Mr.Trunk · @mrtrunk
10 followers · 17897 posts · Server dromedary.seedoubleyou.meSecurityWeek: How Quantum Computing Will Impact Cybersecurity https://www.securityweek.com/how-quantum-computing-will-impact-cybersecurity/ #Quantumcryptography #QuantumComputing #DataProtection #Quantumsecure #encryption
#quantumcryptography #quantumcomputing #dataprotection #quantumsecure #encryption
Gottfried Szing · @kjoo
607 followers · 191 posts · Server hachyderm.io"Start me up Monday – Training quantum Engineers" zum Thema #quantum #quantumcomputing #quantumtechnology #quantumcryptography #security und mehr an der Fachhochschule Technikum Wien.
https://www.technikum-wien.at/events/start-me-up-monday-get-quantum-ready/
#quantum #quantumcomputing #quantumtechnology #quantumcryptography #security
Mr.Trunk · @mrtrunk
6 followers · 14224 posts · Server dromedary.seedoubleyou.meSecurityWeek: Google Releases Security Key Implementation Resilient to Quantum Attacks https://www.securityweek.com/google-releases-security-key-implementation-resilient-to-quantum-attacks/ #Postquantumcryptography #Quantumcryptography #Identity&Access #cryptography #securitykey #google
#postquantumcryptography #quantumcryptography #identity #cryptography #securitykey #google
Mr.Trunk · @mrtrunk
6 followers · 14123 posts · Server dromedary.seedoubleyou.meSecurityWeek: Google Releases Security Key Implementation Resilient to Quantum Attacks https://www.securityweek.com/google-releases-security-key-implementation-resilient-to-quantum-attacks/ #Postquantumcryptography #Quantumcryptography #Identity&Access #cryptography #securitykey #google
#postquantumcryptography #quantumcryptography #identity #cryptography #securitykey #google
Mr.Trunk · @mrtrunk
6 followers · 14022 posts · Server dromedary.seedoubleyou.meSecurityWeek: Google Releases Security Key Implementation Resilient to Quantum Attacks https://www.securityweek.com/google-releases-security-key-implementation-resilient-to-quantum-attacks/ #Postquantumcryptography #Quantumcryptography #Identity&Access #cryptography #securitykey #google
#postquantumcryptography #quantumcryptography #identity #cryptography #securitykey #google
Hackernoon · @hackernoon_bot
412 followers · 7526 posts · Server social.platypush.techReferenced link: https://hackernoon.com/enhancing-cryptography-with-quantum-circuits-and-key-distribution
Discuss on https://discu.eu/q/https://hackernoon.com/enhancing-cryptography-with-quantum-circuits-and-key-distribution
Originally posted by HackerNoon | Learn Any Technology / @hackernoon: http://nitter.platypush.tech/hackernoon/status/1654169155124199445#m
Learn about quantum computing in cybersecurity by exploring quantum circuits, cryptography protocols, and key distribution. - https://hackernoon.com/enhancing-cryptography-with-quantum-circuits-and-key-distribution #quantumcryptography #quantumcomputing
#quantumcryptography #Quantumcomputing
Gottfried Szing :unverified: · @kjoo
541 followers · 1687 posts · Server fosstodon.orgBrian N. Siegelwax · @bsiegelwax
81 followers · 142 posts · Server qubit-social.xyzUpdated with 73 entrees and, thanks to a suggestion from Jack Krupansky, a wine list with 18 algorithms. More is forthcoming.
