Aaron Gable · @asg
211 followers · 407 posts · Server hachyderm.ioApropos of nothing, here's a fun question at the intersection of #linguistics and the #webpki. Given the following sentence:
"...has determined that using the FQDN in the Certificate is no longer legally permitted."
which of the following two things do you think is no longer legally permitted?
LisPi · @lispi314
282 followers · 4213 posts · Server mastodon.topMichael Paepcke · @paepcke
5 followers · 15 posts · Server infosec.exchangeOverview #usenix #enigma2023:
usenix.org/conference/enigma2023
Must-Follow Accounts:
#usenix #enigma2023 #goog #twtr #pki #webpki #iam #ml #eff
Aaron Gable · @asg
174 followers · 288 posts · Server hachyderm.ioDo you like security? Do you like privacy? Cryptography? Do you like working for a public benefit non-profit instead of an investor-beholden corporation?
Let's Encrypt is hiring for someone to join our SRE team and help run the largest Certificate Authority in the world! Come work with me and some of the most wonderful folks in tech, to make the web a better place.
#jobs #sre #webpki #security #privacy #cryptography
GrapheneOS · @GrapheneOS
2899 followers · 128 posts · Server grapheneos.socialNormally, WebPKI certificates lack a secure issuance process and an attacker able to MITM unauthenticated HTTP(S) can obtain one.
GrapheneOS uses the CAA accounturi feature to securely pin our Let's Encrypt account keys for each of our servers for secure certificate issuance.
#grapheneos #privacy #security #webpki #letsencrypt #accounturi
#grapheneos #privacy #security #webpki #letsencrypt #accounturi
Dataplane.org · @dataplane
24 followers · 6 posts · Server fosstodon.orgThe Internet Last Week
* AS PAth (ASPA) verification objects in the RPKI
https://mailarchive.ietf.org/arch/msg/sidrops/xXd8d42FSYT_RPW1h6gif6Ew0_g/
* Internet Governance Forum
https://igf2022.intgovforum.org/en
https://www.intgovforum.org/en/content/igf-2022-outputs
* Trustcor root certs removal
https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/yLohoVqtCgAJ
https://www.washingtonpost.com/technology/2022/11/30/trustcor-internet-authority-mozilla/
* SEAMEWE-5 undersea cable cut
https://www.theregister.com/2022/11/30/seamewe5_cut_outage_apac_africa/
https://twitter.com/PTAofficialpk/status/1597632957627658240?ref_src=twsrc%5Etfw
https://twitter.com/netblocks/status/1597625107333238784?ref_src=twsrc%5Etfw
#bgp #rpki #IGF2022 #x509 #webpki #outages
rmhrisk :verified: · @rmhrisk
424 followers · 47 posts · Server infosec.exchangeTo err is human, to forgive is divine
https://unmitigatedrisk.com/?p=711 #WebPKI #ACME #FailOver
· @dustinhollenback
2 followers · 1 posts · Server infosec.exchangeFrom the Washington Post:
Web browsers drop mysterious company with ties to U.S. military contractor
https://www.washingtonpost.com/technology/2022/11/30/trustcor-internet-authority-mozilla/
rmhrisk :verified: · @rmhrisk
421 followers · 46 posts · Server infosec.exchangeA Boy Scout is always prepared https://unmitigatedrisk.com/?p=710 #WebPKI #ACME #ARI
Aaron Gable · @asg
64 followers · 44 posts · Server hachyderm.ioAnd Eric Rescorla (CTO of Firefox) just published this fantastic writeup about #eIDAS, the EU's attempt to legislate that browsers *must* trust certain root certificates that issue #QWAC certs, a specific kind of EV cert. It also starts with a great overview of the whole #WebPKI system, in order to set up the argument that eIDAS is Bad for the Internet.
https://educatedguesswork.org/posts/eidas-article45/
It goes on to propose alternate designs that achieve the EU's goals without compromising trust. Well worth a read!
Aaron Gable · @asg
63 followers · 43 posts · Server hachyderm.ioRyan Hurst (of Google Trust Services, Google's CA, but obvs not speaking on their behalf) just published a good roundup of some of the major things that need to change in the #WebPKI / #TLS ecosystem to evolve in the modern era. Just 5% of CAs issue 99% of TLS certs!
https://unmitigatedrisk.com/?p=702
Points include:
- Require #ACME for all certificate issuance
- Get ACME clients to fail over between CAs
- Use Acme Renewal Info to make mass revocations non-issues
- Do continuous audits
Give it a read!
Dr. Joseph Lorenzo Hall · @joebeone
819 followers · 104 posts · Server techpolicy.socialFrom @ekr____@twitter.com: "Can we agree on the facts about QWACs? More than you wanted to know about the eIDAS proposal to regulate how browsers treat certificates" https://educatedguesswork.org/posts/eidas-article45/ #eIDAS #QWACs #WebPKI #TLS
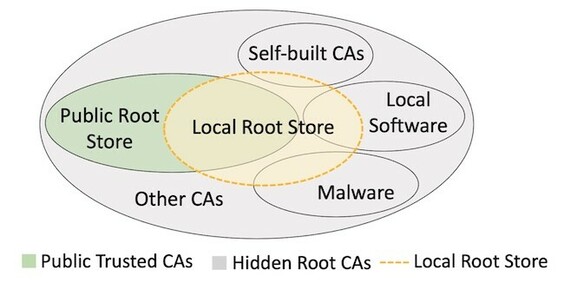
Diego Cordoba 🇦🇷 · @d1cor
514 followers · 2248 posts · Server mstdn.ioRT @helpnetsecurity
Researchers shed light on hidden root CAs - https://www.helpnetsecurity.com/2021/11/19/hidden-root-cas-ecosystem/ - @QIHU_Official @Tsinghua_Uni @UCIrvine #webpki #HTTPS #rootca #certificates #security
#certificates #https #rootCA #webpki #security