Joerg Jaspert :debian: · @Ganneff
266 followers · 869 posts · Server fulda.socialUsing #OPNSense, is there really no "self-service" web interface? Where a user can login and do nothing beside changing their password, setting up OTP, download a #VPN config and (if needed) renew their users #X509 #cert (for that VPN)?
Right now it seems, if using OTP, an admin has to create the initial secret. Tell that to the user somehow. Also tell them initial password. Then user can login - and change password / request new OTP seed. But *nothing* else.
There appears to be no way to get the user a VPN config safely, have them update their cert once a year (default lifetime 397 days). Except for an admin doing the work of exporting the VPN config/cert and storing those exports in some other system, to which the user then needs access to download their config (or updated cert).
Really?
I hope I only miss stuff, this would be a *huge* point against OPNsense, unfortunately. I can't have an admin go and recreate things all the time.
Soo, what did I miss?
Kevin Karhan :verified: · @kkarhan
1010 followers · 60906 posts · Server mstdn.social@dangoodin I doubt this to be the case - #Fax survive in regulatory bs nieches, and #Passwords will be unremoveable since not every platform & application will allow auth via #X509 certs, #GnuPG# or #SSH #Pubkeys and you can't force everything to be #online or using a centralized server...
#online #pubkeys #ssh #gnupg #x509 #passwords #fax
icinga (inofficial) · @icinga
20 followers · 149 posts · Server social.tchncs.derobalex · @robalex
4 followers · 48 posts · Server indieweb.social:mastodon: aytin :fedora: · @aytin
25 followers · 203 posts · Server mastodon.unoHo cercato di sintetizzare e semplificare al massimo l'insieme di operazioni che faccio quando ho bisogno di creare una catena di certificati per i miei laboratori o per uso personale, allo scopo di far diventare l'operazione meno complicata di quanto sarebbe realmente.
https://noblogo.org/aytin/come-creare-un-certificato-digitale
#DigitalCertificate #x509 #csr #openssl #ca #cryptography #AsymmetricEncryption #SymmetricEncryption #DigitalSignature
#digitalcertificate #x509 #csr #openssl #ca #cryptography #asymmetricencryption #symmetricencryption #digitalsignature
Joel Goguen · @jgoguen
244 followers · 1 posts · Server hachyderm.ioHello (again) World!
I suppose it's probably about time for another #introduction since I’ve moved servers. Hi! I'm me. You know I'm me because I said so, and this is the Internet so why would I lie?
I'm a #security #generalist, currently focusing on securing client devices (your employee laptops/desktops/phones) and #ZeroTrust. I like to think I'm reasonably competent with #X509 certificates and #2fa.
#introduction #security #generalist #zerotrust #x509 #2fa
Stewart Russell · @scruss
189 followers · 819 posts · Server xoxo.zoneI love that the ham radio community decided that the best way to validate radio contact logs was to massively over-engineer an X.509 public key cryptography solution
Logbook of the World — https://lotw.arrl.org/lotw-help/
:mastodon: aytin :fedora: · @aytin
18 followers · 181 posts · Server mastodon.unohttps://noblogo.org/aytin/stunnel-cose-e-come-si-configura
#ca #certificati #CifraturaAsimmetrica #CifraturaSimmetrica #crittografia #fullchain #psk #ssh #ssl #stunnel #tls #x509 #openssl
#ca #certificati #cifraturaasimmetrica #cifraturasimmetrica #crittografia #fullchain #psk #ssh #ssl #stunnel #tls #x509 #openssl
:mastodon: aytin :fedora: · @aytin
18 followers · 181 posts · Server mastodon.unohttps://noblogo.org/aytin/stunnel-cose-e-come-si-configura
#ca #certificati #CifraturaAsimmetrica #CifraturaSimmetrica #crittografia #fullchain #psk #ssh #ssl #stunnel #tls #x509 #openssl
#ca #certificati #cifraturaasimmetrica #cifraturasimmetrica #crittografia #fullchain #psk #ssh #ssl #stunnel #tls #x509 #openssl
:mastodon: aytin :fedora: · @aytin
18 followers · 181 posts · Server mastodon.unohttps://noblogo.org/aytin/stunnel-cose-e-come-si-configura
#ca #certificati #CifraturaAsimmetrica #CifraturaSimmetrica #crittografia #fullchain #psk #ssh #ssl #stunnel #tls #x509 #openssl
#ca #certificati #cifraturaasimmetrica #cifraturasimmetrica #crittografia #fullchain #psk #ssh #ssl #stunnel #tls #x509 #openssl
bertrand 🏃 👨💻 · @bertrand
167 followers · 911 posts · Server piaille.fr@iamkale certificates are #x509, not #tls or #ssl. #https on the other hand can be either ssl or TLS and both make use of those x509 certificates.
And yep, I too say SSL connection when I should say TLS connection ^^
Oh and x509 certificates can be generated using #openssl 🙃
#x509 #tls #ssl #https #openssl
bertrand 🏃 👨💻 · @bertrand
156 followers · 864 posts · Server piaille.frOK so a self-issued cert is used to authenticate the user.