https://medium.com/the-modern-scientist/quantum-computing-product-menu-965bf32439d2 #quantum #quantumcomputing #quantumcomputer #quantumtech #quantumtechnology #quantumcommunication #quantummachinelearning #quantumentanglement #quantumtechnologies #quantumcomputers #quantuminternet #quantumcryptography
#quantum #quantumcomputing #quantumcomputer #quantumtech #quantumtechnology #QuantumCommunication #QuantumMachineLearning #quantumentanglement #quantumtechnologies #quantumcomputers #QuantumInternet #quantumcryptography
dispatch · @dispatch
529 followers · 2947 posts · Server ioc.exchangeSide-Channel Attack against CRYSTALS-Kyber https://www.schneier.com/blog/archives/2023/02/side-channel-attack-against-crystals-kyber.html #quantumcryptography #side-channelattacks #quantumcomputing #machinelearning #academicpapers #Uncategorized #cryptography #encryption
#quantumcryptography #side #quantumcomputing #machinelearning #academicpapers #Uncategorized #cryptography #encryption
tkteo · @tkteo
16 followers · 657 posts · Server infosec.exchangeAh! This is indeed in the works! draft from December 2022 of "a post-quantum public-key algorithm extension for the OpenPGP protocol. Given the generally assumed threat of a cryptographically relevant quantum computer, this extension provides a basis for long-term secure OpenPGP signatures and ciphertexts. Specifically, it defines composite public-key encryption based on CRYSTALS-Kyber, composite public-key signatures based on CRYSTALS-Dilithium, both in combination with elliptic curve cryptography, and SPHINCS+ as a standalone public key signature scheme"
#cryptography #pgp #openpgp #gpg #quantum #quantumcomputing #quantumcomputers #quantumcryptography
#cryptography #pgp #openpgp #gpg #quantum #quantumcomputing #quantumcomputers #quantumcryptography
cloudgal42 · @cloudgal42
0 followers · 1 posts · Server infosec.exchangeI recently read a very interesting paper on Leakage-Abuse Attacks against Order-Preserving Encryption (OPE) schemes and Order-Revealing Encryption (ORE) Schemes.
In this paper, the researchers show how the widely used encryption schemes are inadequate. Here are some snippets from the paper.
Order-preserving encryption (#OPE) - ensures that Ek(m1)<Ek(m2) for m1<m2 and Ek the encryption algorithm. Most widely used scheme is #BCLO.
Order-revealing encryption (#ORE) - reveals ordering relations by way of a public comparison function that operates on pairs of plaintexts. Most widely used scheme is #CLWW.
Popular belief is that OPE and ORE schemes remain secure in practice for plaintext data drawn from larger domains, and practitioners could simply avoid using OPE for small-domain data.
The researchers used a non-crossing attack (min-weight non-crossing #bipartite matching) which runs in only a few hours, even for the largest target dataset, against real-world datasets using the BCLO scheme to encrypt a set of first names.
Using this attack they were able to recover almost half the data set. The leakage was even worse for last names, with almost 97% of last names trivially recoverable.
#Composition of the two (BCLO & CLWW) schemes does #decrease attack accuracy but is still far from providing acceptable security.
Exploiting known plaintexts is even easier.
Attacking frequency-hiding schemes - #Kerschbaum recently introduced a scheme that hides frequency information. However, a “#binomial” attack performs reasonably well, recovering on average 30% of first names and 7% of last names. Notably, it recovers majority of high-frequency plaintexts (despite not having frequency information leaked), suggesting these plaintexts are particularly poorly protected by any order-revealing scheme.
In terms of countermeasures, an obvious suggestion is to move towards less leaky schemes, such as those that only reveal order, including Kerschbaum's scheme and the more recent #Boneh et al. scheme based on #multilinear maps. Unfortunately in most settings there exists inherent #challenges to deployment of these schemes. Kerschbaum's scheme is relatively efficient, but requires client-side state which impedes scaling. The Boneh et al. scheme has ciphertexts larger by 10 orders of magnitude than BCLO ciphertexts and requires tens of minutes to compute encryptions.
#ope #bclo #ore #clww #bipartite #composition #decrease #kerschbaum #binomial #boneh #multilinear #challenges #encryption #quantumcomputing #quantumcryptography
Xavier Valcarce · @xvalcarce
13 followers · 1 posts · Server qubit-social.xyzAlright, here we go Mastodon 😄
A small #introduction:
I am a #PhD student at the Institut de Physique Théorique (Université Paris-Saclay/CEA) working on #QuantumInformation. My main focus is #QuantumCryptography (mostly device-independent quantum key distribution) but I am also interested in #QuantumComputing.
