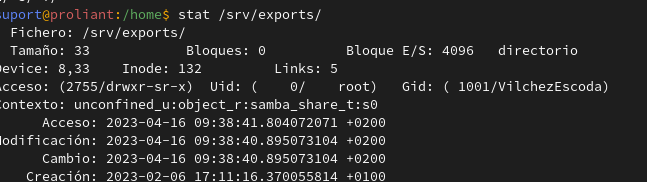
MaInKiVi · @mainkivi
79 followers · 418 posts · Server xarxa.cloudMarco Ivaldi · @raptor
1690 followers · 923 posts · Server infosec.exchangeAs it turns out, the #setuid bit in #Unix was invented by Dennis Ritchie to prevent false updates to the moo game leaderboard 🤯 #Unix #history
https://minnie.tuhs.org/pipermail/tuhs/2023-February/027644.html
Tod Beardsley · @todb
821 followers · 429 posts · Server infosec.exchangeAll right #infosec mastodon. How do I find out who is talking about a particular fresh vuln? I’m going to throw out some hashtags and see what turns up relevant conversation.
#186f495d4be1
#cve_2022_23093
#pingbof
#pr_pack
#freebsd
Is this a big deal because stack based #bof in a common #setuid binary, or a #shrug because #ping is capability restricted in #freebsd?
https://www.freebsd.org/security/advisories/FreeBSD-SA-22:15.ping.asc
#infosec #186f495d4be1 #cve_2022_23093 #pingbof #pr_pack #freebsd #bof #setuid #shrug #ping
c0nsid3rate 🌱 · @c0nsid3rate
256 followers · 503 posts · Server infosec.exchangeRooted another OSCP machine this morning. There is no other exploit that has been more widespread and easy to leverage than pwnkit (CVE-2021-4034). I've simply lost count of the the number of machines I've been able to use this on to get root access from a low-privilege account. For people who do this kind of stuff, this post is a cold take, but I just wanted to come here and state the obvious. #OSCP #pwnkit #polkit #CVE-2021-4034 #Linux #pkexec #setuid
From the Ubuntu website: "A local privilege escalation vulnerability was found on polkit’s pkexec utility. The pkexec application is a setuid tool designed to allow unprivileged users to run commands as privileged users according predefined policies. The current version of pkexec doesn’t handle the calling parameters count correctly and ends trying to execute environment variables as commands. An attacker can leverage this by crafting environment variables in such a way it’ll induce pkexec to execute arbitrary code. When successfully executed the attack can cause a local privilege escalation given unprivileged users administrative rights on the target machine."
#oscp #pwnkit #polkit #cve #linux #pkexec #setuid