Arthur Lutz (Zenika) · @arthurzenika
367 followers · 584 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
That's it, remember to have fun while learning all this security stuff, don't be too competitive, share with your peers and stay humble.
End of 🧵
#kubeconctf #kubeconeu #kubecon
Arthur Lutz (Zenika) · @arthurzenika
367 followers · 583 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
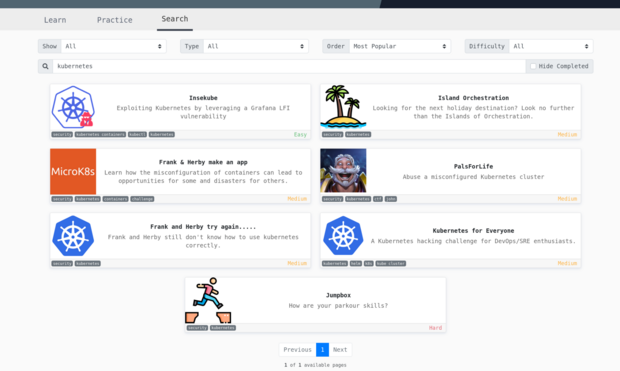
Another thing I might try to do is spend some time on the kubernetes rooms on TryHackMe https://tryhackme.com/hacktivities?tab=search&page=1&free=all&order=most-popular&difficulty=all&type=all&searchTxt=kubernetes
#kubeconctf #kubeconeu #kubecon
Arthur Lutz (Zenika) · @arthurzenika
367 followers · 582 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
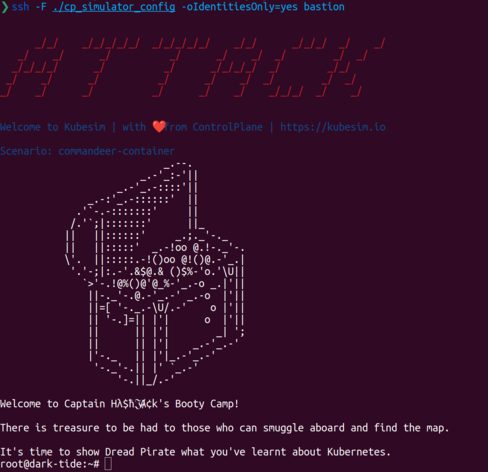
So it was quite fun for a first k8s CTF, although I regret not focusing more on the task at hand. On the failed routes I learned a bunch of things and tried a bunch of new tools which was cool. Thanks for the setup and the fun 🏴☠️ scenario !
I believe the setup was done with https://github.com/controlplaneio/simulator which is open source so I might find the time to explore more.
https://github.com/madhuakula/kubernetes-goat might be another was to practice a bit more of this type of challenges.
#kubeconctf #kubeconeu #kubecon
Arthur Lutz (Zenika) · @arthurzenika
367 followers · 581 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
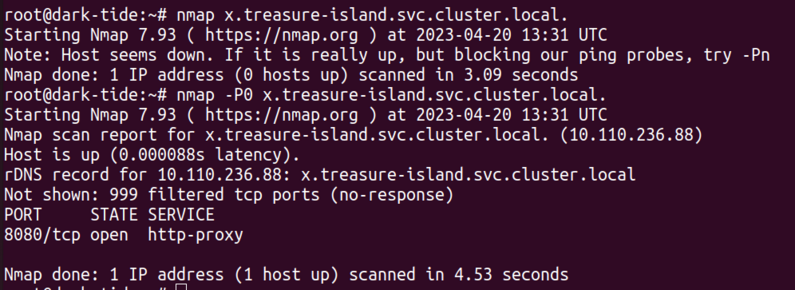
One of the exploration tools I had used had found a service in the DNS, so nmap got me the port, curl told me there was a /login redirect, time to try that password there. First attempt failed, and then time was up, the environment got deleted and I got disconnected (CTF was time boxed) ⌛... shame shame. But that's the rules of the game.
#kubeconctf #kubeconeu #kubecon
Arthur Lutz (Zenika) · @arthurzenika
367 followers · 580 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
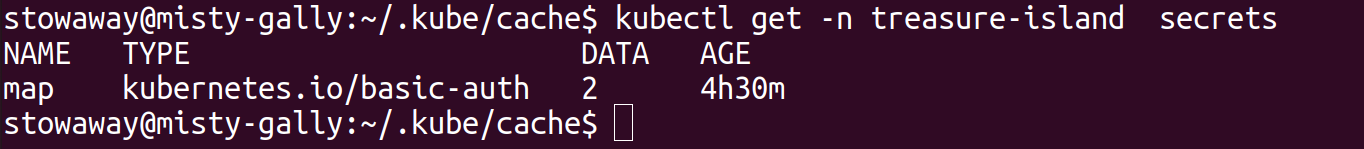
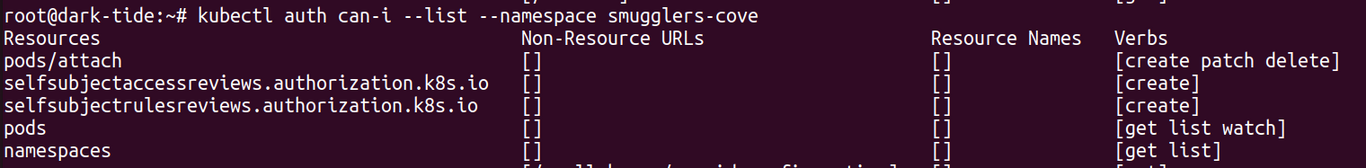
Next step was to go at "kubectl auth can-i" again with the namespaces found in the first pod. I found I could look for Secrets in the other namespace so I got them there, "base64 -d" later I had a user and a password. What service should I use them against ?
#kubeconctf #kubeconeu #kubecon
Arthur Lutz (Zenika) · @arthurzenika
367 followers · 579 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
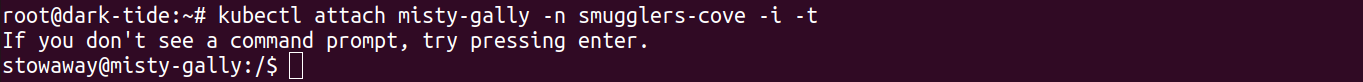
Next step was to list the pods in that namespace, and then use "kubectl attach" to get a shell in that other pod. In that pod, less permissions since the user was not root.
#kubeconctf #kubeconeu #kubecon
Arthur Lutz (Zenika) · @arthurzenika
367 followers · 578 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
Then you're off to find a flag. Enumation, evasion, esclation, escaping, etc. I checked a bunch of things (but won't go into all the failed explorations). Being root in the pod enabled me to install a few tools, "kubectl get ns" got me the other namespaces available, then "kubectl auth can-i --list" got me some hints as to what was possible with the service account at hand.
#kubeconctf #kubeconeu #kubecon
Arthur Lutz (Zenika) · @arthurzenika
367 followers · 577 posts · Server pouet.chapril.org#KubeCon #KubeConEU #KubeConCTF
So you start off on the following page https://controlplaneio.github.io/kubecon-eu-2023-ctf/ with some instructions, you need to join the CNCF Slack, then a #kubecon23-ctf room, then ping the CTF TaskMaster which sends you a tgz with some ssh configuration files. The setup is described in detail on https://controlplaneio.github.io/kubecon-eu-2023-ctf/setup/
#kubecon23 #kubeconctf #kubeconeu #kubecon