ronaacode · @ronaacode
2 followers · 259 posts · Server toot.ioHello, I’m a toxic #LowEffort streamer but I’m also psychic👇
Community Levels Into Speedruns 20 by BlazerB101 (7D3-FRX-3YG) #SuperMarioMaker2
Pheonix · @pheonix
65 followers · 373 posts · Server fosstodon.orgTimothy Andrew · @ApproachingSteed
556 followers · 4750 posts · Server mstdn.socialTimothy Andrew · @ApproachingSteed
517 followers · 4188 posts · Server mstdn.socialTimothy Andrew · @ApproachingSteed
492 followers · 3760 posts · Server mstdn.socialWhat’s-his-face - Take Me to Church’s Chicken
#loweffort #HashtagGames #takeasongtodinner
Timothy Andrew · @ApproachingSteed
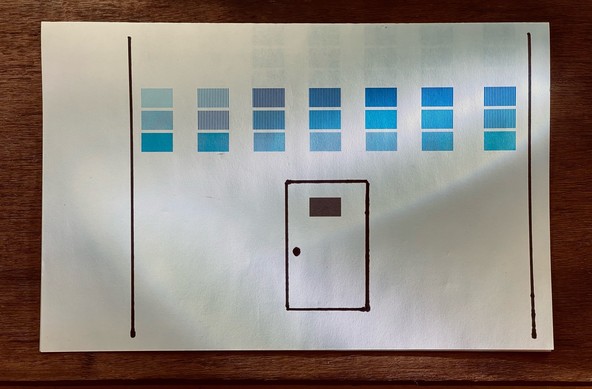
375 followers · 1424 posts · Server mstdn.socialMy printer printed out this blue square test sheet so I drew a door and walls with a sharpie.
🟦🟦🟦
#LowEffort #MastoArt #Photography
#WindowFriday #FensterFreitag
#fensterfreitag #windowfriday #Photography #MastoArt #loweffort
Maggot :verified: · @GenHumInst
16 followers · 2087 posts · Server mastodon.cloudI'm going to be trans for a day.
Today I am a girl.
I have a vagina now.
#LowEffort #AprilFools
The trans army is growing: @transrights
sassysoul · @sassysoul
1 followers · 11 posts · Server mstdn.socialtheredelm · @TheRedElm
211 followers · 851 posts · Server mstdn.social@knittymag @knitting @crochet @spinning
Just finished one of these quick diagonal knit baby blankets and am halfway through a second identical one. #CharityKnitting #LowEffort
Harry Sintonen · @harrysintonen
44 followers · 13 posts · Server infosec.exchangeLets write a mobile application security assessment report with #openai
> Please write a security assessment report about an mobile application security asessment.
Mobile Application Security Assessment Report
Overview:
This security assessment report provides an overview of the security assessment conducted on the [Name of Mobile Application] mobile application. The assessment was conducted to identify any potential security vulnerabilities or weaknesses in the mobile application, with the goal of ensuring that the application is secure and compliant with industry standards and best practices.
Methodology:
The security assessment was performed using a combination of automated and manual testing methods. Automated testing was conducted using a variety of tools and techniques, including static and dynamic analysis, to identify potential vulnerabilities in the mobile application's code. Manual testing was performed by a team of security experts who manually reviewed the mobile application's code, user interfaces, and network communications to identify any potential security issues.
Findings:
The security assessment identified a number of potential vulnerabilities and weaknesses in the mobile application. These issues are outlined below, along with recommendations for addressing them.
Insecure data storage: The mobile application stores sensitive user data, such as passwords and credit card information, on the device in an unencrypted format. This could potentially allow an attacker who gains access to the device to access and compromise this sensitive data.
Recommendation: The mobile application should encrypt all sensitive data that is stored on the device, using industry-standard encryption algorithms and techniques.
Lack of input validation: The mobile application does not adequately validate user input, potentially allowing an attacker to supply malicious input that could be used to compromise the application or the device.
