Just Another Blue Teamer · @LeeArchinal
53 followers · 77 posts · Server ioc.exchangeHappy Monday everyone! I know it's a little late and I am not going to deny that the picture with the article really helped this one become my #readoftheday! Brought to you by the Check Point Software Technologies Ltd Research team, this article provides not only insight to the #infostealer but context surrounding creation, functionality, technical analysis, and behaviors. Known as the #Rhadamanthys Stealer, this malware author appears to have given it every functionality needed by any cyber criminal. Enjoy and Happy Hunting!
RHADAMANTHYS: THE “EVERYTHING BAGEL” INFOSTEALER
https://research.checkpoint.com/2023/rhadamanthys-the-everything-bagel-infostealer/
#CyberSecurity #ITSecurity #InfoSec #BlueTeam #ThreatIntel #ThreatHunting #ThreatDetection #HappyHunting
#readoftheday #infostealer #rhadamanthys #cybersecurity #itsecurity #infosec #blueteam #threatintel #threathunting #ThreatDetection #happyhunting
Anonymous :anarchism: 🏴 · @YourAnonRiots
5381 followers · 32103 posts · Server mstdn.socialTOP10 last week's threats by uploads 📊
⬆️ #Redline 517 (478)
⬆️ #Amadey 287 (182)
⬇️ #Remcos 175 (212)
⬇️ #Emotet 150 (302)
⬆️ #Qbot 141 (111)
⬆️ #Asyncrat 133 (102)
⬆️ #Smoke 132 (67)
⬇️ #Snake 119 (143)
⬇️ #Njrat 96 (101)
⬆️ #Rhadamanthys 87 (26)
https://any.run/malware-trends/?utm_source=twitter&utm_medium=post&utm_campaign=statistics&utm_content=200323 #InfoSec #CyberSecurity #Ransomware
#Ransomware #CyberSecurity #InfoSec #rhadamanthys #njrat #snake #smoke #AsyncRAT #qbot #emotet #remcos #amadey #redline
Don Carlos · @engmorales
1 followers · 6 posts · Server techhub.socialRT SwiftOnSecurity: 😎 Google Ad Executives 😎
Looks like money
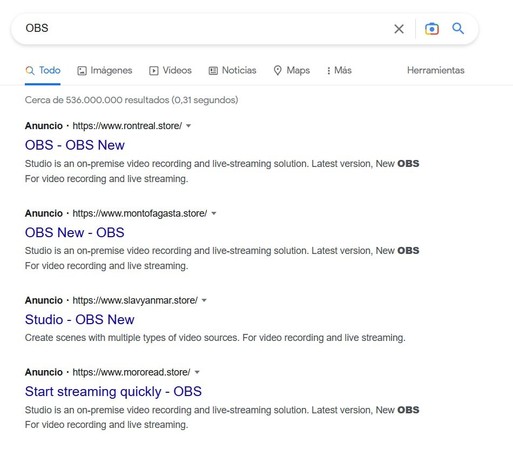
QT 1ZRR4H: 1/ THIS IS BAD!!!
Search for "OBS" in Google and you get, not 1, but 5 (❗️) malicious ads in the first links/results 😱
All part of a new #Rhadamanthys stealer campaign with new tricks and mainly targeting streamers.
FairlySadPanda · @FairlySadPanda
61 followers · 679 posts · Server mastodon.socialMeanwhile it is totally fine on DuckDuckGo, which is a universally superior engine anyway. If you want decent search results, get off Google
RT @1ZRR4H@twitter.com
1/ THIS IS BAD!!!
Search for "OBS" in Google and you get, not 1, but 5 (❗️) malicious ads in the first links/results 😱
All part of a new #Rhadamanthys stealer campaign with new tricks and mainly targeting streamers.
