· @kioan
26 followers · 84 posts · Server mastodon.socialAnother #phishing campaign trying to trick users into supplying their credentials:
🎣https[:]//jccm.com[.]ve/camezs/MailUpdateFresh/index.html
📧email via mail9.uitech[.]jp
☁️hosted by @Cloudflare
Webserver #opendir shows multiple phishing sites.
#phishing #opendir #infosec #cybersecurity #ioc
StalkPhish · @stalkphish_io
17 followers · 17 posts · Server infosec.exchangeHive... again!
Detected by Stalkphish.io
Targeting @USPS @swisspost
#phishingkit #phishing #soc
#cybersecurity #scam #stalkphish #opendir
#phishingkit #phishing #soc #cybersecurity #scam #stalkphish #opendir
James_inthe_box · @james_inthe_box
213 followers · 58 posts · Server infosec.exchange
Malwar3Ninja | Threatview.io · @Malwar3Ninja
122 followers · 41 posts · Server infosec.exchange[Threatview.io ] 🔥 Our latest collection on #virustotal using telemetry gathered through our proactive hunter "Peaking inside an malicious host using #opendir on "37.77.239[.]239"
⚠️ Previously #QakBot & #Redline C2 were hosted on the IP
⚠️#Ransomware
⚠️#Hacktools
#virustotal #opendir #qakbot #redline #ransomware #hacktools #threatintel #dfir
Malwar3Ninja | Threatview.io · @Malwar3Ninja
106 followers · 33 posts · Server infosec.exchange[Threatview.io ] 🔥 Our latest collection on #virustotal using telemetry gathered through our proactive hunter "Peaking inside toolkit of #MedusaLokcker using #opendir on 95.213.145[.]101"
#threatintel
#DFIR
#cobaltstrike
⚠️PoshC2
⚠️Netscan
⚠️Mimikatz
⚠️ PowerShell
#virustotal #medusalokcker #opendir #threatintel #dfir #cobaltstrike
Malwar3Ninja | Threatview.io · @Malwar3Ninja
106 followers · 33 posts · Server infosec.exchange[Threatview.io ] 🔥 Our latest collection on #virustotal using telemetry gathered through our proactive hunter "Peaking inside toolkit of #MedusaLokcker using #opendir on "62.182.159[.]147"
⚠️Mimikatz
⚠️Netscan
⚠️PoshC2
⚠️Cobaltstrike
⚠️Netscan
⚠️Historic detections on host also shows use of #Mythic C2 along with #Cobaltstrike
#virustotal #medusalokcker #opendir #mythic #cobaltstrike #threatintel #dfir #cybersecurity #threatintelligence #poshc2
James_inthe_box · @james_inthe_box
183 followers · 52 posts · Server infosec.exchange
· @kioan
5 followers · 15 posts · Server mastodon.social· @kioan
5 followers · 22 posts · Server mastodon.social· @kioan
5 followers · 14 posts · Server mastodon.socialavc · @avc
5 followers · 5 posts · Server infosec.exchangeavc · @avc
5 followers · 5 posts · Server infosec.exchangeGerald @ Simply Cyber :verified: · @Gerald_Auger
72 followers · 12 posts · Server infosec.exchangeQuite a repo, and cobaltstrike to boot. I'm aware of opendir but don't really run in those circles so just asking/guessing. Thx.
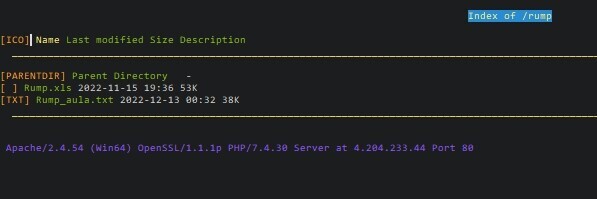
Oliver Hough · @olihough86
12 followers · 875 posts · Server infosec.exchangeMulti Service Phishing page & kit
hxxps://aptitudelyfit.in/wp-includes/Mercy/SYNCDATA/login.php
Kit in #opendir hxxps://aptitudelyfit.in/wp-includes/Mercy/
Actor email: Allahmercyisreal@gmail.com
Oliver Hough · @olihough86
12 followers · 875 posts · Server infosec.exchange#GodzillaLoader complete with manual in Russian #OpenDir
hxxp://qwerkkc.ru/