Tae'lur Alexis :verified: · @taeluralexis
282 followers · 90 posts · Server infosec.exchangeSolved my first challenge on Portswigger #infosec #owasp #portswigger #appsec #hacking https://portswigger.net/web-security/sql-injection/lab-retrieve-hidden-data
#infosec #owasp #portswigger #appsec #hacking
Konstantin :C_H: · @kpwn
61 followers · 206 posts · Server infosec.exchange#Portswigger just updated its #WebSecAcademy with a Spring auth bypass of @PTSwarm
https://bird.makeup/users/ptswarm/statuses/1631287479604060161
#portswigger #websecacademy #infosec #cybersecurity #pentesting #bugbounty
Alexandra Beekers 🏳️🌈🌍 · @AlexandraB
51 followers · 379 posts · Server mastodon.social#CVSS system criticized for failure to address real-world impact
#cybersecurity #it #portswigger
https://portswigger.net/daily-swig/cvss-system-criticized-for-failure-to-address-real-world-impact
#cvss #cybersecurity #it #portswigger
b4nq💅🏴☠️💻 · @b4nq
20 followers · 31 posts · Server infosec.exchange#portswigger academy is fucking awesome and I recommend that to everybody who want to learn about #cybersecurity
Konstantin · @kpwn
11 followers · 48 posts · Server infosec.exchange#PortSwigger provides a practice exam. Instead of two, there is just one application to solve.
In my preparation, I failed the practice exam several times. Don‘t get discouraged when you fail, but learn from your mistakes.
https://portswigger.net/web-security/certification/practice-exam
Digital Empress :verified: · @digitalempress
405 followers · 224 posts · Server infosec.exchangeSolved: Username enumeration via response timing
#burpsuite #portswigger #owasp #appsec #studying
Digital Empress :verified: · @digitalempress
404 followers · 223 posts · Server infosec.exchangeSolved: Username enumeration via subtly different responses
#portswigger #burpsuite #appsec
rffuste · @rffuste
14 followers · 11 posts · Server infosec.exchangeHow your scanner app can be tested?
Do you want to test your brand new scanner app? How to know if the app detects the vulnerabilities it should?
Thanks to Portswigger now we have Gin and Juice Shop. This is a vulnerable web shop where your scanner app can be tested.
The application can be found here: https://ginandjuice.shop
Happy scan! 😈
https://www.rffuste.com/2023/01/23/how-your-scanner-app-can-be-tested/
#Pills #portswigger #webscan
ChickenPwny · @ChickenPwny
473 followers · 3196 posts · Server infosec.exchangeNext, is adding in #portswigger #burp into the api to make the processes even easier. XD
Digital Empress :verified: · @digitalempress
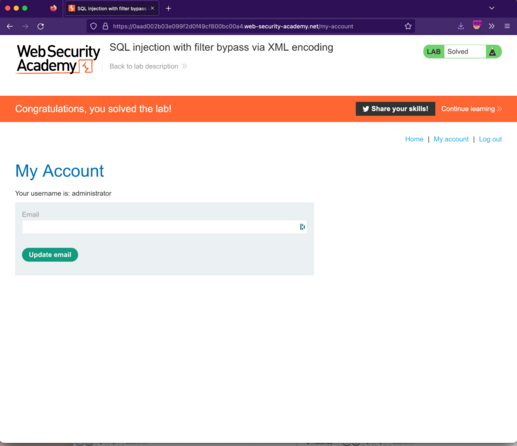
400 followers · 221 posts · Server infosec.exchangeSQL injection with filter bypass via XML encoding solved!!
#portswigger #burpsuite #appsec
Digital Empress :verified: · @digitalempress
400 followers · 220 posts · Server infosec.exchangeBlind SQL injection with out-of-band data exfiltration solved!!
#portswigger #appsec #burpsuite
Digital Empress :verified: · @digitalempress
398 followers · 218 posts · Server infosec.exchangeCompleted ✅
#burpsuite #portswigger #owasp #hacking
#burpsuite #portswigger #owasp #hacking
Digital Empress :verified: · @digitalempress
398 followers · 219 posts · Server infosec.exchangeBack to studying daily on portswigger labs. Prepare to be sick of me. #burpsuite #portswigger #appsec
#burpsuite #portswigger #appsec
n0kovo 🇩🇰:anarchy::comm::terminal::vegan::debian::python::tor::signal: · @n0kovo
462 followers · 91 posts · Server infosec.exchangeFor all my Burp Suite users on MacOS:
For all the Burp extensions that will run something "in terminal" and you want that terminal to be iTerm2, create a shell script with the following content, link it to /usr/local/bin/iterm or something, and set it as the terminal command in your Burp extensions.
