OSTechNix · @ostechnix
658 followers · 1706 posts · Server floss.socialA Step-by-Step Guide to Configure Passwordless Sudo Access to Specific Commands in Linux #sudo #password #Linux #NOPASSWD #PASSWD #Sudoers #Linuxcommands #PrivilegeEscalation #LinuxSecurity #Permissions #Linuxadministration
https://ostechnix.com/run-particular-commands-without-sudo-password-linux/
#sudo #password #Linux #nopasswd #passwd #sudoers #linuxcommands #privilegeescalation #linuxsecurity #permissions #Linuxadministration
Mr.Trunk · @mrtrunk
5 followers · 4565 posts · Server dromedary.seedoubleyou.meSecurityOnline: PrivKit: simple beacon object file that detects privilege escalation vulnerabilities https://securityonline.info/privkit-simple-beacon-object-file-that-detects-privilege-escalation-vulnerabilities/ #privilegeescalation #PostExploitation #PrivKit
#privilegeescalation #postexploitation #privkit
Mr.Trunk · @mrtrunk
4 followers · 4466 posts · Server dromedary.seedoubleyou.meSecurityOnline: PrivKit: simple beacon object file that detects privilege escalation vulnerabilities https://securityonline.info/privkit-simple-beacon-object-file-that-detects-privilege-escalation-vulnerabilities/ #privilegeescalation #PostExploitation #PrivKit
#privilegeescalation #postexploitation #privkit
Collei :verified: · @kohelet
81 followers · 402 posts · Server mstdn.socialEASY LINUX PRIVILEGE ESCALATION, WORKS 100% OF THE TIMEEE!!!!111
simply write:
PS1="root@root# "
alias whoami="echo root"
And that's it!!!
works on every Linux system!
This is what real hackers don't want you to know!
Next time: how to protect against this! (hint, just use windowssss?? :O)
Buy my course for more AMAZING TRICKS THEY HIDE FROM YOU!
HACKING HAS NEVER BEEN THIS EASYYYYY!!!!!11112222
#superhackercourse
#Linux (#humor, just in case)
#privilegeescalation
#privilegeescalation #Humor #Linux #superhackercourse
sekurak News · @sekurakbot
30 followers · 232 posts · Server mastodon.com.plPodatność w kernelu Linuksa – dowolny użytkownik może uzyskać uprawnienia roota (privilege escalation). Przypadkiem opublikowali exploita, więc pospieszcie się z łataniem.
W opisie podatności CVE-2023-32233 czytamy: In the Linux kernel through 6.3.1, a use-after-free in Netfilter nf_tables when processing batch requests can be abused to perform arbitrary read and write operations on kernel memory. Unprivileged local users can obtain root privileges. This occurs because anonymous sets are mishandled. Natomiast w tym...
#WBiegu #Kernel #Linux #PrivilegeEscalation
https://sekurak.pl/podatnosc-w-kernelu-linuksa-dowolny-uzytkownik-moze-uzyskac-uprawnienia-roota-privilege-escalation-przypadkiem-opublikowali-exploita-wiec-pospieszcie-sie-z-lataniem/
#wbiegu #kernel #linux #privilegeescalation
GEBIRGE · @GEBIRGE
0 followers · 1 posts · Server infosec.exchangeTaking over a server with a single HTTP request:
https://gebir.ge/blog/privesc-part-3/
I went ahead and created a social media presence, that's how proud I am! ¯\_(ツ)_/¯
#rce #privilegeescalation #deserialization
Vidmo :donor: :mastodon: · @VidmoOreda
654 followers · 2989 posts · Server infosec.exchangeI think the sexiest thing alive is #linux #privilegeescalation and #vulnerability testing.
#linux #privilegeescalation #vulnerability
CyberArkLabs · @CyberArkLabs
31 followers · 17 posts · Server infosec.exchange🚨Breaking News🚨:
Docker Desktop just got hit with more vulnerabilities!
In this two-part series, we dive into the details of how Eviatar Gerzi found SIX privilege escalation vulnerabilities in Docker Desktop for Windows and created a tool, "PipeViewer," to help identify potential risks.
Follow the journey of how he uncovered full privilege escalation (CVE-2022-25365) and more in this must-read article!
🔍 #DockerVulnerability #WindowsContainers #PipeViewer #PrivilegeEscalation #CyberSecurityAwareness
#dockervulnerability #windowscontainers #pipeviewer #privilegeescalation #cybersecurityawareness
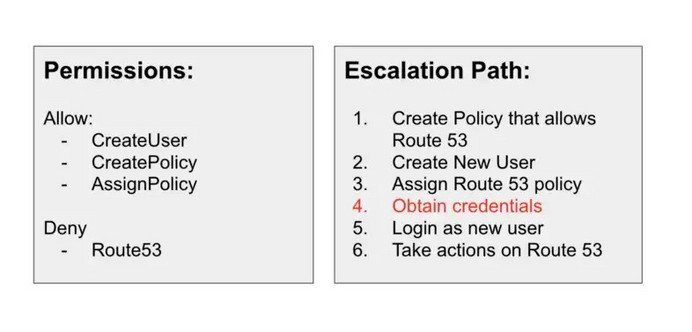
Teri Radichel · @teriradichel
665 followers · 150 posts · Server infosec.exchangeMitigating CreateUser Privilege Escalation and Back Doors: ACM.143 Preventing an attacker from creating a backdoor user in your cloud account ~~~~~ by Teri Radichel | Jan 28, 2023 #cloudsecurity #backdoor #privilegeescalation #iam #createuser #aws
#cloudsecurity #backdoor #privilegeescalation #iam #createuser #aws
Teri Radichel · @teriradichel
664 followers · 150 posts · Server infosec.exchangeMitigating CreateUser Privilege Escalation and Back Doors: ACM.143 Preventing an attacker from creating a backdoor user in your cloud account
~~~~~
by Teri Radichel | Jan 28, 2023
#cloudsecurity #backdoor #privilegeescalation #iam #createuser #aws
#cloudsecurity #backdoor #privilegeescalation #iam #createuser #aws
Taylor Parizo · @taylorparizo
159 followers · 172 posts · Server infosec.exchangeDragonSpark is a busy one. Remote access tool, open-source web shell and priv esc tools, Golang reflection AND source code interpretation using the Yaegi framework.
