Stefano Marinelli · @stefano
813 followers · 1837 posts · Server mastodon.bsd.cafeA few days ago, someone asked me for advice about a slow website.
Upon analysis, the server wasn't the issue—it was running #Linux #CentOS7 on bare metal. However, the site was operating on PHP 5.4 (default for CentOS 7) and was entirely custom-made.
I suggested updating everything, especially since CentOS 7 is nearing its EOL, and transitioning the web application to work on PHP 8.
Their response? "We don't want to do it." They wanted me to set up a new, optimized server to run PHP 5.4. I explained the risks and the nonsensical nature of this, only to hear that they found someone willing to install PHP 5.4 on a new system. So, if I refused, they'd give the job to someone else.
I replied, "Good luck," and ended the conversation.
It saddens me that some in the IT world would opt for such shortcuts rather than striving for a more secure web.
#linux #centos7 #websecurity #techethics #servermanagement #sysadmin #php
Lulu Powerful · @lulu_powerful
173 followers · 722 posts · Server fosstodon.orgHellloooo, Web Security Mastodon. :)
I have a question if you don't mind indulging me. I've used a VPN for a while, but all of a sudden, a bunch of popular retail sites have stopped working for me - unless I turn off my VPN.
Same thing is happening to my family member, who uses a different VPN.
I use a Chromium-based browser (I know, I know, I have excuses lol), and he uses a Firefox variant.
So... has it begun? Is this the start of the "web integrity" apocalypse?
Daniel Norton · @daniel
97 followers · 587 posts · Server mastodon.danielnorton.comCongrats to the University of Pennsylvania for the greatest number of hacked Google hits via website open redirect.
e.g. https://www.google.com/search?q=site%3Awww.workday.upenn.edu+%22untitled%22
You can put any URL after "http://www.workday.upenn.edu/" and it will redirect there.
See https://cwe.mitre.org/data/definitions/601.html
#cybersecurity #security #privacy #CWE #CWE601 #OpenRedirect #WebSecurity #CrossSiteRedirect #CrossDomainRedirect #UniversityOfPennsylvania
#cybersecurity #security #privacy #cwe #cwe601 #openredirect #websecurity #crosssiteredirect #crossdomainredirect #universityofpennsylvania
AzureTracks · @azuretracks
0 followers · 33 posts · Server techhub.socialTip: Safeguard your web browsing experience with Microsoft Defender SmartScreen. It blocks known malicious websites and helps protect you from phishing attacks. #WebSecurity #MicrosoftDefender
#websecurity #microsoftdefender
Mr.Trunk · @mrtrunk
5 followers · 9089 posts · Server dromedary.seedoubleyou.meSecurityWeek: US, Australia Issue Warning Over Access Control Vulnerabilities in Web Applications https://www.securityweek.com/us-australia-issue-warning-over-access-control-vulnerabilities-in-web-applications/ #Vulnerabilities #websecurity #Government #guidance
#vulnerabilities #websecurity #government #guidance
Mr.Trunk · @mrtrunk
5 followers · 8887 posts · Server dromedary.seedoubleyou.meSecurityWeek: US, Australia Issue Warning Over Access Control Vulnerabilities in Web Applications https://www.securityweek.com/us-australia-issue-warning-over-access-control-vulnerabilities-in-web-applications/ #Vulnerabilities #websecurity #Government #guidance
#vulnerabilities #websecurity #government #guidance
Mr.Trunk · @mrtrunk
5 followers · 8786 posts · Server dromedary.seedoubleyou.meSecurityWeek: US, Australia Issue Warning Over Access Control Vulnerabilities in Web Applications https://www.securityweek.com/us-australia-issue-warning-over-access-control-vulnerabilities-in-web-applications/ #Vulnerabilities #websecurity #Government #guidance
#vulnerabilities #websecurity #government #guidance
Mr.Trunk · @mrtrunk
5 followers · 8685 posts · Server dromedary.seedoubleyou.meSecurityWeek: US, Australia Issue Warning Over Access Control Vulnerabilities in Web Applications https://www.securityweek.com/us-australia-issue-warning-over-access-control-vulnerabilities-in-web-applications/ #Vulnerabilities #websecurity #Government #guidance
