ITSEC News · @itsecbot
1240 followers · 34532 posts · Server schleuss.online#IdentityManagementDay - Best Practices to Help Keep Your Organization Secure - By Chinatu Uzuegbu, CISSP, CEO/Managing Cyber Security Consultant at RoseTech Cyb... https://blog.isc2.org/isc2_blog/2023/04/identitymanagementday-best-practices.html #cybersecurityworkforce #operationssecurity #networksecurity #itsecurity #ransomware #privacy #risk
#risk #privacy #ransomware #itsecurity #networksecurity #operationssecurity #cybersecurityworkforce #IdentityManagementDay
ITSEC News · @itsecbot
1234 followers · 34491 posts · Server schleuss.onlinePush Notification Is More Secure Than SMS 2FA, So Why the Reluctance to Enable It? - Forget SMS 2FA authentication – Twitter and others are making it less attractive ... https://blog.isc2.org/isc2_blog/2023/04/push-notification-is-more-secure-than-sms-2fa-so-why-the-reluctance-to-enable-it.html #operationssecurity #itsecurity
#itsecurity #operationssecurity
ITSEC News · @itsecbot
1234 followers · 34480 posts · Server schleuss.onlineLATEST CYBERTHREATS AND ADVISORIES - APRIL 7, 2023 - The U.S. government takes down another dark web forum, Western Digital suffers a ... https://blog.isc2.org/isc2_blog/2023/04/latest-cyberthreats-and-advisories-april-7-2023.html #operationssecurity #networksecurity
#networksecurity #operationssecurity
ITSEC News · @itsecbot
1235 followers · 34425 posts · Server schleuss.onlineCYBERSECURITY INDUSTRY NEWS REVIEW - APRIL 4, 2023 - UK government potentially skimps on senior cyber role salary as the NCSC calls fo... https://blog.isc2.org/isc2_blog/2023/04/cybersecurity-industry-news-review-april-4-2023.html #cybersecurityworkforce #operationssecurity #networksecurity
#networksecurity #operationssecurity #cybersecurityworkforce
Tech news from Canada · @TechNews
168 followers · 4164 posts · Server mastodon.roitsystems.caKotaku: War Thunder Players Are, Once Again, Posting Military Documents On Forums https://kotaku.com/war-thunder-military-documents-classified-leak-forum-1850009524 #gaming #tech #kotaku #internationaltrafficinarmsregulations #mcdonnelldouglasf15estrikeeagle #technology2cinternet #operationssecurity #computersecurity #militaryscience #internetforum #espionage #politics #offtopic #articles #aircraft #f16
#Gaming #Tech #kotaku #internationaltrafficinarmsregulations #mcdonnelldouglasf15estrikeeagle #technology2cinternet #operationssecurity #computersecurity #militaryscience #internetforum #espionage #politics #offtopic #articles #aircraft #f16
CryptoNewsBot · @cryptonewsbot
294 followers · 8193 posts · Server schleuss.onlineDarknet Forum Dread to Relaunch After Month-Long Downtime Due to DDOS Attack - According to web portal darkdot.com and anonymous journalist Darkdotfail, the popu... - https://news.bitcoin.com/darknet-forum-dread-to-relaunch-after-month-long-downtime-due-to-ddos-attack/ #criticalsourceoftruth #anonymousjournalist #operationssecurity #freedomofspeech #specificvendors #stealthdelivery #dreadforumdown #darknetmarket #@darkdotfail #darkdot.com #dreadforum #hugbunter #downtime #darknet #offline
#offline #darknet #downtime #hugbunter #dreadforum #darkdot #darknetmarket #dreadforumdown #stealthdelivery #specificvendors #freedomofspeech #operationssecurity #anonymousjournalist #criticalsourceoftruth
ITSEC News · @itsecbot
1061 followers · 32934 posts · Server schleuss.onlineSSCP Members – We Need Your Input - The SSCP certification is held by more than 7,000 professionals around the world. ... https://blog.isc2.org/isc2_blog/2022/12/sscp-members-we-need-your-input.html #cybersecuritycertifications #operationssecurity #networksecurity #itsecurity
#itsecurity #networksecurity #operationssecurity #cybersecuritycertifications
ITSEC News · @itsecbot
856 followers · 32559 posts · Server schleuss.onlineLATEST CYBERTHREATS AND ADVISORIES - SEPTEMBER 23, 2022 - Cyberattacks on the video game industry, big-name brand data breaches and the Tea ... https://blog.isc2.org/isc2_blog/2022/09/latest-cyberthreats-and-advisories-september-23-2022.html #operationssecurity #ransomware #risk
#risk #ransomware #operationssecurity
ITSEC News · @itsecbot
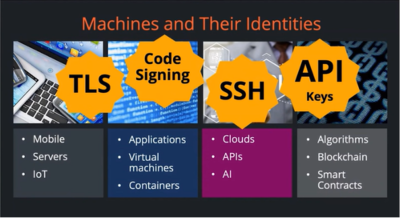
856 followers · 32559 posts · Server schleuss.online(ISC)² and Venafi Explore The Strange New World of Machine Identity Management - Earlier this year, (ISC)² hosted a webinar about a new kind of challenge facing cy... https://blog.isc2.org/isc2_blog/2022/09/machine-identity-management.html #softwaredevelopment #operationssecurity #risk