However it's referenced in the enterprise LDAP after some enrolment took place I guess? Like a FIDO2 pub key is stored server-side after enrolment. And the user attributes are not coming from the self-issued cert but from that enrolment phase.
I can see that happening eventually (though #X509 UX vs #FIDO2, there's not really much of a match here...)
bertrand 🏃 👨💻 · @bertrand
156 followers · 864 posts · Server piaille.fr@kidehen @meneer @aniltj @w3c
Very few enterprises if any want to deal with any self-issued credentials when we're dealing with *B2E* access control. They already have a hard time maintaining identity quality and proofing without having to trust user issued data, especially for non public access (it's not because I self-issue the CEO title that I can have access to those documents)
#x509 #tls
bertrand 🏃 👨💻 · @bertrand
156 followers · 864 posts · Server piaille.fr@kidehen @meneer @aniltj @w3c
How will a selfsigned CA scale better than PGP?
If as a person, app or organisation I want strong assurance about a returning identity (ie proof of possession) I already can do that with FIDO2 (or X509 but the former is the current cool kid on the block)
Neither #FIDO2 nor selfsigned #X509 solves identity proofing. They're as good as FB so that says a lot 😊
#identity #authenticity #zerotrust #pgp #ssi
#fido2 #x509 #identity #authenticity #zerotrust #pgp #ssi
bertrand 🏃 👨💻 · @bertrand
156 followers · 864 posts · Server piaille.fr@kidehen @meneer @aniltj @w3c
Mmh 🤔, who apart from my employer can provide a VC stating my employment status? Who can certify my diploma? Who can provide a VC stating my health insurance status? Who can provide a VC certifying my legal identity? I definitely need 3rd parties to issue those VCs right.
#identity #authenticity #x509 #tls #ssi #privacy #internet #web #verifiableCredentials
#identity #authenticity #x509 #tls #ssi #privacy #internet #web #verifiablecredentials
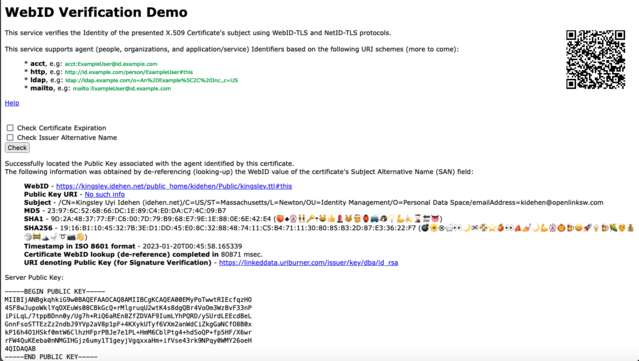
Kingsley Uyi Idehen · @kidehen
469 followers · 1118 posts · Server mastodon.social@youid @Mastodon Regarding verification of claims in my profile doc, here's how that objective is achieved via #HTTPS using a custom handshake.
Custom Handshake?
Credentials in my public profile doc are looked-up and matched to equivalents in my locally held #X509 cert, following completion of the conventional handshake.
#LinkInBio #Identity #Authenticity #SSI #YouID #NetID #WebID #Privacy #TLS
#https #x509 #linkinbio #identity #authenticity #ssi #youid #netid #webid #privacy #tls
Jürgen · @elbosso
97 followers · 3431 posts · Server mastodon.socialaaaahhh - ein guter tag: #rfc9130 https://www.rfc-editor.org/info/rfc9310 ist gerade verabschiedet und die https://github.com/elbosso/expect-dialog-ca kann bereits bei der erzeugung entsprechender CSRs unterstützen und konforme #x509 #certificates erstellen! näheres dazu bald auf https://elbosso.github.io/
David J. Bianco (He/Him) · @DavidJBianco
1009 followers · 153 posts · Server infosec.exchangeIn case you're having "that kind" of day, I just spent 10 minutes trying to figure out what the "/Q=" part of an #X509 distinguished name was supposed to be, before realizing my monitor was dusty.
YouID™ · @youid
4 followers · 8 posts · Server mastodon.socialHere's a #screencast that demonstrates the creation of verifiable credentials (#X509 cert and associated Private Key) using my #iOS edition on an #iPhone.
#screencast #x509 #iOS #iphone #ssi
Kingsley Uyi Idehen · @kidehen
401 followers · 821 posts · Server mastodon.socialMore #SMIME and #Email grief. Using the latest and greatest release of #OutLook on #macOS, I can no longer find the "Trust Center" module for setting the preferred #X509 cert to be used for digitally signing my emails. Basically, it just selects what it sees as the default from my collection -- magically :(
All of this when #Phishing via email remains the prevalent tool for tinkering with #privacy, #security, and #democracy by bad actors!
#smime #email #outlook #macos #x509 #phishing #privacy #security #democracy