. #riscv #linux #openwrt #debian
https://www.cnx-software.com/2022/06/21/sipeed-lichee-rv-dock-pro-risc-v-sbc-adds-mipi-rgb-lcd-connector-dual-mic-and-bl702-jtaguart-debugger/
Original tweet : https://twitter.com/cnxsoft/status/1539175399661326336
#sbc #jtag #riscv #linux #openwrt #debian
CNX Software · @cnxsoft
267 followers · 528 posts · Server noc.social.@SipeedIO's new variant of their @AllwinnerTech D1 RISC-V #SBC with MIPI LCD connector, two microphones, and a built-in #JTAG and UART debugger. #riscv #linux #openwrt #debian
https://www.cnx-software.com/2022/06/21/sipeed-lichee-rv-dock-pro-risc-v-sbc-adds-mipi-rgb-lcd-connector-dual-mic-and-bl702-jtaguart-debugger/
Original tweet : https://twitter.com/cnxsoft/status/1539175399661326336
#sbc #jtag #riscv #linux #openwrt #debian
CNX Software · @cnxsoft
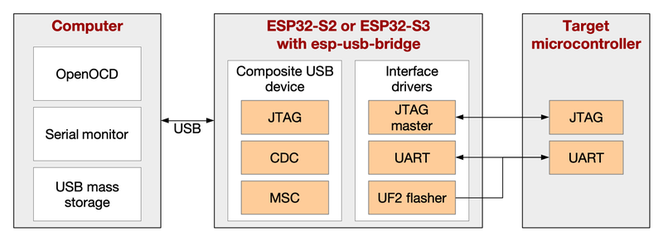
267 followers · 528 posts · Server noc.socialEspressif Systems has released a project to use compatible #ESP32-S2 or ESP32-S3 boards as USB to UART or USB to #JTAG debug boards. #debugging #opensource #firmware
https://www.cnx-software.com/2022/04/15/esp-usb-bridge-project-converts-esp32-s2-or-esp32-s3-into-a-usb-to-uart-jtag-chip/
Original tweet : https://twitter.com/cnxsoft/status/1514811360403935235
#esp32 #jtag #debugging #opensource #firmware