technomike :verified: 🏳️🌈 · @technomike
34 followers · 122 posts · Server mstdn.social🚨 Watch out for the Vietnamese threat actor known as MrTonyScam. They're launching wide-reaching Facebook Messenger spam attacks with dangerous attachments. Stay vigilant! #Cybersecurity #ThreatActor #Malware #FacebookMessenger
#facebookmessenger #Malware #threatactor #CyberSecurity
MISP · @misp
998 followers · 108 posts · Server misp-community.orgAnother excellent playbook from @cudeso "Threat actor profiling" to explore MISP galaxies and clusters and discover TA associated TTPS, indicators and vulnerabilities and even TAXII-ing towards MITRE ATT&CK repository.
For more playbooks https://github.com/MISP/misp-playbooks/
#cti #misp #opensource #ThreatIntelligence #threatintel #threatactor
#cti #misp #opensource #threatintelligence #threatintel #threatactor
Manuel Bissey · @mbissey
30 followers · 459 posts · Server cyberplace.socialCybersecurity researchers have discovered previously undocumented payloads associated with a Romanian #threatactor named Diicot, revealing its potential for launching distributed denial-of-service #DDoS attacks☝️👩💻
IAintShootinMis · @iaintshootinmis
495 followers · 375 posts · Server digitaldarkage.cc#NewsYouShouldKnow is full of all kinds of great things this week.
#SVB #Outlook #CVE #Telerik #CISA #CTI #ThreatIntel #ThreatActor #Emotet
https://www.justinmcafee.com/2023/03/20230321news-you-should-know.html
#newsyoushouldknow #svb #outlook #cve #telerik #cisa #cti #threatintel #threatactor #emotet
Ultraviolet · @VioletSullivan
31 followers · 49 posts · Server risk.socialBold #threatactor method used by #medusa -showing video for proof of access and captured first by Brett Callon (@brettcallon) https://twitter.com/brettcallow/status/1633143876600082432?s=46&t=04BtnGCemt5Ct-65f8iJ9g
acrypthash👨🏻💻 · @acrypthash
305 followers · 325 posts · Server infosec.exchangeIf you have a root account on vCenter that has an expired password, would that be considered a vulnerability? Would a threat actor be able to leverage that to gain access?
#security #vmware #password #vulnerability #threatactor
Joe Słowik · @jfslowik
2797 followers · 1695 posts · Server infosec.exchangeWhen your team catches a #ransomware incident in progress and shoots it in the face, but before you can gather enough details to link the activity to a known #ThreatActor... #CTI #ThreatIntelligence
#ransomware #threatactor #cti #threatintelligence
We Open Tech · @weopentech
73 followers · 220 posts · Server infosec.exchangeThe alleged #hacker behind the Riot Games #breach is now trying to auction off the source code for the game League of Legends and is taking bids starting at $1 million. #InfoSec #GameHacking #ThreatActor
#hacker #breach #infosec #gamehacking #threatactor
Joe Słowik · @jfslowik
2622 followers · 1083 posts · Server infosec.exchangeExcited to head to Lausanne in March to present on #CTI #threatactor tracking and the problems therein for #insomnihack
https://www.insomnihack.ch/talks-2023/#GRVQEJ
#cti #threatactor #insomnihack
тняєαт нυηтяєѕѕ 🚨 :verified: :donor: · @ThreatHuntress
189 followers · 213 posts · Server infosec.exchange#Women are naturally good at #DFIR because if we can figure out where you were and who you were with on Sunday, September 23, 2019 at 2:56:43am, we can definitely figure out what a #threatactor is doing
#women #dfir #threatactor #infosec #threathunting #jokes
Xavier «X» Santolaria :verified_paw:🇧🇪🇪🇸 @ 🇨🇭 · @0x58
495 followers · 526 posts · Server infosec.exchange#WhatsApp has denied claims of a #databreach of 500 million users worldwide days after a news platform reported that the stolen information was being sold on the dark web.
Remember that according to a report published by Cyber News on November 26, an unknown #threatactor was able to hack into the messaging application and sell the stolen information on the dark web.
I guess we'll have to wait some more to see where the truth lies.
https://thecyberexpress.com/whatsapp-denies-data-leak-500-million-users/
#whatsapp #databreach #threatactor #cybersecurity #infosec
Misuse Case · @MisuseCase
13 followers · 70 posts · Server twit.socialA related #infosecurity practice is plotting an “abuse case.” This is a #usecase but from the perspective of a #threatactor. The user in an abuse case is the protagonist of the #untitledgoosegame (“I think I am going to cause problems on purpose”).
Then of course there is the “misuse case”: what happens when a legitimate user makes a mistake with the application or system? 3/?
#infosecurity #usecase #threatactor #untitledgoosegame
Sten Eikrem · @Storesteinen
43 followers · 67 posts · Server infosec.exchange@fifonetworks I agree that the explanations in most certifications are bad. I'm currently working on #cRISK and the language there is at the best of times unnecessary heavy and complicated.
I find it sad but understandable that respected online dictionaries can't tell the differences as well. Most folks can't. Its just a fact.
However would you agree that a common language and understanding of #risk terms is crucial to have a meaningful common discussion on what to do and what to prioritise in #cyber?
Unfortunately this is not my experience, even in the same organisations and teams.
This makes meaningful discussions in a topic already complex almost impossible.
From what I've come to understand over the years is that #threat (and related #threatactor (s)) is just one building block or component of #risk. The other ones is the #asset #control #vulnerability and #Lossevent / #impact.
If you cannot describe these building blocks together, then you don't have a #risk. You have something else, an #threat #lossevent #issue, #controldeviation #problem #a-thing #something. #a-list-of-things-todo
But please do not call it a #riskregister.
