invoke-eric · @invoke_eric
5 followers · 2 posts · Server infosec.exchangeThe registrant "genafontc" appears to be shared by some #NetSupportRAT #c2 domains like manigiajabae32[.]com
ktalarisa18[.]com
aonukanand11[.]com
Brad · @malware_traffic
2180 followers · 97 posts · Server infosec.exchange2023-01-18 (Wednesday) - malspam pushes #NetSupportRAT - Saw many of the same IOCs last month, reported at: https://github.com/pan-unit42/tweets/blob/master/2022-12-28-IOCs-for-NetSupport-RAT-infection.txt
Email attachment (zip archive) available at: https://bazaar.abuse.ch/sample/be7b369ed7aa9ed4943736b5b84277b000f3923a5794d596629deb3e41701d59/
Last month, it was a link to download the zip archive. This month, the zip archive is an attachment. Otherwise, same infection traffic.
da_667 · @da_667
3307 followers · 142 posts · Server infosec.exchangeFound this article in my threat intel feed:
https://asec.ahnlab.com/en/45312/
Looks like NetSupport RAT?
C2 domain/port: tradinghuy.duckdns[.]org:1488.
We have rules in the ETOPEN ruleset to catch NetSupport CnC Checkin, and the response from the server:
2035892 (NetSupport Remote Admin Checkin)
2035895 (NetSupport Remote Admin Response)
#threatintel #malware #netsupportrat #snort #suricata #iocsharing #ioc
#threatintel #malware #netsupportrat #snort #suricata #iocsharing #ioc
Brad · @malware_traffic
1958 followers · 65 posts · Server infosec.exchangeAvailable at: https://malware-traffic-analysis.net/2022/12/28/index.html
- Traffic from #pcap (two split pcaps) of the infection
- A Fiddler capture for traffic leading to an initial zip download
- USPS-themed #malspam example
- Some malware/artifacts from this #NetSupportRAT infection
Brad · @malware_traffic
1958 followers · 65 posts · Server infosec.exchangeTweet I wrote for: https://twitter.com/Unit42_Intel/status/1608185209329008641
2022-12-28 (Wednesday): USPS-themed #malspam pushing #NetSupportRAT - Some indicators available at: https://github.com/pan-unit42/tweets/blob/master/2022-12-28-IOCs-for-NetSupport-RAT-infection.txt
If I get the time, I'll post a blog for some of the malware/artifacts/traffic. You know the deal....
Jérôme Segura · @malwareinfosec
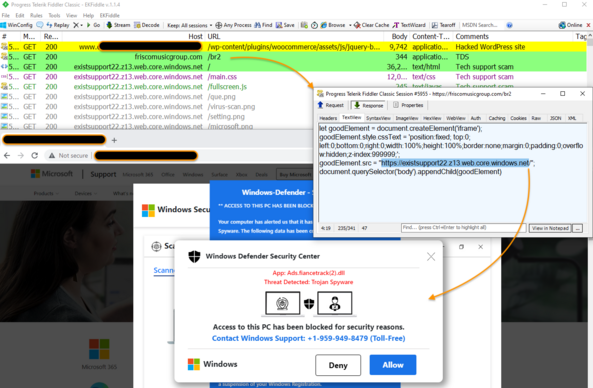
174 followers · 22 posts · Server infosec.exchangeThe #sczriptzzbn campaign which normally delivers #netsupportRAT, #solarmarker or #icedID is currently redirecting to a tech support scam :blobeyes:
friscomusicgroup[.]com/br2
existsupport22[.]z13[.]web[.]core[.]windows[.]net
#sczriptzzbn #netsupportrat #solarmarker #icedid
ITSEC News · @itsecbot
687 followers · 32461 posts · Server schleuss.online‘Coronavirus Report’ Emails Spread NetSupport RAT, Microsoft Warns - Attackers used malicious Excel 4.0 documents to spread the weaponized NetSupport RAT in a spear-ph... more: https://threatpost.com/coronavirus-emails-netsupport-rat-microsoft/156026/ #microsoftsecurityintelligence #remoteaccesstool #netsupportrat #spearphishing #websecurity #coronavirus #microsoft #covid-19 #excel4.0
#excel4 #covid #microsoft #coronavirus #websecurity #spearphishing #netsupportrat #remoteaccesstool #microsoftsecurityintelligence