I will (mainly) post about our papers, but I might also toot about some of my other interests (#linux stuff, bouldering, political topics, ...). Looking forward to connect with y'all 😊
#introduction #phd #QuantumInformation #quantumcryptography #quantumcomputing #linux
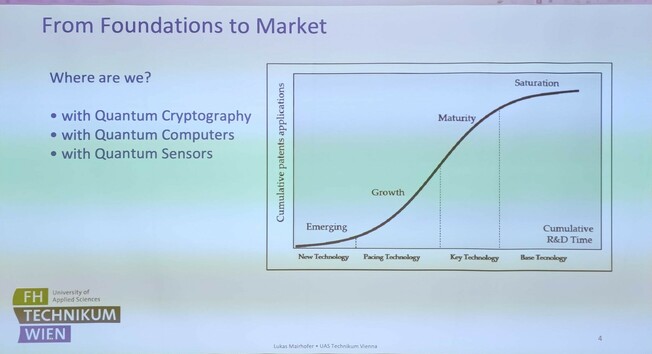
Gottfried Szing :unverified: · @kjoo
317 followers · 745 posts · Server fosstodon.orgWhere would you put the #quantumcomputing #QuantumSensing and #quantumcryptography / #qkd? In what stage is what technology? What is your opinion? 🤔
#quantumcomputing #QuantumSensing #quantumcryptography #qkd
Gottfried Szing :unverified: · @kjoo
279 followers · 695 posts · Server fosstodon.orgProf Leymann explained today the underlying #mathematics of Shor's algorithm without actually going deeper into #quantumcomputing as on the one slides. TIL on what shoulders even a mathematical genius like Peter Shor is standing. All the theories were there, but he combined all this a specific way, which enables QC to break the security (sooner or later or never).
Mind blowing this was. 🤯
#mathematics #quantumcomputing #pqc #quantumcryptography #cryptography
Barry Schwartz :fake_verified: · @chemoelectric
155 followers · 1454 posts · Server mstdn.socialThat such a simulation is impossible is the conclusion of so-called ‘Bell’s theorem’. Therefore ‘Bell’s theorem’ must be fallacious.
That #QuantumComputers (and #QuantumCryptography, which is pure snake oil) are taking advantage of some special ‘quantum’ property is a conclusion that depends on ‘Bell’s theorem’. Thus this conclusion also is fallacious.
#quantumcryptography #quantumcomputers
Barry Schwartz :fake_verified: · @chemoelectric
155 followers · 1454 posts · Server mstdn.socialOkay, it is time for me to irritate the #science hashtaggers who actually are very unscientific. Perhaps they agree with Neil deGrasse Tyson, that ‘objective reality’ (or some such misused phrase) is whatever the orthodox consensus says it is.
I should irritate also the snake-oil salesmen who deal in #QuantumCryptography and those earning their pay on the misuse of funds called #QuantumComputing.
So let’s just have my first foray here ...
#quantumcomputing #quantumcryptography #Science
Brandon Rodenburg, PhD · @punk_physicist
124 followers · 17 posts · Server qoto.orgI lead a group in #quantum technologies at a US national lab. My background is in quantum #optics, but these days I spend my time primarily thinking about things like #QuantumComputing, #QuantumNetworks, #QuantumCommunications, #QuantumSensing, and #QuantumCryptography.
I am also an Ambassador for Optica (formerly the Optical Society or OSA). In my role as Optica Ambassador, I engage in outreach and mentorship to students and early career professionals within the optics and photonics community.
Me as a comic:
#introduction #quantumcomputing #QuantumNetworks #quantum #optics #QuantumCommunications #QuantumSensing #quantumcryptography
IT News · @itnewsbot
1661 followers · 238595 posts · Server schleuss.onlineMastercard’s New Card: Safer From Quantum Attacks? - Quantum computers present a unique threat to many aspects of modern information te... - https://hackaday.com/2022/10/25/mastercards-new-card-safer-from-quantum-attacks/ #post-quantumcryptography #quantumcryptography #quantumcomputer #currentevents #securityhacks #paymentcard #creditcard #debitcard #interest #card
#card #interest #debitcard #creditcard #paymentcard #securityhacks #currentevents #quantumcomputer #quantumcryptography #post
Tech News Worldwide · @TechNews
11247 followers · 97975 posts · Server aspiechattr.meMastercard’s New Card: Safer From Quantum Attacks?
https://hackaday.com/2022/10/25/mastercards-new-card-safer-from-quantum-attacks/
#post-quantumcryptography #quantumcryptography #quantumcomputer #CurrentEvents #SecurityHacks #paymentcard #creditcard #debitcard #Interest #card
#post #quantumcryptography #quantumcomputer #CurrentEvents #SecurityHacks #paymentcard #creditcard #DebitCard #Interest #card
dispatch · @dispatch
472 followers · 2723 posts · Server ioc.exchangeNIST’s Post-Quantum Cryptography Standards https://www.schneier.com/blog/archives/2022/08/nists-post-quantum-cryptography-standards.html #quantumcryptography #quantumcomputing #Uncategorized #cryptanalysis #cryptography #algorithms #NIST
#quantumcryptography #quantumcomputing #Uncategorized #cryptanalysis #cryptography #algorithms #nist