#vulnerabilities #websecurity #government #guidance
Mr.Trunk · @mrtrunk
5 followers · 8584 posts · Server dromedary.seedoubleyou.meSecurityWeek: US, Australia Issue Warning Over Access Control Vulnerabilities in Web Applications https://www.securityweek.com/us-australia-issue-warning-over-access-control-vulnerabilities-in-web-applications/ #Vulnerabilities #websecurity #Government #guidance
#vulnerabilities #websecurity #government #guidance
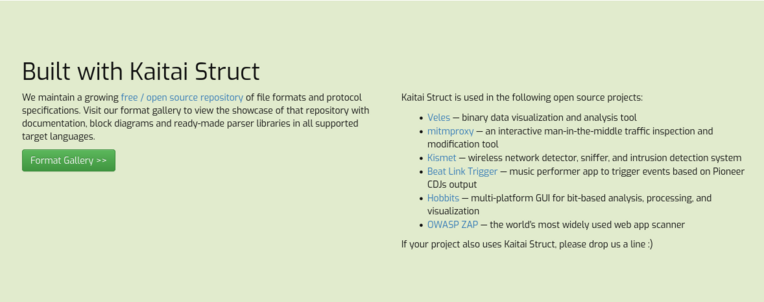
Skyper 💻🎧☕📖 · @Skyper
28 followers · 222 posts · Server fosstodon.org@zaproxy is now mentioned in the "Built with Kaitai Struct" section of the official website of the project!
Kaitai Struct has been used to generate the parser of ".DS_Store" files baked into ZAP to detect potential hidden files when crawling websites with its Spider tool.
#security #infosec #hacking #web #websecurity
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
136 followers · 393 posts · Server defcon.socialHTTPLeaks - All possible ways, a website can leak HTTP requests
#pentesting #websecurity #infosec
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
124 followers · 384 posts · Server defcon.socialTop 10 OSINT Tools
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
#cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips #linux #websecurity #network #networksecurity #cybersecurityawareness
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
124 followers · 382 posts · Server defcon.socialJenkins CI/CD pipeline:
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity
#cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips #linux #websecurity #network #networksecurity
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
117 followers · 372 posts · Server defcon.socialIncident Response Process
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
#cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips #linux #websecurity #network #networksecurity #cybersecurityawareness
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
115 followers · 362 posts · Server defcon.social10 Effective Ways of Preventing Insider Threats
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
#cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips #linux #websecurity #network #networksecurity #cybersecurityawareness
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
115 followers · 361 posts · Server defcon.social10 Ways to Protect Your Personal Data
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
#cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips #linux #websecurity #network #networksecurity #cybersecurityawareness
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
115 followers · 361 posts · Server defcon.socialCommon DNS Attacks
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
#linux #websecurity #network #networksecurity #cybersecurityawareness #cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips
FastRuby.io · @FastRuby
27 followers · 97 posts · Server ruby.socialThere is no greater threat to your Rails app than exploitable code.
ICYMI: Our Rails security webinar is out and free to watch! Check out our new blog to watch it, as well as Ernesto’s slides. Make sure to bookmark our resources linked throughout—you’ll need them!
#rubysec #security #infosec #cybersecurity #websecurity
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
113 followers · 353 posts · Server defcon.socialCommon Data Privacy Mistakes
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
#cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips #linux #websecurity #network #networksecurity #cybersecurityawareness
Vasileiadis A. (Cyberkid) 🛡 · @Cyberkid1987
113 followers · 349 posts · Server defcon.socialAre You Protected From Hackers on Public WiFi?
#cybersecurity #pentesting #informationsecurity #hacking #DataSecurity #CyberSec #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness
#cybersecurity #pentesting #informationsecurity #hacking #datasecurity #cybersec #bugbountytips #linux #websecurity #network #networksecurity #cybersecurityawareness