· @Mud
1 followers · 3 posts · Server infosec.exchangeTradingView #SEOPoisoning leading to #Rhadamanthys infection
Delivery:
hxxps://tradingwiv[.]com
hxxp://dropbox[.]com/s/kvtg7pwzb4a0xu0/TradingVlew_x32_x64_bit.zip?dl=1
#C2: 179.43.142.109
#seopoisoning #rhadamanthys #c2
· @Mud
2 followers · 3 posts · Server infosec.exchangeFake/backdoored game cheats leading to #Rhadamanthys infection
Delivery:
hxxps://ominate[.]io
hxxps://github[.]com/t4ppe/HyperVisor-Injector
hxxps://www.tiktok[.]com/@codmodss
hxxps://discord[.]gg/wzmods
#C2: 91.202.5.208
Panel: hxxp://91.202.5.208:443/admin/console/index.html
· @Mud
2 followers · 3 posts · Server infosec.exchangeGPU-Z #SEOPoisoning leading to #Rhadamanthys infection
Delivery: hxxps://download-gpuz[.]net
#C2: 152.89.198.59
Panel: hxxp://152.89.198.59:443/admin/console/index.html
#seopoisoning #rhadamanthys #c2
Katie Paxton-Fear (InsiderPhD) · @insiderphd
1468 followers · 455 posts · Server infosec.exchangeRT @1ZRR4H@twitter.com
1/ THIS IS BAD!!!
Search for "OBS" in Google and you get, not 1, but 5 (❗️) malicious ads in the first links/results 😱
All part of a new #Rhadamanthys stealer campaign with new tricks and mainly targeting streamers.
TropChaud · @IntelScott
192 followers · 36 posts · Server infosec.exchange#Rhadamanthys #stealer seems to be having a moment right now. Quick rundown on what we know about infection trends & its post-exploit TTPs
Discovered last summer, it's one of several popular & emerging #infostealer #malware with new/improved evasion and/or theft capabilities observed in recent months. Like many popular families, Rhadamanthys initial infections occur via multiple vectors, including #phishing & #spam email attachments and - increasingly - legitimate web search ads: https://www.malware-traffic-analysis.net/2023/01/03/index.html, https://blog.cyble.com/2023/01/12/rhadamanthys-new-stealer-spreading-through-google-ads/
In our broad analysis of the infostealer threat landscape, we identified #mitreattack TTPs associated with 16 families across dozens of public reports. We've already added more reported techniques to Rhadamanthys' set since the report dropped this week https://www.tidalcyber.com/blog/big-game-stealing-part-1-the-infostealer-landscape-rising-infostealer-threats-to-businesses-w
Still somewhat limited public reporting on this threat to date, although we've identified 22 (sub-)techniques associated with Rhadamanthys so far. Visualize them and pivot to associated defensive & offensive testing capabilities here: https://app.tidalcyber.com/share/techniqueset/48405ee2-b243-4bda-a6c2-75eb80869056
In addition to the reports above, two other resources here: https://www.accenture.com/us-en/blogs/security/information-stealer-malware-on-dark-web, https://threatmon.io/rhadamanthys-stealer-analysis-threatmon/. Thanks to the teams that published great reporting & analysis around Rhadamanthys so far, including ThreatMon Accenture @malware_traffic & Cyble
#rhadamanthys #stealer #infostealer #malware #phishing #spam #mitreattack #threatinformeddefense #credentials #cookies #mfa #2fa
Brad · @malware_traffic
2104 followers · 87 posts · Server infosec.exchange2023-01-12 (Thursday) - Google Ad --> Fake Notepad++ site textedit-notepad[.]com --> #Rhadamanthys (#RhadamanthysStealer)
I carved the inflated 777 MB EXE to remove all the padding. Sample available at:
- https://bazaar.abuse.ch/sample/2a4637eeb74d47ddbe7ff10f005806bce77ee877b9ae52f55bf6ae425cc3fcd5/
- https://tria.ge/230113-eqwwfahg9v
- https://app.any.run/tasks/3d9a4477-3053-47bf-a194-556b1ad97e23
C2 traffic:
- hxxp://164.90.172[.]224/blob/oo6nbv.a50a
#rhadamanthys #rhadamanthysstealer
Yogesh Londhe :verified: · @YogeshLondhe
48 followers · 35 posts · Server infosec.exchangeTropChaud · @IntelScott
180 followers · 28 posts · Server infosec.exchange#Infostealer Infection Trends: Impersonating Legitimate Software
As actors saw success using #stealer-derived creds in attacks on major orgs last year, @tidalcyber anticipates the infostealer threat for businesses is rising heading into 2023, with search ad abuse a top vector
2023 threat landscape briefing next Tuesday, January 10, noon Eastern with more details: https://hubs.la/Q01v-PN00
(Infographic is already out of date with @malware_traffic 's latest blog on #Rhadamanthys distributed via an ad for a fake Notepad++ download. Update forthcoming! https://www.malware-traffic-analysis.net/2023/01/03/index.html)
#infostealer #stealer #rhadamanthys