#risk #operationssecurity #softwaredevelopment
ITSEC News · @itsecbot
856 followers · 32559 posts · Server schleuss.onlineThe ‘Hottest’ IT Security Technologies in 2022 - Did you catch The ‘Hottest’ IT Security Technologies in 2022 webinar? If not, we a... https://blog.isc2.org/isc2_blog/2022/08/the-hottest-it-security-technologies-in-2022.html #cybersecurityworkforce #softwaredevelopment #operationssecurity #networksecurity
#networksecurity #operationssecurity #softwaredevelopment #cybersecurityworkforce
ITSEC News · @itsecbot
856 followers · 32559 posts · Server schleuss.onlineEffective Security Using Zero Trust Architecture - By Jagadish Paranthaman, CISSP, Global Cybersecurity Solutions Architect at Avanad... https://blog.isc2.org/isc2_blog/2022/08/effective-security-using-zero-trust-architecture.html #operationssecurity #networksecurity
#networksecurity #operationssecurity
ITSEC News · @itsecbot
856 followers · 32559 posts · Server schleuss.online(ISC)² and F5 Examine OWASP’S “Top 10” Report on New Web Application Security Risks - In late 2021, the Open Web Application Security Project® (OWASP®) Foundation relea... https://blog.isc2.org/isc2_blog/2022/08/owasps-top-10-report-on-new-web-application-security-risks.html #operationssecurity #risk
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.onlineSummary of March Inside (ISC)2 Webinar: Stay Vigilant - As the war in Ukraine rages on, (ISC)² leaders took the opportunity to remind cybe... https://blog.isc2.org/isc2_blog/2022/03/summary-of-march-inside-isc2-webinar.html #cybersecurityworkforce #cybersecuritytraining #operationssecurity #networksecurity
#networksecurity #operationssecurity #cybersecuritytraining #cybersecurityworkforce
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.onlineThe Dilemma of Defense in Depth - By Ala' F. Wrikat, MSc, CISSP, CISM. Ala' is currently a specialist in policies an... https://blog.isc2.org/isc2_blog/2022/03/the-dilemma-of-defense-in-depth.html #operationssecurity #itsecurity
#itsecurity #operationssecurity
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.onlineElevating the Risk Discussion – Quantitative Analytics - By Charlene Deaver-Vazquez, CISSP, CISA. Charlene is the developer of Probabilisti... https://blog.isc2.org/isc2_blog/2022/02/elevating-the-risk-discussion-quantitative-analytics.html #operationssecurity #risk
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.onlineU.S. Cyber Command Operation Targets ‘Real-life Cyber Threats’ - A U.S. Cyber Command (USCYBERCOM) task force has conducted “its first offensive cy... https://blog.isc2.org/isc2_blog/2022/01/us-cyber-command-operation-targets-real-life-cyber-threats.html #operationssecurity #networksecurity #government #ransomware
#ransomware #government #networksecurity #operationssecurity
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.onlineDecisions, Decisions and the Role of Authorization - Technology and cybersecurity cannot be thought of as the responsibility of a siloe... https://blog.isc2.org/isc2_blog/2021/12/decisions-and-authorization.html #cybersecuritycertifications #operationssecurity
#operationssecurity #cybersecuritycertifications
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.onlinePoll Data: What CEOs Need to Know About Cybersecurity Going into 2022 - The end of the year is a good time to reflect on the past 12 months and create a p... https://blog.isc2.org/isc2_blog/2021/12/ceos-cybersecurity-2022.html #operationssecurity #ransomware
#ransomware #operationssecurity
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.online(ISC)² Celebrates Cybersecurity Awareness Month With Treasure Trove of Knowledge Building Resources - It’s October! And that can mean only one thing. It’s time to kick off the annual ... http://feedproxy.google.com/~r/isc2Blog/~3/Eyk_kLDgILk/cybersecurity-awareness-month-2021.html #operationssecurity #networksecurity #itsecurity
#itsecurity #networksecurity #operationssecurity
ITSEC News · @itsecbot
856 followers · 32557 posts · Server schleuss.onlineNational Small Business Week: 10 Best Practices for Small Business Cybersecurity - A recent survey conducted by CNBC and Momentive found that 56% of small business o... http://feedproxy.google.com/~r/isc2Blog/~3/ItAqg2IxF70/isc2-10-best-practices-for-small-business-cybersecurity.html #cybersecuritytraining #operationssecurity #networksecurity #cloudsecurity #ransomware #risk
#risk #ransomware #cloudsecurity #networksecurity #operationssecurity #cybersecuritytraining