When looking at the average #riskregister this is what most of them contains just that - #things.
#crisk #risk #cyber #threat #threatactor #asset #control #vulnerability #lossevent #impact #issue #controldeviation #problem #a #something #riskregister #things
woFF · @woFF
39 followers · 42 posts · Server infosec.exchangePretty funky investigation and response to a #pypi #supplychain #threatactor developing a #malware : https://blog.phylum.io/disrupting-a-software-supply-chain-threat-actor-building-a-botnet
Might use the TTPs for the next threat detection test...
#pypi #supplychain #threatactor #malware
Joe Slowik · @jfslowik
1330 followers · 74 posts · Server infosec.exchangeNew blog from me covering #CTI-focused #ThreatHunting and #pivot methodologies applied to #domain hunting - with the unexpected result of potentially identifying a campaign linked to #DPRK #threatactor #Kimsuky. Shout out to @DomainTools, URLScan.io, and Censys.io for enabling this research!
#cti #threathunting #pivot #domain #dprk #threatactor #kimsuky
Sten Eikrem · @Storesteinen
43 followers · 67 posts · Server infosec.exchange@jerry Thats unfortunate, but understandable.
It seems like its not easy for folks if your not having an background from #enterprise #military or #government to know that in every country there are forces working for #good and depending on your #threatactor #threatlandscape #threatmodeling for #bad.
I've always put #CISA squarly in the good category due to the great work they do and they are a great resource for #infosec community and anyone else working to improve cybersecurity in private life, companies and countries.
If you and your commuity truly is a target or interest of #nationstate #lawenforcement or #intelligence community attention, I'm not sure #mastodon is the right type of platform for you.
#lawenforcement and #intelligence #agencies from #nationstate seems to always find a way when they focus their efforts and the massive resources anyways and from my perspective, I'm struggeling to see how blocking #infosecExchange would make any significant #riskreduction in such regard.
#enterprise #military #government #good #threatactor #threatlandscape #threatmodeling #bad #cisa #infosec #nationstate #lawenforcement #intelligence #mastodon #agencies #infosecexchange #RiskReduction
mrjhnsn :verified: :donor: · @mrjhnsn
165 followers · 133 posts · Server infosec.exchangeSooo #threatactor appears to have compromised the domain of someone who is not a client of mine… however, in the course of this compromise they intercepted comms between a user at this domain and a client of mine.
This external domain user was preparing to wire $400k to my client user.
The quick thinking #threatactor quickly registered a misspelling of my client’s domain name, signed up for ZohoMail, and emailed the external domain user in an attempt to intercept the wire.
The ext-user noticed something was amiss and emailed my client, and while we were trying to determine what was happening, ext-user could not make phone calls from his cell… and had provided his cell to the #threatactor.
The external domain’s business does not have an IT helper, staff or MSP.
Right now there are some #threatactors god knows how deep in this domain and its proving very tough to get the domain owners to realize this.
SMB’s need our help.
FilesWithThreateningAuras · @Iaintshootinmis
202 followers · 504 posts · Server infosec.exchange@ozurie This argument cycles back around every few weeks, but unlike birdsite, here actually seems to be conducive to conversations :D
With that being said, Bad guys are going to bad guy. They were doing it before Cult of the Dead Cow released Back Orifice, and will continue long after we're all dead and gone.
As a blue teamer, I don't have the tools or time to learn everything about red teaming to be an effective adversary for myself and the things I build. I also don't work for an org with a large enough budget to bring in full time red team staff to pound on my security controls all day.
But, Metasploit is a super easy way for me to implement a control and them hammer against it with little to no additional knowledge.
It goes back to the guns argument. Are guns bad? No, at best they are amoral. But are they dangerous? Absolutely.
I'd prefer to have them than to not have them any day of the week. Same with #metasploit #cobaltStrike etm,
Happy to hear any rebuttal and to work out what a better option is for this kind of security assurance testing.
#infosec #security #redteam #threatactor #securityassurance #securitytools
#metasploit #cobaltstrike #infosec #security #redteam #threatactor #securityassurance #securitytools
Dmitry Bestuzhev · @dimitribest
28 followers · 11 posts · Server infosec.exchange#Threat Group Cards: A #ThreatActor Encyclopedia
https://apt.etda.or.th/cgi-bin/aptgroups.cgi
#MISP connector available
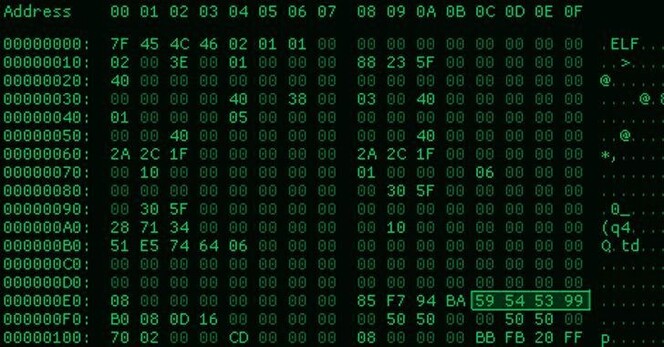
Cody Dostal :unverified: · @dostalcody
337 followers · 358 posts · Server infosec.exchangeA #ThreatActor has claimed to have breached the U.S. Congress.
https://nitter.it/vxunderground/status/1590865694027288577#m
EDIT: Some comments are saying it looks like NJ General Assembly, not US Congress.
https://nitter.it/uuallan/status/1590869923580022784#m
Since this is just claims and basic evidence, it’s definitely a questionable claim, but something to keep an eye on.
#threatactor #cybersecurity #infosec #breach