Here I'm using it with the (awesome) Custom Send To extension for sending requests directly. from Burp to a number of different tools like SQLMap, Wfuzz, Gobuster etc. The script will open a new tab in iTerm and run the command specified.
You're welcome!
Script: https://gist.github.com/n0kovo/0e893c7b36f0209ffe971883064bee6f
Custom Send To:
https://github.com/bytebutcher/burp-send-to
#iterm2 #burpsuite #appsec #burp #portswigger #bugbounty #infosec #pentesting #websecurity #techtips
#iterm2 #burpsuite #appsec #burp #portswigger #bugbounty #infosec #pentesting #websecurity #techtips
Ashland.jp :verified: :nyancat: · @Ashland
38 followers · 34 posts · Server infosec.exchangePretty excited that I made it to level 8! I’ve been grinding through all of the easy rooms and it’s been so rewarding. I feel like I’m learning so much! Aside from THM I’m not sure what else to do. Maybe #portswigger or @Hacker0x01 ? So many options to choose from
Sanjaymenon :mastodon: · @sanjaymenon
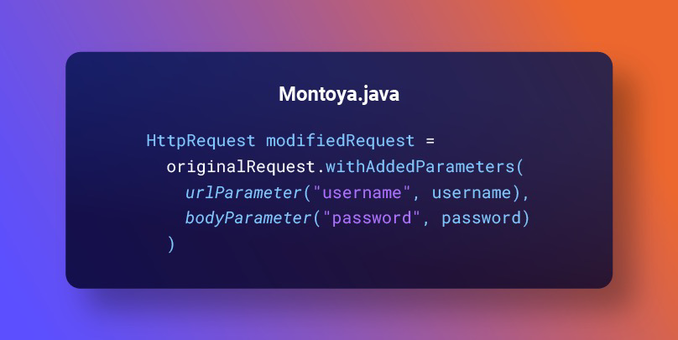
48 followers · 112 posts · Server mastodon.socialPortSwigger wants your feedback in the new Burp Suite API is codenamed "Montoya"
https://portswigger.net/blog/new-burp-suite-api-we-want-your-feedback
#api #burpsuite #portswigger #proxy #security
#API #burpsuite #portswigger #proxy #security
ChickenPwny · @ChickenPwny
416 followers · 1973 posts · Server infosec.exchangeHmmm, best way to start from nothing to doing BB. Two years of study need to study for but may not need to pass or take exam Network plus. Doing lots of ctfs that are progressively harder, till you are comfortable. Do #portswigger academy labs all of them, you may skip secc5ions for sqli but you should be confident In technique. Xss depending, but more the better.
You may do BB and portswigger at same time, do one vuln a week then hunt for the vuln for a week. You should Learn it pretty well through repition
Ryan :donor: · @chmod777
79 followers · 134 posts · Server infosec.exchange@Colin_Mac I just signed up for LetsDefend.io and so far I'm digging that. SOC analyst/Blue Team focused. I did a handful of lessons and then subscribed since they had a 50% off
Other resources I've signed up for but haven't fully explored yet:
PortSwigger, Hack the Box, TryHackMe
#portswigger #hackthebox #letsdefend #tryhackme
Digital Empress :verified: · @digitalempress
318 followers · 168 posts · Server infosec.exchangeFinally solved this lab! 🥳
#burpsuite #portswigger #appsec #hacking
https://portswigger.net/web-security/sql-injection/examining-the-database/lab-listing-database-contents-non-oracle
#burpsuite #portswigger #appsec #hacking
Claudio · @sonoclaudio
163 followers · 80 posts · Server mastodon.insicurezzadigitale.comVia, #Malwarebytes: Rubare le #password di #Mastodon (avevo già segnalato un post di #PortSwigger, qualche giorno fa).
Quindi, anche su #Mastodon, attivate #2FA.
#malwarebytes #password #mastodon #portswigger #2fa