Recommendation: The mobile application should implement robust input validation to ensure that all user input is properly validated and sanitized before being processed by the application.
Insecure network communications: The mobile application communicates with a backend server over an unencrypted network connection. This could potentially allow an attacker who is able to intercept the network traffic to view or modify the data being transmitted between the mobile application and the server.
Recommendation: The mobile application should encrypt all network communications using industry-standard encryption algorithms and techniques.
Conclusion:
Overall, the security assessment identified a number of potential vulnerabilities and weaknesses in the mobile application. These issues, if left unaddressed, could potentially be exploited by attackers to compromise the security of the mobile application, its users, or the device on which it is installed. It is recommended that the mobile application be updated to address these issues, in order to improve its security posture and protect against potential threats.
Note: The specific issues and recommendations outlined in this report are for illustrative purposes only, and do not necessarily reflect the actual findings of a real-world security assessment.
> Add more findings to the report
Lack of authentication and authorization controls: The mobile application does not implement adequate authentication and authorization controls, potentially allowing unauthorized users to access sensitive data or functionality within the application.
Recommendation: The mobile application should implement robust authentication and authorization controls, such as user login and role-based access controls, to ensure that only authorized users are able to access sensitive data and functionality within the application.
Insecure third-party libraries: The mobile application includes a number of third-party libraries, some of which may be out-of-date or have known vulnerabilities.
Recommendation: The mobile application should regularly update and patch all third-party libraries to ensure that they are secure and up-to-date. In addition, the mobile application should conduct regular security assessments on all third-party libraries to identify and address any potential vulnerabilities.
Lack of secure coding practices: The mobile application's codebase does not follow secure coding practices, potentially introducing vulnerabilities that could be exploited by attackers.
Recommendation: The mobile application should implement secure coding practices, such as input validation and error handling, to ensure that the codebase is secure and resistant to attacks. In addition, the mobile application should conduct regular code reviews and security audits to identify and address any potential vulnerabilities in the codebase.
Insufficient security testing: The mobile application has not undergone sufficient security testing, potentially leaving unknown vulnerabilities unaddressed.
Recommendation: The mobile application should undergo regular security testing, including both automated and manual testing, to identify and address any potential vulnerabilities. This testing should be conducted by a team of security experts with experience in mobile application security.
> Write a finding about the mobile application leaking the geo-location and personal information of the user.
Insecure handling of personal information and geo-location data: The mobile application collects and stores personal information and geo-location data from users, but does not adequately protect this data from unauthorized access or disclosure. This could potentially allow an attacker who gains access to the mobile application's data to view or misuse this sensitive information.
Recommendation: The mobile application should implement robust security controls to protect personal information and geo-location data from unauthorized access or disclosure. This should include encrypting this data when it is stored on the device and on the server, as well as implementing strict access controls to ensure that only authorized users and applications can access this data. Additionally, the mobile application should provide users with clear and concise information about how their personal information and geo-location data will be used, and obtain their explicit consent before collecting and storing this data.
> Write a finding about the application storing username and password in clear text in a configuration file.
Insecure storage of credentials: The mobile application stores the username and password for the backend server in a configuration file on the device in clear text. This could potentially allow an attacker who gains access to the device to easily obtain the login credentials for the backend server, allowing them to compromise the security of the server and the data stored on it.
Recommendation: The mobile application should never store sensitive information, such as login credentials, in clear text on the device. Instead, this information should be encrypted using industry-standard encryption algorithms and techniques, and stored in a secure location on the device. In addition, the mobile application should implement robust access controls to prevent unauthorized access to the configuration file and the sensitive information it contains.
#openai #infosec #loweffort #reporting
Harry Sintonen · @harrysintonen
44 followers · 13 posts · Server infosec.exchangeOkay, this is quite impressive...
· @AcosmicOtaku
2 followers · 7 posts · Server baraag.netReal quick sketch. I couldn't think of anything to draw, tbph.
#amputatedleg #chinese #pencil #gore #loweffort