SparkRAT is something to keep an eye on.
https://www.sentinelone.com/labs/dragonspark-attacks-evade-detection-with-sparkrat-and-golang-source-code-interpretation/
#RAT #PrivilegeEscalation #Golang #ThreatIntel #Malware
#rat #privilegeescalation #golang #threatintel #malware
Teri Radichel · @teriradichel
645 followers · 112 posts · Server infosec.exchangeBackdoors and Privilege Escalation Via Cloud Account Users: ACM.134 Preventing a user from leveraging another user with permissions they don’t have
~~~~~~~
by Teri Radichel | Jan 16, 2023
#iam #cloudsecurity #chbbersecurity #privilegeescalation
#iam #cloudsecurity #chbbersecurity #privilegeescalation
Teri Radichel · @teriradichel
641 followers · 110 posts · Server infosec.exchangePrivilege Escalation Via a Cloud Compute Resource: ACM.133 Limiting Pass Role permissions using AWS IAM policies
~~~~~~~
by Teri Radichel | Jan 15, 2023
#cloudsecurity #cybersecurity #iam #privilegeescalation
https://medium.com/cloud-security/privilege-escalation-via-a-cloud-compute-resource-e869adc89f56
#cloudsecurity #cybersecurity #iam #privilegeescalation
Astra Kernel :verified: · @AstraKernel
641 followers · 679 posts · Server infosec.exchangeDirtyCred Remastered: how to turn an UAF into Privilege Escalation
Articles:
https://exploiter.dev/blog/2022/CVE-2022-2602.html
Poc:
https://github.com/LukeGix/CVE-2022-2602
Credits: @kiks7_7 @LukeGix
#exploitdevelopment #infosec #binaryexploit
#kernelexploit #privilegeescalation #linux
#exploitdevelopment #infosec #binaryexploit #kernelexploit #privilegeescalation #linux
Astra Kernel :verified: · @AstraKernel
635 followers · 674 posts · Server infosec.exchangeLessons on Linux kernel exploit development:
https://breaking-bits.gitbook.io/breaking-bits/exploit-development/linux-kernel-exploit-development
https://lkmidas.github.io/posts/20210123-linux-kernel-pwn-part-1/
#exploitdevelopment #infosec #exploit #exploitation
#kernelexploit #ring0 #privilegeescalation #linux
#exploitdevelopment #infosec #exploit #exploitation #kernelexploit #ring0 #privilegeescalation #linux
Sam Stepanyan :verified: 🐘 · @securestep9
365 followers · 98 posts · Server infosec.exchange#Linux: PoC Code for Linux Kernel Privilege Escalation #Vulnerability (CVE-2022-2602):
#PrivilegeEscalation
#linux #vulnerability #privilegeescalation
Martin Lien :verified: · @lienmar
3 followers · 4 posts · Server infosec.exchangeI was planning to write about how fun it's been to do TCM's Windows Privilege Escalation for Beginners course. But also, i want to say i'm a bit scared of Active Directory now. #privilegeescalation #activedirectory #pentesting
#privilegeescalation #activedirectory #pentesting
Security Affairs RSS feed · @securityaffairs
1 followers · 135 posts · Server 0twitter.comSamba addressed multiple high-severity vulnerabilities https://securityaffairs.co/wordpress/139760/hacking/samba-multiple-flaws.html #informationsecuritynews #ITInformationSecurity #privilegeescalation #PierluigiPaganini #SecurityAffairs #BreakingNews #SecurityNews #hackingnews #Security #Hacking #Samba
#informationsecuritynews #ITInformationSecurity #privilegeescalation #PierluigiPaganini #SecurityAffairs #BreakingNews #SecurityNews #hackingnews #Security #Hacking #Samba
Rob Prometheus · @Prometheus
31 followers · 108 posts · Server infosec.exchangeSo my ex come over and get on my wifi. Guest wifi…#ios #synology #privilegeescalation #privacy
#ios #synology #privilegeescalation #privacy
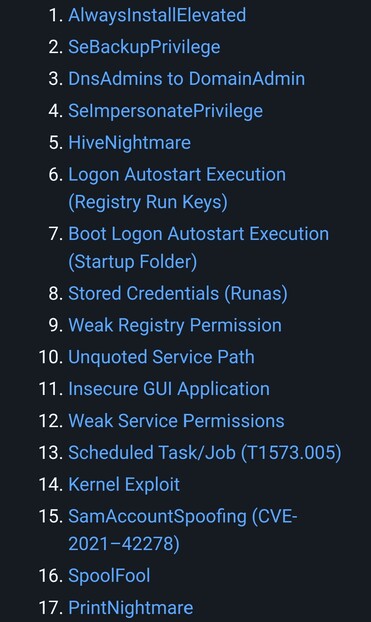
Astra Kernel · @AstraKernel
71 followers · 86 posts · Server infosec.exchangeWindows Privilege Escalation Cheatsheet:
To help #OSCP aspirants understand the various methods of escalating privilege on Windows-based machines and CTFs with examples
https://github.com/Ignitetechnologies/Windows-Privilege-Escalation
#oscp #pentesting #redteam #privilegeescalation #networksecurity