kurtseifried (he/him) · @kurtseifried
555 followers · 602 posts · Server mastodon.socialGood news: the Chinese #CA https://www.bjca.cn/ (that is currently in the process of joining the #RootCA program in all our web browsers) has confirmed they have strong technical controls that separate their root CA business from their alleged #spyware business.
Bad news: The alleged spyware business, and tge fact these are bother under control of the same business.
Steve Zakulec · @keen456
24 followers · 206 posts · Server infosec.exchangeThis is genuinely fascinating watching a company basically destroy a large part of itself, not so much for what they originally did, but how they reacted when asked about it: https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/etbBho-VBQAJ?pli=1 #cacert #rootca #certificates #trustcor
#cacert #rootCA #certificates #trustcor
Graham Gold :hacker_g: :hacker_g: · @cirriustech
974 followers · 2286 posts · Server infosec.exchangeMore on dodgy #rootCA
An Untrustworthy #TLS #Certificate in Browsers https://www.schneier.com/blog/archives/2022/11/an-untrustworthy-tls-certificate-in-browsers.html
Graham Gold :hacker_g: :hacker_g: · @cirriustech
974 followers · 2286 posts · Server infosec.exchangeDiego Cordoba 🇦🇷 · @d1cor
514 followers · 2248 posts · Server mstdn.ioRT @helpnetsecurity
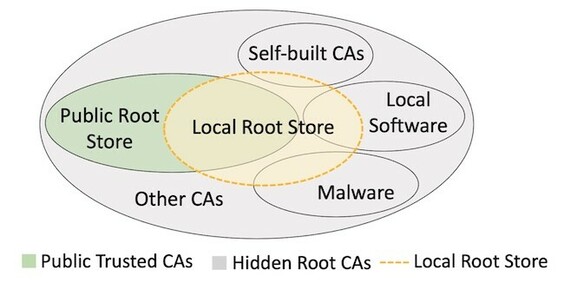
Researchers shed light on hidden root CAs - https://www.helpnetsecurity.com/2021/11/19/hidden-root-cas-ecosystem/ - @QIHU_Official @Tsinghua_Uni @UCIrvine #webpki #HTTPS #rootca #certificates #security
#certificates #https #rootCA #webpki #security
Kevin Vuilleumier 🇨🇭 · @kvuilleumier
341 followers · 5025 posts · Server framapiaf.orghttps://scotthelme.co.uk/impending-doom-root-ca-expiring-legacy-clients/
C'est une problématique intéressante à laquelle on prête peu d'attention.
Lorsqu'on parle de machines connectées qui ne sont plus mises à jour, on pense immédiatement aux risques de sécurité que ça implique (plus de correctifs) et une incompatibilité avec de futures versions des logiciels.
1/n
#letsencrypt #certificate #expiry #rootCA #ca
Grégory PAUL · @paulgreg
130 followers · 1646 posts · Server framapiaf.orgEasy, Secure HTTPS With An ESP8266 via @hackaday https://hackaday.com/2020/07/02/easy-secure-https-with-an-esp8266/ #esp8266 #certificate #TLS #rootCA
#esp8266 #certificate #tls #rootCA