Mark Gritter · @markgritter
202 followers · 312 posts · Server mathstodon.xyzI'm perpetually confused by #aws security groups, which act both as access control rules *and* an identifier for a source of traffic.
For example, you can attach multiple security group to a load balancer, and my understanding is that the result is the union of the permissions.
But when you want to permit traffic from that load balancer to your instance, the load balancer's #SecurityGroup is the "source" for a rule in the instance security group.
But if the load balancer has three groups A, B, and C, are any of them usable as the source? My reading of https://docs.aws.amazon.com/vpc/latest/userguide/security-group-rules.html#security-group-referencing suggests "yes" -- any resource associated with the source security group can use that rule.
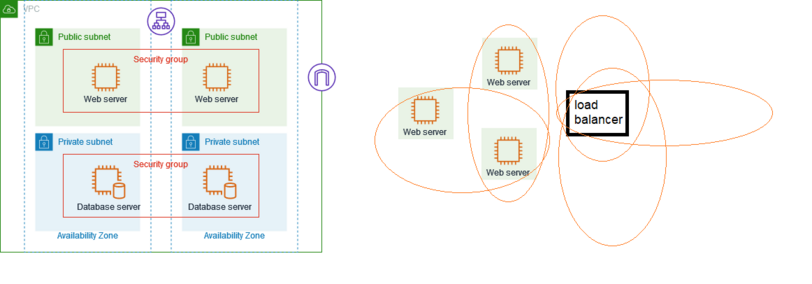
The pictures in the documentation look all nice and neat and hierarchal, when in real life it seems it is always a horrible mess, particularly when you let Kubernetes start creating things for you.
I think the thing that is more surprising to me is that the security group view does not give you any way of finding what is in it! You have to go to the "network interfaces" tab and filter by service group there, then look at the descriptions of each to see what it belongs to.
(So the real members of a security group are network interfaces? I'm pretty sure you can set up different ENIs attached to the same instance in different security groups, but that seems glossed over a lot in the UI.)
Frankly, I think this is an incredible muddle and I'm wondering if other cloud providers do better.
Qiita - 人気の記事 · @qiita
2 followers · 240 posts · Server rss-mstdn.studiofreesia.com【AWS/Terraform】セキュリティグループの管理
https://qiita.com/yokku21/items/d68344a31259f6cdce0a?utm_campaign=popular_items&utm_medium=feed&utm_source=popular_items
#AWS #SecurityGroup #Terraform
#aws #securitygroup #terraform
Patrick Koch · @patkoch
16 followers · 10 posts · Server hostux.socialMy next blog post explains #Azure Virtual #Network using a #Terraform configuration. It is intended for all who would like to establish their first private network in Azure.
#azurecommunity #iac #cloud #microsoft #hashicorp #virtualmachine #subnet #securitygroup
#azure #network #terraform #azurecommunity #iac #Cloud #microsoft #hashicorp #virtualmachine #subnet #securitygroup
Andy 'Bob' Brockhurst · @b3cft
62 followers · 90 posts · Server infosec.exchange@dob That's a big scope.
Some things we do to make our lives easier and doesn't cost $$$.
Enable #guardduty and pipe all the alerts into a slack channel (+email as well).
Enable #cloudtrail log everything to an #S3 bucket in another account. #cloudwatch alerts on auth failures (to slack + email (some go to pagerduty #infosec contact).
We also have some alerts on updates when a cidr is added to a #SecurityGroup.
Don't use #ssh or #bastion/#JumpHosts use #ssm to run automations on the hosts (package install, service restarts etc) also to get a shell on a box (if needed at all). (you can use #TransitiveTags with #RoleAssumption to give granular access).
Using #ssm for console access also logs the entire session (including someone doing sudo su - root etc!) into #S3
Use #MicroSegmentation within our #vpc. Instances behind an #alb will only accept traffic from the #alb #SecurityGroup etc.. #rds, #elasticache willl only accept traffic from instances in the appropriate #SecurityGroup. (Basically we don't use cidr ingress rules, we use security group ids) (this works across accounts in the same region with peering, but not across regions however).
#guardduty #cloudtrail #s3 #cloudwatch #infosec #securitygroup #ssh #bastion #ssm #transitivetags #roleassumption #microsegmentation #vpc #alb #rds #elasticache #aws